ISRO CS 2014
Question 1 |
Consider a 33 MHz CPU based system. What is the number of wait states required if it is interfaced with a 60 ns memory? Assume a maximum of 10 ns delay for additional circuitry like buffering and decoding.
0 | |
1 | |
2 | |
3 |
Question 1 Explanation:
A wait state is a situation in which a computer program or processor is waiting for the completion of some event before resuming activity. A program or process in a wait state is inactive for the duration of the wait stat
When a computer processor works at a faster clock speed (expressed in MHz or millions of cycles per second) than the random access memory ( RAM ) that sends it instructions, it is set to go into a wait state for one or more clock cycles so that it is synchronized with RAM speed. In general, the more time a processor spends in wait states, the slower the performance of that processor.
From the given question, we will get total memory access time by combining access time and delay.
CPU frequency = 33 MHz
1 clock time = 1 / (33 MHz) = (1/33)*10-6 = 30.30 ns.
Total memory access time = 60 ns + 10 ns = 70 ns.
Total number of wait states = Total number of cycle needed
= Total memory access time / CPU frequency
=70 ns / (30.30 ns) = 2.31 (equivalent to 3 cycles)
When a computer processor works at a faster clock speed (expressed in MHz or millions of cycles per second) than the random access memory ( RAM ) that sends it instructions, it is set to go into a wait state for one or more clock cycles so that it is synchronized with RAM speed. In general, the more time a processor spends in wait states, the slower the performance of that processor.
From the given question, we will get total memory access time by combining access time and delay.
CPU frequency = 33 MHz
1 clock time = 1 / (33 MHz) = (1/33)*10-6 = 30.30 ns.
Total memory access time = 60 ns + 10 ns = 70 ns.
Total number of wait states = Total number of cycle needed
= Total memory access time / CPU frequency
=70 ns / (30.30 ns) = 2.31 (equivalent to 3 cycles)
Question 2 |
The number of states required by a Finite State Machine, to simulate the behavior of a computer with a memory capable of storing ‘m’ words, each of length ‘n’ bits is?
m x 2n | |
2m+n | |
2mn | |
m+n |
Question 2 Explanation:
A finite-state machine (FSM) an abstract machine that can be in exactly one of a finite number of states at any given time. The FSM can change from one state to another in response to some external inputs; the change from one state to another is called a transition.
Generally FSM consists of 2x states for a given input x.
But in the question, the input is specified number of words and length of each word.
For a given, ‘m’ words, each of length ‘n’ bits, so total number of bits are m*n
So, total number of states required by a Finite State Machine are 2mn.
Generally FSM consists of 2x states for a given input x.
But in the question, the input is specified number of words and length of each word.
For a given, ‘m’ words, each of length ‘n’ bits, so total number of bits are m*n
So, total number of states required by a Finite State Machine are 2mn.
Question 3 |
What is the output of the following C program?
#include<stdio.h>
#define SQR(x) (x*x)
int main()
{
int a;
int b=4;
a=SQR(b+2);
printf("%d\n",a);
return 0;
}
#include<stdio.h>
#define SQR(x) (x*x)
int main()
{
int a;
int b=4;
a=SQR(b+2);
printf("%d\n",a);
return 0;
}
14 | |
36 | |
18 | |
20 |
Question 3 Explanation:
In the question, SQR is macro which is preprocessor statement in c language.
Here macro takes one parameter also.
A macro is a fragment of code that is given a name. You can use that fragment of code in your program by using the name. For example,
#define SQR(x) (x*x)
Here, when we use SQR(x) in our program, it's replaced with (x*x)
The movement program control execute the macro, it will replace SQR(b+2) by (b+2*b+2)
The expression (b+2*b+2) consists of addition and multiplication operators.
Between two operators multiplication operator has highest priority later addition .
So the expression evaluation steps are as follows
a = (b + 2*b + 2)
=(4+2*4+2)// first multiplication
=(4+8+2) // addition equal priority , so it will evaluate left to right
=(12+2)
=14
Here macro takes one parameter also.
