ict
Question 1 |
A type of memory that holds the computer startup routine is
A | Cache |
B | RAM
|
C | DRAM |
D | ROM |
Question 1 Explanation:
The invention of read-only memory (ROM) of various types solved this paradox by allowing computers to be shipped with a startup program that could not be erased. Growth in the capacity of ROM has allowed ever more elaborate start up procedures to be implemented
Question 2 |
Match List I with List II:
List I List II
A) Input (I) Mouse
B) Output (II) Monitor
C) Memory (III) Cache
D) Software (IV) Python
Choose the correct answer from the options given below:
List I List II
A) Input (I) Mouse
B) Output (II) Monitor
C) Memory (III) Cache
D) Software (IV) Python
Choose the correct answer from the options given below:
A | (A)-(I), (B)-(II), (C)-(IV), (D)-(III)
|
B | (A)-(I), (B)-(III), (C)-(II), (D)-(IV)
|
C | (A)-(III), (B)-(II), (C)-(I), (D)-(IV)
|
D | (A)-(I), (B)-(II), (C)-(III), (D)-(IV)
|
Question 2 Explanation:
Input device → Mouse
Output device → Monitor
Memory → Cache
Software → Python
Output device → Monitor
Memory → Cache
Software → Python
Question 3 |
The word blog is derived from the word
A | My log
|
B | We blog |
C | E blog |
D | Blogger |
Question 3 Explanation:
A blog (a truncation of "weblog") is a discussion or informational website published on the World Wide Web consisting of discrete, often informal diary-style text entries (posts). Posts are typically displayed in reverse chronological order, so that the most recent post appears first, at the top of the web page.
Question 4 |
Cloud computing has the following distinct characteristics:
A) The service is hosted on the internet.
B) It is made available by a service provider.
C) It computes and predicts rain when the weather is cloudy.
D) The service is fully managed by the provider.
Choose the correct answer from the options given below:
A) The service is hosted on the internet.
B) It is made available by a service provider.
C) It computes and predicts rain when the weather is cloudy.
D) The service is fully managed by the provider.
Choose the correct answer from the options given below:
A | (A), (B) only
|
B | (A), (B), (C) only
|
C | (A), (D) only |
D | (A), (B), (D) only
|
Question 5 |
A firewall is a software tool that protects
A) Server
B) Network
C) Fire
D) Individual Computer
Choose the correct answer from the options given below:
A) Server
B) Network
C) Fire
D) Individual Computer
Choose the correct answer from the options given below:
A | (A), (C) only |
B | (B), (C) only |
C | (A), (B), (C) only |
D | (A), (B), (D) only |
Question 5 Explanation:
A firewall is a software tool that protects Server, Network and Individual Computer.
Question 6 |
Which tool is used to create online bulletin board where you can display information in the form of pictures, texts, videos etc.?
A | Quizzizz |
B | Padlet |
C | Screen Castify |
D | Windows |
Question 7 |
Which of the following are example of Asynchronous communication?
A. Blog
B. Podcast
C. Electronic Mail
D. Discussion Forum
E. Phone calls
Choose the most appropriate answer from the options given below:
A. Blog
B. Podcast
C. Electronic Mail
D. Discussion Forum
E. Phone calls
Choose the most appropriate answer from the options given below:
A | B and E only |
B | C, D and E only |
C | A, C and D only |
D | A, B, C and D only |
Question 8 |
The hardware address of a computer network device consists of 48 bits. Which of the following is a valid address in hexadecimal numbers?
A | 00E0071944A0 |
B | 0A23B5 |
C | 1E07FG124372 |
D | 398A7E9412110408 |
Question 9 |
The computer uses a bootstrap. Which of the following shows the part of a computer of which the bootstrap is an example?
A | Application software |
B | Firmware |
C | Hard disk drive |
D | IP address |
Question 10 |
Given below are tow statements:
Statement I: One always uses CD-ROMs to save data
Statement II: A computer has 2048 MB of RAM. That means computer has 1.2 GB of RAM.
