ISRO CS-2023
Question 1 |
Consider the context-free grammar G below for arithmetic expressions :
E->E+E|E*E|id
Which of the following statements is TRUE:
E->E+E|E*E|id
Which of the following statements is TRUE:
The string "id + id x id" has no parse tree according to G
| |
The string "id + id x id" has only one parse tree according to G
| |
The string "id + id x id" has exactly two parse trees according to G
| |
The string "id + id x id" has more than two parse trees according to G |
Question 2 |
Which of the following heap memory allocation strategies is likely to exploit spatial locality of memory accesses in a program, the most?
Best Fit
| |
First Fit
| |
Next Fit
| |
Last Fit |
Question 3 |
Which of the following is true?
Both Parity and Cyclic Redundancy Check are error correcting codes
| |
Both Parity and Low Density Parity Check Code are error correcting codes
| |
Both Reed-Solomon code and Low Density Parity Check Code are error correcting codes
| |
Both Cyclic Redundancy Check and Low Density Parity Check Code are error correcting codes |
Question 3 Explanation:
Reed-Solomon Code: Reed-Solomon codes are widely used error-correcting codes, especially in applications where burst errors are common, such as in data storage systems (CDs, DVDs, QR codes, etc.). They can correct multiple errors and are known for their effectiveness in dealing with errors in communication.
Low Density Parity Check Code (LDPC): LDPC codes are also error-correcting codes. LDPC codes have gained popularity, especially in modern communication systems, for their capacity to approach the Shannon limit for channel capacity.
Low Density Parity Check Code (LDPC): LDPC codes are also error-correcting codes. LDPC codes have gained popularity, especially in modern communication systems, for their capacity to approach the Shannon limit for channel capacity.
Question 4 |
In Reverse Polish notation, expression A*B+C*D is written as
AB*CD*+
| |
A*BCD*+
| |
AB*CD+*
| |
A*B*CD+ |
Question 4 Explanation:
Reverse Polish Notation (RPN), also known as postfix notation, operators come after their operands.
A*B translates to AB*
C*D translates to CD*
Finally, the + operator is placed after AB* and CD*.
A*B translates to AB*
C*D translates to CD*
Finally, the + operator is placed after AB* and CD*.
Question 5 |
In a vectored interrupt
The branch address is assigned to a fixed location in memory
| |
The interrupting source supplies the branch information to the processor
| |
The branch address is obtained from a register in the processor
| |
None of the above |
Question 5 Explanation:
In a vectored interrupt, each interrupting device or source is assigned a specific vector address.
When an interrupt occurs, the interrupting device sends its vector address to the processor.
The processor uses this vector address to locate the corresponding interrupt service routine (ISR) or branch address.
This allows the processor to directly jump to the specific routine associated with the interrupting device
Question 6 |
Worst case time complexity of heap sort for n elements
O(nlogn)
| |
O(logn)
| |
O(n2)
| |
O(n) |
Question 6 Explanation:
Heap Sort has a time complexity of O(n log n) in the worst case because it builds a max-heap or min-heap (depending on whether it's sorting in ascending or descending order) and performs n iterations (heapify) for n elements.
Each heapify operation takes O(log n) time in the worst case.
Each heapify operation takes O(log n) time in the worst case.
Question 7 |
Consider a database table T containing two columns X and Y each of type Integer. After the creation of the table, one record (X=l, Y=l) is inserted in the table. Let MX and MY denote the respective maximum values of X and Y among all records in the table at any point in time. Using MX and MY, new records are inserted in the table 128 times with X and Y values being MX+I, 2 x MY+I respectively. It may be noted that each time after the insertion, values of MX and MY change. What will be the output of the following SQL query after the steps mentioned above are
carried out?
SELECT Y FROM T WHERE X=7;
SELECT Y FROM T WHERE X=7;
127 | |
15 | |
129 | |
257 |
Question 8 |
A full adder circuit requires
two inputs and two outputs
| |
two inputs and three outputs
| |
three inputs and two outputs
| |
three inputs and one output |
Question 8 Explanation:
A full adder is a digital circuit that adds three binary inputs: A, B, and Cin (carry-in).
It produces two outputs: Sum (S) and Carry-out (Cout).
The sum output (S) is the result of the addition of A, B, and Cin.
The carry-out (Cout) represents the carry that is generated when adding A, B, and Cin.
Question 9 |
The logical operation of the following circuit is