A macro is a fragment of code that is given a name. You can use that fragment of code in your program by using the name. For example,
#define SQR(x) (x*x)
Here, when we use SQR(x) in our program, it's replaced with (x*x)
The movement program control execute the macro, it will replace SQR(b+2) by (b+2*b+2)
The expression (b+2*b+2) consists of addition and multiplication operators.
Between two operators multiplication operator has highest priority later addition .
So the expression evaluation steps are as follows
a = (b + 2*b + 2)
=(4+2*4+2)// first multiplication
=(4+8+2) // addition equal priority , so it will evaluate left to right
=(12+2)
=14
Question 4 |
Consider the following pseudo code
while (m < n)
if (x > y ) and (a < b) then
a=a+1
y=y-1
end if
m=m+1
end while
What is cyclomatic complexity of the above pseudo code?
while (m < n)
if (x > y ) and (a < b) then
a=a+1
y=y-1
end if
m=m+1
end while
What is cyclomatic complexity of the above pseudo code?
2 | |
3 | |
4 | |
5 |
Question 4 Explanation:
Finding cyclomatic complexity using 3 formulas
1. E-V+2
2. P+1
3. No.of Regions
According to above code segment.
→ Edges-Vertices+2
= 8-6+2 = 4
→ Total number of regions = 4
→ Predicates+1 = 3+1 = 4
Note: We can use any one of above formulas.
1. E-V+2
2. P+1
3. No.of Regions
According to above code segment.
→ Edges-Vertices+2
= 8-6+2 = 4
→ Total number of regions = 4
→ Predicates+1 = 3+1 = 4
Note: We can use any one of above formulas.
Question 5 |
What is the number of steps required to derive the string ((() ()) ()) for the following grammar?
S → SS
S → (S)
S → ε
S → SS
S → (S)
S → ε
10 | |
15 | |
12 | |
16 |
Question 5 Explanation:
The required string consists of only only matched parenthesis enclosed with parentheses.
To generate the string ((() ()) ()) , we need to perform the steps sequentially.
As the string starts with left parentheses, we will start with the production S → (S).
Depending upon the string we will go for either left or right tree generation.
1) S → (S) // Replacing S by (S)
2) S → (SS) // Replacing by S by SS
3) S → ((S)S) //Replacing S by(S)
4) S → ((SS)S)// Replacing S by SS
5) S → (((S)S))S)
6) S → (((S)(S))S)
7) S → (((S)(S))(S)) [S → ε]
8) S → ((()(S))S) [S → ε]
9) S → ((()())S) [S → ε]
10) S → ((()()))
To generate the string ((() ()) ()) , we need to perform the steps sequentially.
As the string starts with left parentheses, we will start with the production S → (S).
Depending upon the string we will go for either left or right tree generation.
1) S → (S) // Replacing S by (S)
2) S → (SS) // Replacing by S by SS
3) S → ((S)S) //Replacing S by(S)
4) S → ((SS)S)// Replacing S by SS
5) S → (((S)S))S)
6) S → (((S)(S))S)
7) S → (((S)(S))(S)) [S → ε]
8) S → ((()(S))S) [S → ε]
9) S → ((()())S) [S → ε]
10) S → ((()()))
Question 6 |
The process of modifying IP address information in IP packet headers while in transit across a traffic routing device is called
Port address translation (PAT) | |
Network address translation (NAT) | |
Address mapping | |
Port mapping |
Question 6 Explanation:
Network address translation (NAT)
It is a method of remapping one IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.The technique was originally used as a shortcut to avoid the need to readdress every host when a network was moved. It has become a popular and essential tool in conserving global address space in the face of IPv4 address exhaustion. One Internet-routable IP address of a NAT gateway can be used for an entire private network.
Port Address Translation (PAT) is an extension to network address translation (NAT) that permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. The goal of PAT is to conserve IP addresses.
Address mapping (also know as pin mapping or geocoding) is the process of assigning map coordinate locations to addresses in a database. The output of address mapping is a point layer attributed with all of the data from the input database.