In the light of the above statements, choose the correct answer from the options given below:
Statement I: One always uses CD-ROMs to save data
Statement II: A computer has 2048 MB of RAM. That means computer has 1.2 GB of RAM.
In the light of the above statements, choose the correct answer from the options given below:
A | Both Statement I and Statement II are true. |
B | Both Statement I and Statement II are false. |
C | Statement I is true and Statement II is false. |
D | Statement I is false and Statement II is true. |
Question 11 |
Which file formats are used to store music files?
A.bmp
B.wav
C.mp3
D.htm
E.wma
Choose the correct answer from the options given below:
A.bmp
B.wav
C.mp3
D.htm
E.wma
Choose the correct answer from the options given below:
A | A, B and D only |
B | A, D and E only |
C | B, C and D only |
D | B, C and E only |
Question 12 |

Choose the correct answer from the options given below:
A | A-I, B-II, C-III, D-IV |
B | A-IV, B-II, C-III, D-I |
C | A-II, B-IV, C-I, D-III |
D | A-IV, B-III, C-II, D-I |
Question 13 |
Which of the following is an example of IEEE 802.3?
A |
LAN |
B | MAN
|
C | WAN
|
D | PAN |
Question 14 |
Which of the following technologies is used in the second generation of computers?
A |
Vacuum tubes |
B | Transistors |
C | Integrated circuits |
D | VLSI
|
Question 15 |
Which of the following is the correct sequence of increasing access time of storage/memory devices?
A. Magnetic tape
B. RAM
C. Cache memory
D. Hard disk
E. Registers
A. Magnetic tape
B. RAM
C. Cache memory
D. Hard disk
E. Registers
A | A, B, C, D, E
|
B | B, E, C, A, D
|
C |
E, C, B, D, A |
D | C, E, B, A, D |
Question 16 |
With reference to cyber-attacks, which of the following statements are correct?
A. Malware is a malicious software designed to cause damage to a single computer, server, or computer network.
B. Types of malware include computer viruses, worms, Trojan horses, ransomware, and spyware.
C. Pegasus is a malicious software classified as ransomware.
D. India is not a signatory to the Budapest Convention on cybercrime.
Choose the most appropriate answer from the options given below :
A. Malware is a malicious software designed to cause damage to a single computer, server, or computer network.
B. Types of malware include computer viruses, worms, Trojan horses, ransomware, and spyware.
C. Pegasus is a malicious software classified as ransomware.
D. India is not a signatory to the Budapest Convention on cybercrime.
Choose the most appropriate answer from the options given below :
A | A, B and C only
|
B | B, C and D only |
C | A, B, C and D
|
D | A, B and D only
|
Question 17 |
Match List – I with List – II
Choose the correct answer from the options given below
| List I (Operating System) | List II (Task) |
| A. UNIX | I. Assist users in system maintenance tasks |
| B. MS-DOS | II. Mobile device |
| C. Android OS | III. Single-user operating system |
| D. Utility Programs | IV. Multi-user operating system |
Choose the correct answer from the options given below
A | A-III, B-IV, C-I, D-II
|
B | A-I, B-II, C-IV, D-III
|
C |
A-IV, B-III, C-II, D-I |
D |
A-III, B-I, C-II, D-IV
|
Question 18 |
Android is a mobile operating system developed by
A | IBM |
B | Apple |
C | Microsoft |
D | Google |
Question 19 |
Which of the following statements A - D are true with reference to high-level computer
programming languages?
A. These need to be translated into machine code in order to run on a computer.
B. These are written using mnemonic codes-
C. These are specific to the computer's hardware.
D. These are portable languages.
Choose the correct answer from the options given below:
A. These need to be translated into machine code in order to run on a computer.
B. These are written using mnemonic codes-
C. These are specific to the computer's hardware.
D. These are portable languages.
Choose the correct answer from the options given below:
A | B and C only |
B | A and B Only |
C | A and D Only |
D | C and D Only |
Question 20 |
Which of the following is an independent malicious program that propagates itself across a
network by exploiting security flaws in widely-used services?