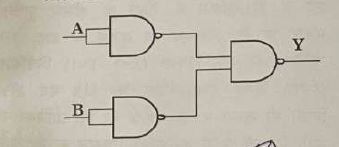
XOR
| |
NAND | |
AND | |
OR |
Question 10 |
A logic circuit that provides a LOW output when both inputs are HIGH or both inputs are LOW is
AND
| |
NAND
| |
XNOR
| |
XOR |
Question 10 Explanation:
The XNOR (exclusive-NOR) gate produces a LOW output when both inputs are the same (both HIGH or both LOW).
Question 11 |
Which of the following multithreading model is followed in Linux OS?
One User Thread mapping to One Kernel Thread
| |
Many User Threads mapping to One Kernel Thread
| |
One User Th read mapping to Many Kernel Threads
| |
Many User Threads mapping to Many Kernel Threads |
Question 12 |
Purpose of priority inheritance protocol in synchronization mechanisms is
To prevent priority inversion in systems having two or lesser priorities for a resource
| |
To provide mutual exclusion between threads and prevent data corruption
| |
To prevent priority inversion and ensure fairness in resource allocation | |
To allow multiple threads to access any resource simultaneously
|
Question 13 |
Consider the deterministic finite-state automaton (DEA) below. The alphabet is {a,b}. The state with a small incoming arrow is the initial state, while the double circle state denotes a final state.

Which of the following regular expressions defines the language accepted by the DFA?
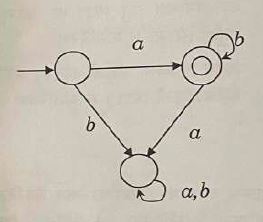
Which of the following regular expressions defines the language accepted by the DFA?
ab*
| |
a*b*
| |
(ab)*
| |
a*b |
Question 14 |
Which of the following scenario may not be a good for HDFS in Big data paradigm?
HDFS is not suitable for scenarios requiring multiple/simultaneous writes to the same file
| |
HDFS is suitable for storing data related to applications requiring low latency data access
| |
HDFS is suitable for storing data related to applications requiring high latency data access
| |
None of the above |
Question 15 |
A standard Java API for monitoring and managing applications is
JVM
| |
JVN
| |
JMX
| |
JMY |
Question 16 |
Which of the following clustering technique is used by K- Means Algorithm:
Hierarchical Technique
| |
Partitional technique
| |
Divisive | |
Agglomerative |
Question 17 |
Match the following in the context of Information Security which are closely associated
| (i) Ingress filtering | (P) Data leakage prevention |
| (ii) Egress filtering | (Q) Hiding identity of systems |
| (iii) NAT | (R) Keep track of TCP/IP connections |
| (iv) Stateful firewall | S) Malicious traffic prevention |
(i)-(S),(ii)-(P),(iii)-(Q),(iv)-(R)
| |
(i)-(P),(ii)-(R),(iii)-(S),(iv)-(Q)
| |
(i)-(S),(ii)-(R),(iii)-(P),(iv)-(Q)
| |
(i)-(R),(ii)-(Q),(iii)-(S),(iv)-(P) |
Question 18 |
Asymmetric encryption is not suitable for
Confidentiality
| |
Authentication
| |
Key Exchange
| |
Prevention of Denial of Service |
Question 19 |
Find the minimum spanning distance and the corresponding number of edges for the following graph

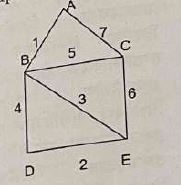
10,3
| |
11,4
| |
15,4
| |
28,7 |
Question 20 |
Match the following
(A) Floyd Warshall i) shortest path between two vertices
(B) Dijkstra ii)single source shortest path
(C) Kruskal's iii)Minimum spanning tree
(D) Bellman ford iv)solving all pair shortest path
(A) Floyd Warshall i) shortest path between two vertices
(B) Dijkstra ii)single source shortest path
(C) Kruskal's iii)Minimum spanning tree
(D) Bellman ford iv)solving all pair shortest path
(A)-(iii),(B)-(i),(C)-(iv),(D)-(i)
| |
(A)-(iv),(B)-(i),(C)-(iii),(D)-(ii)
| |
(A)-(i),(B)-(ii),(C)-(iii),(D)-(iv)
| |
(A)-(ii),(B)-(iii),(C)-(i),(D)-(iv) |
There are 20 questions to complete.