Port mapping or port forwarding is an application of network address translation (NAT) which redirects a communication request from one address and port number combination to another while the packets are traversing a network gateway, such as a router or firewall.
It is a method of remapping one IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.The technique was originally used as a shortcut to avoid the need to readdress every host when a network was moved. It has become a popular and essential tool in conserving global address space in the face of IPv4 address exhaustion. One Internet-routable IP address of a NAT gateway can be used for an entire private network.
Port Address Translation (PAT) is an extension to network address translation (NAT) that permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. The goal of PAT is to conserve IP addresses.
Address mapping (also know as pin mapping or geocoding) is the process of assigning map coordinate locations to addresses in a database. The output of address mapping is a point layer attributed with all of the data from the input database.
Port mapping or port forwarding is an application of network address translation (NAT) which redirects a communication request from one address and port number combination to another while the packets are traversing a network gateway, such as a router or firewall.
Question 7 |
What does a pixel mask mean?
string containing only 1’s | |
string containing only 0’s | |
string containing two 0’s | |
string containing 1’s and 0’s |
Question 7 Explanation:
Pixel mask: when a given image is intended to be placed over a background, the transparent areas can be specified through a binary mask.
→ This way, for each intended image there are actually two bitmaps:
1. Actual image, in which the unused areas are given a pixel value with all bits set to 0s.
2. Additional mask, in which the correspondent image areas are given a pixel value of all bits set to 0s and the surrounding areas a value of all bits set to 1s.
In the sample at right, black pixels have the all-zero bits and white pixels have the all-one bits.
→ This way, for each intended image there are actually two bitmaps:
1. Actual image, in which the unused areas are given a pixel value with all bits set to 0s.
2. Additional mask, in which the correspondent image areas are given a pixel value of all bits set to 0s and the surrounding areas a value of all bits set to 1s.
In the sample at right, black pixels have the all-zero bits and white pixels have the all-one bits.
Question 8 |
In the standard IEEE 754 single precision floating point representation, there is 1 bit for sign, 23 bits for fraction and 8 bits for exponent. What is the precision in terms of the number of decimal digits?
5 | |
6 | |
7 | |
8 |
Question 8 Explanation:
A floating-point variable can represent a wider range of numbers than a fixed-point variable of the same bit width at the cost of precision. A signed 32-bit integer variable has a maximum value of 231 − 1 = 2,147,483,647, whereas an IEEE 754 32-bit base-2 floating-point variable has a maximum value of (2 − 2−23) × 2127 ≈ 3.402823 × 1038.
In the IEEE 754-2008 standard, the 32-bit base-2 format is officially referred to as binary32; it was called single in IEEE 754-1985. IEEE 754 specifies additional floating-point types, such as 64-bit base-2 double precision and, more recently, base-10 representations.
We can convert the binary into decimal representation by using the following steps
let the number of digits in decimal digits be ‘x’
2-23 = 10-x
After taking log on both sides
log210-x =log2 2-23
-x log210 = -23log22 (The value of log22=1)
-3.322 x = -23 (The value of log210 = 3.321928)
x = 6.92
In the IEEE 754-2008 standard, the 32-bit base-2 format is officially referred to as binary32; it was called single in IEEE 754-1985. IEEE 754 specifies additional floating-point types, such as 64-bit base-2 double precision and, more recently, base-10 representations.
We can convert the binary into decimal representation by using the following steps
let the number of digits in decimal digits be ‘x’
2-23 = 10-x
After taking log on both sides
log210-x =log2 2-23
-x log210 = -23log22 (The value of log22=1)
-3.322 x = -23 (The value of log210 = 3.321928)
x = 6.92
Question 9 |
Let R be the radius of the circle. What is the angle subtended by an arc of length at the center of the circle?
1 degree | |
1 radian | |
90 degrees | |
π radians |
Question 9 Explanation:
A degree (in full, a degree of arc, arc degree, or arc degree), usually denoted by ° (the degree symbol), is a measurement of a plane angle, defined so that a full rotation is 360 degrees.