A | Computer Worm |
B | Computer Virus |
C | Trojan Horse |
D | Logic Bomb |
Question 21 |
Match the LIST-I with LIST-II
Choose the correct answer from the options given below:
| LIST-I(Question) | LIST-II(Answer) | ||
| A | The speed of a CPU is measured in ____ | I | Inches |
| B | Storage capacity of data is measured in ___ | II | Hertz |
| C | Network bandwidth is measured in ____ | III | bits per second |
| D | Size of a computer monitor is measured in ___ diagonally from corner to the opposite corner. | IV | Bytes |
Choose the correct answer from the options given below:
A | A-I, B-III, C-IV, D-II |
B | A-III, B-II, C-I, D-lV |
C | A-IV, B-I, C-II, D-III |
D | A-II, B-lV, C-III, D-l |
Question 22 |
Match List-I with List-II
List-I List-II
(Internet Term) (Description)
A)Blogs (I) Allows users to create and edit web pages using a browser
B)Podcasts (II) A type of bookmarking where a user “marks” a webpage or photo using text to describe its contents
C)Tagging (III) A series of digital media files
D)Wikis (IV) Personal internet journals,br> Choose the correct answer from the options given below:
List-I List-II
(Internet Term) (Description)
A)Blogs (I) Allows users to create and edit web pages using a browser
B)Podcasts (II) A type of bookmarking where a user “marks” a webpage or photo using text to describe its contents
C)Tagging (III) A series of digital media files
D)Wikis (IV) Personal internet journals,br> Choose the correct answer from the options given below:
A | (A)-(I), (B)-(II) , (C)-(III),(D)-(IV)
|
B | (A)-(III), (B)-(IV) , (C)-(II),(D)-(I) |
C | (A)-(IV), (B)-(III) , (C)-(II),(D)-(I) |
D | (A)-(II), (B)-(III) , (C)-(IV),(D)-(I) |
Question 23 |
Identify the correct order of the following major technological changes A-D in the development of computers based on the first to fourth generation of the computers :
A)Transistors
B)Microprocessor
C)Vacuum tubes
D)Integrated circuits
choose the correct answer from the options given below :
A)Transistors
B)Microprocessor
C)Vacuum tubes
D)Integrated circuits
choose the correct answer from the options given below :
A | (A),(C),(D),(B)
|
B | (B),(A),(C),(D) |
C | (D),(A),(C),(B) |
D | (C),(A),(D),(B) |
Question 24 |
If (L)M represents a number L in base-M number system, then what will be the value of (107)8 + (257)16?
A | (762)10
|
B | (862)10
|
C | (962)10 |
D | (662)10 |
Question 25 |
To record voice narration for your Microsoft PowerPoint presentation, your computer must have :
A)Sound card
B)An internet connection
C)Speakers
D)An external video port
E)Microphone
Choose the correct answer from the options give below :
A)Sound card
B)An internet connection
C)Speakers
D)An external video port
E)Microphone
Choose the correct answer from the options give below :
A | (A),(C) and (E) only
|
B | (B) and (D) only
|
C | (A) and (E) only |
D | (B),(C) and (D) only
|
Question 26 |
In computer networking , an Ip version-6 is ____________times larger than an IP version-4 address.
A | 2 |
B | 4 |
C | 6 |
D | 8 |
Question 26 Explanation:
The IPv4 is a 32-bit address, whereas IPv6 is a 128-bit hexadecimal address.
Question 27 |
Given below are two statements : One is labelled as Assertion A and the other is labelled as Reason R.
Assertion (A) : Discussion forums are one of the Four Quadrants for MOOC.
Reasons (R) : Discussion forums are in-built feature Of learning management systems (LMS).
In the light of the above statements, choose the most appropriate answer from the options given below
Assertion (A) : Discussion forums are one of the Four Quadrants for MOOC.
Reasons (R) : Discussion forums are in-built feature Of learning management systems (LMS).
In the light of the above statements, choose the most appropriate answer from the options given below
A | Both (A) and (R) are correct and (R) is the correct explanation of (A)
|
B | Both (A) and (R) are correct but (R) is NOT the correct explanation of (A) |
C | (A) is correct but (R) is not correct (A) |
D | (A) is not correct but (R) is correct (A) |
Question 28 |
Which of the following statements are correct regarding CERT-IN?