It is not an SI unit, as the SI unit of angular measure is the radian, but it is mentioned in the SI brochure as an accepted unit.Because a full rotation equals 2π radians.
The radian (SI symbol rad) is the SI unit for measuring angles, and is the standard unit of angular measure used in many areas of mathematics. The length of an arc of a unit circle is numerically equal to the measurement in radians of the angle that it subtends;
It is not an SI unit, as the SI unit of angular measure is the radian, but it is mentioned in the SI brochure as an accepted unit.Because a full rotation equals 2π radians.
The radian (SI symbol rad) is the SI unit for measuring angles, and is the standard unit of angular measure used in many areas of mathematics. The length of an arc of a unit circle is numerically equal to the measurement in radians of the angle that it subtends;
Question 10 |
The number of logical CPUs in a computer having two physical quad-core chips with hyperthreading enabled is
1 | |
2 | |
8 | |
16 |
Question 10 Explanation:
There is only one processor chip. That chip can have one, two, four, six, or eight cores.
Currently, an 18-core processor is the best you can get in consumer PCs.
Each “core” is the part of the chip that does the processing work. Essentially, each core is a central processing unit (CPU).
From the given information , there are two quad core chips are available
So, total number of physical CPUs = 2*4 = 8
Each CPU has two logical CPU in hyper threading
So, 8 physical CPU have 2*8 = 16 logical CPU.
Currently, an 18-core processor is the best you can get in consumer PCs.
Each “core” is the part of the chip that does the processing work. Essentially, each core is a central processing unit (CPU).
From the given information , there are two quad core chips are available
So, total number of physical CPUs = 2*4 = 8
Each CPU has two logical CPU in hyper threading
So, 8 physical CPU have 2*8 = 16 logical CPU.
Question 11 |
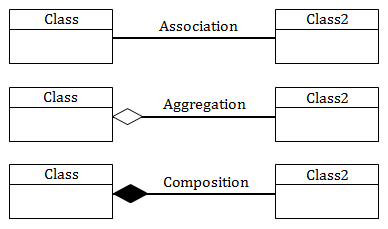
An aggregation, the association is drawn using which symbol?
A line which loops back on to the same table | |
A small open diamond at the end of a line connecting two tables | |
A small closed diamond at the end of a line connecting two tables | |
A small closed triangle at the end of a line connecting two tables |
Question 11 Explanation:
Association: Relationship between 2 objects. It defines the multiplicity between objects like 1-1, 1-many, many-1, many to many.
Aggregation: A directional between objects. When an object “has-a” another object, then you have got an aggregation between them, you have got an aggregation between them. Direction between them specified which object contains the other object.

Aggregation: A directional between objects. When an object “has-a” another object, then you have got an aggregation between them, you have got an aggregation between them. Direction between them specified which object contains the other object.
Question 12 |
How many states are there in a minimum state deterministic finite automaton accepting the language L = {w | w {0,1} number of 0’s is divisible by 2 and number of 1’s is divisible by 5, respectively} ?
7 | |
9 | |
10 | |
11 |
Question 12 Explanation:
From the given data
String which consists of 0’s and 1’s
Language is number of 0’s is divisible by 2 and number of 1’s is divisible by 5
Machine is minimum state deterministic finite automaton
The set of strings generated by {0,1} are ={ε,0,1,00,11,01,10,000,011,010 .. and so on}
The strings which are generated by language which is specified in the questions are
{ ε , 00, 11111, 0011111, 0011111 , 1111100, 1010111 , 000011111,….and so on }
So, strings accepted by the automaton have to be of length 0, 2, 4, 5, 6, 7, 8, 9, 10, 11, 14, 12….and so on, i.e. equation for length will be 2x + 5y (where x,y>=0 )
Number of 0’s divisible by 2 means , the possible remainders are 0 and 1 i.e; 2
Number of 1’s divisible by 5 means , the possible remainders are 4,3,2,1,0 i.e; 5
Total number of states are 2*5 =10
String which consists of 0’s and 1’s
Language is number of 0’s is divisible by 2 and number of 1’s is divisible by 5
Machine is minimum state deterministic finite automaton
The set of strings generated by {0,1} are ={ε,0,1,00,11,01,10,000,011,010 .. and so on}
The strings which are generated by language which is specified in the questions are
{ ε , 00, 11111, 0011111, 0011111 , 1111100, 1010111 , 000011111,….and so on }
So, strings accepted by the automaton have to be of length 0, 2, 4, 5, 6, 7, 8, 9, 10, 11, 14, 12….and so on, i.e. equation for length will be 2x + 5y (where x,y>=0 )
Number of 0’s divisible by 2 means , the possible remainders are 0 and 1 i.e; 2
Number of 1’s divisible by 5 means , the possible remainders are 4,3,2,1,0 i.e; 5
Total number of states are 2*5 =10
Question 13 |
Which of the following is true with respect to Reference?
A reference can never be NULL | |
A reference needs an explicit dereferencing mechanism | |
A reference can be reassigned after it is established | |
A reference and pointer are synonymous |
Question 13 Explanation:
In the C++ programming language, a reference is a simple reference data type that is less powerful but safer than the pointer type inherited from C. A reference is a general concept datatype, with pointers and C++ references being specific reference data type implementations.
We can assign NULL to pointers where as we can’t assign NULL to references.
We can re-assign pointers as many as number of times where a reference can never be re-assigned once it is established.
We can assign NULL to pointers where as we can’t assign NULL to references.
We can re-assign pointers as many as number of times where a reference can never be re-assigned once it is established.
Question 14 |
There are 200 tracks on a disc platter and the pending requests have come in the order – 36, 69, 167, 76, 42, 51, 126, 12 and 199. Assume the arm is located at the 100 track and moving towards track 199. If the sequence of disc access is 126, 167, 199, 12, 36, 42, 51, 69 and 76 then which disc access scheduling policy is used?
Elevator | |
Shortest seek-time first | |
C-SCAN | |
First Come First Served |
Question 14 Explanation:
Total tracks are :200
Tracks order is 36, 69, 167, 76, 42, 51, 126, 12 and 199
Track position is at 100 and moving towards 199.
sequence of disc access is 126, 167, 199, 12, 36, 42, 51, 69 and 76
From the above sequence , we can observe that disc moving from 100 to 126 from there to moving right side direction until last disc 199
From the last disc(199) to first disc(12) and from there to next disc(36) and so on.
C-SCAN sweeps the disk from end-to-end, but as soon it reaches one of the end tracks it then moves to the other end track without servicing any requesting location. As soon as it reaches the other end track it then starts servicing and grants requests headed to its direction
Tracks order is 36, 69, 167, 76, 42, 51, 126, 12 and 199
Track position is at 100 and moving towards 199.
sequence of disc access is 126, 167, 199, 12, 36, 42, 51, 69 and 76
From the above sequence , we can observe that disc moving from 100 to 126 from there to moving right side direction until last disc 199
From the last disc(199) to first disc(12) and from there to next disc(36) and so on.
C-SCAN sweeps the disk from end-to-end, but as soon it reaches one of the end tracks it then moves to the other end track without servicing any requesting location. As soon as it reaches the other end track it then starts servicing and grants requests headed to its direction
Question 15 |
Consider the logic circuit given below:

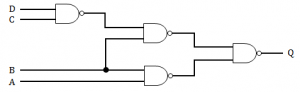
A’C + BC ‘ + CD | |
ABC + C’D | |
AB + BC’ + BD’ | |
AB’ + AC’ + C’D |
Question 15 Explanation:
Q = (((CD)’B)'(AB)’)’
Q = ((CD)’B)” + (AB)”
Q = (CD)’B + AB
Q = (C’ + D’)B + AB
Q = C’B + D’B + AB
Q = AB + BC’ + BD’
Q = ((CD)’B)” + (AB)”
Q = (CD)’B + AB
Q = (C’ + D’)B + AB
Q = C’B + D’B + AB
Q = AB + BC’ + BD’
Question 16 |
What is routing algorithm used by OSPF routing protocol?