A) CERT-IN is the national nodal agency for responding to computer security incidents as and when they occur
B) CERT-IN is operational since January 2014
C) forecast and alert of cyber security incidents is one of the functions of CERT-IN
Choose the correct answer from the options given below:
A) CERT-IN is the national nodal agency for responding to computer security incidents as and when they occur
B) CERT-IN is operational since January 2014
C) forecast and alert of cyber security incidents is one of the functions of CERT-IN
Choose the correct answer from the options given below:
A | A,B,C |
B | A and B only |
C | A and C only |
D | B and C only
|
Question 29 |
Given below are two statements:
Statement I: Cache memory is volatile memory and is much slower than Random Access Memory(RAM)
Statement II: CDs,DVDs and Magnetic Tapes are all optical media devices
In the light of the above statements. choose the correct answer from the options given below
Statement I: Cache memory is volatile memory and is much slower than Random Access Memory(RAM)
Statement II: CDs,DVDs and Magnetic Tapes are all optical media devices
In the light of the above statements. choose the correct answer from the options given below
A | Both Statement I and Statement II are true
|
B | Both Statement I and Statement II are false
|
C | Statement I is true but Statement II is false
|
D | Statement I is false but Statement II is true |
Question 30 |
Consider the following worksheet:
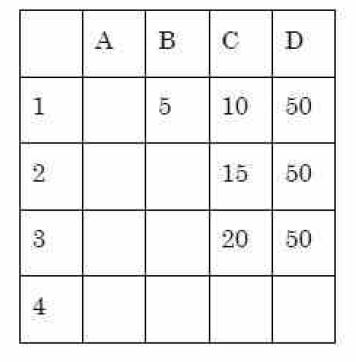
Which of the following formula should be entered into the cell D1 so that when it is copied into the cells D2 and D3, it gives the correct values as shown in the range D1:D3?

Which of the following formula should be entered into the cell D1 so that when it is copied into the cells D2 and D3, it gives the correct values as shown in the range D1:D3?
A | B1*$C$1
|
B | $B$1*C1
|
C | B1*C1
|
D | $B$1*$C$1 |
Question 31 |
Which of the following three numbers (A-C) in decimal, octal and hexadecimal notations respectively, is/are equivalent to (11011001)2 in binary notation?
(A (217)10
(B) (661)8
(C) (D9)16
Choose the correct answer from the options given below :
(A (217)10
(B) (661)8
(C) (D9)16
Choose the correct answer from the options given below :
A | A only
|
B | B only
|
C | A and B only
|
D | A and C only |
Question 32 |
Which Indian Act makes it illegal to knowingly spread a computer virus
A | Data Protection and Security Act,1997
|
B | Information Security Act,1998
|
C | Information Technology Act,2000
|
D | Computer Misuse and Cyber Act,2009 |
Question 33 |
Recording a television programme on a VCR is an example of :
A | time-shifting |
B | content reference |
C | mechanical clarity |
D | media synchronisation |
Question 34 |
The largest number of newspapers in India is published from the state of :
A | Kerala |
B | Maharashtra |
C | West Bengal |
D | Uttar Pradesh |
Question 35 |
Line access and avoidance of collision are the main functions of :
A | the CPU |
B | the monitor |
C | network protocols |
D | wide area networks |
Question 35 Explanation:
Subaltern:- of lower status.
→ which implies inequality
→ which implies inequality
Question 36 |
In the hypermedia database, information bits are stored in the form of :
A | signals |
B | cubes |
C | nodes |
D | symbols |
Question 36 Explanation:
The premises of a valid deductive argument provide conclusive evidence for its conclusion.
Question 37 |
Communications bandwidth that has the highest capacity and is used by microwave, cable and fibre optics lines is known as :
A | hyper-link |
B | broadband |
C | bus width |
D | carrier wave |
Question 38 |
An electronic bill board that has a short text or graphical advertising message is referred to as :
A | bulletin |
B | strap |
C | bridge line |
D | banner |
Question 39 |
Which of the following is not the characteristic of a computer ?