Distance vector | |
Flooding | |
Path vector | |
Link state |
Question 16 Explanation:
→ Open Shortest Path First (OSPF) is a routing protocol for Internet Protocol (IP) networks.
→ It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS).
→ It implements Dijkstra's algorithm, also known as the shortest path first (SPF) algorithm.
→ It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS).
→ It implements Dijkstra's algorithm, also known as the shortest path first (SPF) algorithm.
Question 17 |
If each address space represents one byte of storage space, how many address lines are needed to access RAM chips arranged in a 4 x 6 array, where each chip is 8K x 4 bits ?
13 | |
15 | |
16 | |
17 |
Question 17 Explanation:
From the given data
Each chip size is = 8K x 4 bits = 23 x 210 x 22 == 215 bits = 212 bits
Given chip array = 6 x 4 = 24 ( 24=16 and 25=32)
So the number bits required for the total chips are 5 bits.
So, total number of bits required = 12 + 5 = 17 bits
Each chip size is = 8K x 4 bits = 23 x 210 x 22 == 215 bits = 212 bits
Given chip array = 6 x 4 = 24 ( 24=16 and 25=32)
So the number bits required for the total chips are 5 bits.
So, total number of bits required = 12 + 5 = 17 bits
Question 18 |
Consider the following segment table in the segmentation scheme:

What happens if the logical address requested is Segment ID 2 and offset 1000?
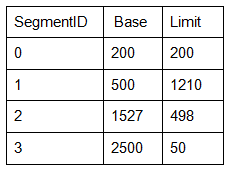
What happens if the logical address requested is Segment ID 2 and offset 1000?
Fetches the entry at the physical address 2527 for segment Id2 | |
A trap is generated | |
Deadlock | |
Fetches the entry at offset 27 in Segment Id 3 |
Question 18 Explanation:
From the question we need to find the logical address for segment id-2.
From given table,
Segment-2 has a base address = 1527 ‘
limit address = 498.
Process can access memory from the location 1527 to 2025(1527+498)
If the process tries to access the memory with offset 1000 then a segmentation fault trap will be generated.
In computing and operating systems, a trap, also known as an exception or a fault, is typically a type of synchronous interrupt caused by an exceptional condition (e.g., breakpoint, division by zero, invalid memory access)
From given table,
Segment-2 has a base address = 1527 ‘
limit address = 498.
Process can access memory from the location 1527 to 2025(1527+498)
If the process tries to access the memory with offset 1000 then a segmentation fault trap will be generated.
In computing and operating systems, a trap, also known as an exception or a fault, is typically a type of synchronous interrupt caused by an exceptional condition (e.g., breakpoint, division by zero, invalid memory access)
Question 19 |
The number of bit strings of length 8 that will either start with 1 or end with 00 is?
32 | |
128 | |
160 | |
192 |
Question 19 Explanation:
→ Number of bit strings of length 8 that start with 1: 27 = 128.
→ Number of bit strings of length 8 that end with 00: 26 = 64.
→ Number of bit strings of length 8 that start with 1 and end with 00: 25 = 32.
→ Applying the subtraction rule, the number is 128+64−32 = 160
→ Number of bit strings of length 8 that end with 00: 26 = 64.
→ Number of bit strings of length 8 that start with 1 and end with 00: 25 = 32.
→ Applying the subtraction rule, the number is 128+64−32 = 160
Question 20 |
Which of the following is not a maturity level as per the Capability Maturity Model?
Initial | |
Measurable | |
Repeatable | |
Optimized |
Question 20 Explanation:
Capability Maturity Model levels
1. Initial
2. Repeatable
3. Defined
4. Managed
5. Optimized
1. Initial
2. Repeatable
3. Defined
4. Managed
5. Optimized
There are 20 questions to complete.