A | computer is an electrical machine |
B | computer cannot think at its own |
C | computer processes information error free |
D | computer can hold data for any length of time |
Question 40 |
What is the name of a webpage address?
A | Directory |
B | Protocol |
C | URL |
D | Domain |
Question 41 |
Which of the following represents billion characters?
A | Megabytes |
B | Kilobytes |
C | Gigabytes |
D | Terabytes |
Question 42 |
Which of the following domains is used for – profit businesses?
A | . net |
B | . edu |
C | . com |
D | . org |
Question 43 |
The data storage hierarchy consists of:
A | Bits, bytes, fields, records, files and databases |
B | Bits, bytes, records, fields, files and databases |
C | Bits, bytes, fields, files, records and databases |
D | Bytes, bits, fields, records, files and databases |
Question 44 |
What is the full form of USB as used in computer related activities?
A | Universal Security Block |
B | Universal Serial Bus |
C | United Serial Bus |
D | Ultra Security Block |
Question 45 |
Which of the following statement(s) regarding the term ICT is/are true?
P: A digital divide is an economic and social equality with regard to access to, use of, or impact of ICT.
Q: ICT helps in international development by bridging the digital divide and providing equitable access to technologies.
Choose the correct answer from the following:
P: A digital divide is an economic and social equality with regard to access to, use of, or impact of ICT.
Q: ICT helps in international development by bridging the digital divide and providing equitable access to technologies.
Choose the correct answer from the following:
A | P only |
B | Q only |
C | P and Q |
D | Neither P nor Q |
Question 46 |
A confidential file needs to be deleted from a workstation. Which is the most effective way to ensure this?
A | Rename the file |
B | Compress the file and back-up to tape |
C | Copy and paste the file into the recycle bin and empty the recycle bin |
D | Drag the file into the recycle bin and empty the recycle bin |
Question 47 |
Which of the following statement(s) is/are true with regard to websites?
P: A blog is a website that consists of posts in reverse chronological order.
Q: A wiki is a website that is designed to allow people to collaborate easily.
Choose the correct answer from the following:
P: A blog is a website that consists of posts in reverse chronological order.
Q: A wiki is a website that is designed to allow people to collaborate easily.
Choose the correct answer from the following:
A | P only |
B | Q only |
C | P and Q |
D | Neither P nor Q |
Question 48 |
In the context of e-mail, what is ‘spam’?
A | The act of overloading an e-mail server by using denial-of-service attacks |
B | E-mail messages that are infected with viruses |
C | A large quantity of messages that do not reach the recipient |
D | Unsolicited advertising sent to a large number of recipients |
Question 49 |
A virus type that is capable of shifting from one computer to another without user interaction is known as a
A | Worm |
B | Trojan |
C | Logic bomb |
D | Boot sector |
Question 50 |
Read the following two statements:
I: Information and Communication Technology (ICT) is considered a subset of Information Technology (IT).
II: The 'right to use' a piece of software is termed as copyright.
Which of the above statement(s) is/are CORRECT?
I: Information and Communication Technology (ICT) is considered a subset of Information Technology (IT).
II: The 'right to use' a piece of software is termed as copyright.
Which of the above statement(s) is/are CORRECT?
A | Both I and II |
B | Neither I nor II |
C | II only |
D | I only |
Access subject wise (1000+) question and answers by becoming as a solutions adda PRO SUBSCRIBER with Ad-Free content
Register Now
You have completed
questions
question
Your score is
Correct
Wrong
Partial-Credit
You have not finished your quiz. If you leave this page, your progress will be lost.
Correct Answer
You Selected
Not Attempted
Final Score on Quiz
Attempted Questions Correct
Attempted Questions Wrong
Questions Not Attempted
Total Questions on Quiz
Question Details
Results
Date
Score
Hint
Time allowed
minutes
seconds
Time used
Answer Choice(s) Selected
Question Text
Need more practice!
Keep trying!
Not bad!
Good work!
Perfect!
