TCP
Question 1 |
Consider a long-lived TCP session with an end-to-end bandwidth of 1 Gbps (= 109 bits/second). The session starts with a sequence number of 1234. The minimum time (in seconds, rounded to the closest integer) before this sequence number can be used again is _________.
33 | |
34 | |
35 | |
36 |
The process of using all the sequence number and repeating a previously used sequence number.
The time taken to wrap around is called wrap around time:
Minimum Time = Wrap around time = Total number of bits in sequence number / Bandwidth = 232 * 8 / 109 = 34.35 == 34 (closest integer)
Question 2 |
Consider three IP networks A, B and C. Host HA in network A sends messages each containing 180 bytes of application data to a host HC in network C. The TCP layer prefixes a 20 byte header to the message. This passes through an intermediate network B. The maximum packet size, including 20 byte IP header, in each network is:
A : 1000 bytes
B : 100 bytes
C : 1000 bytes
The network A and B are connected through a 1 Mbps link, while B and C are connected by a 512 Kbps link (bps = bits per second).

Assuming that the packets are correctly delivered, how many bytes, including headers, are delivered to the IP layer at the destination for one application message, in the best case? Consider only data packets.
200 | |
220 | |
240 | |
260 |
Data will be divided in three packets as:
First packet: 80 bytes + 20 byte of header
Second packet: 80 bytes + 20 byte of header
Third packet: 40 bytes + 20 byte of header
Note: Defragmentation (grouping of fragments) is done only at destination.
HC will receive total 260 bytes including header.
Question 3 |
Consider three IP networks A, B and C. Host HA in network A sends messages each containing 180 bytes of application data to a host HC in network C. The TCP layer prefixes a 20 byte header to the message. This passes through an intermediate network B. The maximum packet size, including 20 byte IP header, in each network is:
A : 1000 bytes
B : 100 bytes
C : 1000 bytes
The network A and B are connected through a 1 Mbps link, while B and C are connected by a 512 Kbps link (bps = bits per second).

What is the rate at which application data is transferred to host HC? Ignore errors, acknowledgements, and other overheads.
325.5 Kbps
| |
354.5 Kbps | |
409.6 Kbps | |
512.0 Kbps |
Application data is transferred at rate of (180/260) x 512 Kbps = 354.46 Kbps
Question 4 |
If the client was waiting to receive a packet, it may wait indefinitely. | |
If the client sends a packet after the server reboot, it will receive a RST segment. | |
The TCP server application on S can listen on P after reboot. | |
If the client sends a packet after the server reboot, it will receive a FIN segment. |
- True
Since broken connections can only be detected by sending data, the receiving side will wait forever. This scenario is called a “half-open connection” because one side realizes the connection was lost but the other side believes it is still active. - True
The situation resolves itself when client tries to send data to server over the dead connection, and server replies with an RST packet (not FIN). - True
Yes, a TCP Server can listen to the same port number even after reboot. For example, the SMTP service application usually listens on TCP port 25 for incoming requests. So, even after reboot the port 25 is assigned to SMTP. - False
The situation resolves itself when client tries to send data to server over the dead connection, and server replies with an RST packet (not FIN), causing client to finally to close the connection forcibly.
FIN is used to close TCP connections gracefully in each direction (normal close of connection), while TCP RST is used in a scenario where TCP connections cannot recover from errors and the connection needs to reset forcibly.
Question 5 |
A program on machine X attempts to open a UDP connection to port 5376 on a machine Y, and a TCP connection to port 8632 on machine Z. However, there are no applications listening at the corresponding ports on Y and Z. An ICMP Port Unreachable error will be generated by
Y but not Z | |
Z but not Y | |
Neither Y nor Z | |
Both Y and Z |
Question 6 |
Consider the following statements about the timeout value used in TCP.
(i) The timeout value is set to the RTT (Round Trip Time) measured during TCP connection establishment for the entire duration of the connection.
(ii) Appropriate RTT estimation algorithm is used to set the timeout value of a TCP connection.
(iii) Timeout value is set to twice the propagation delay from the sender to the receiver.
Which of the following choices hold?
(i) is false, but (ii) and (iii) are true | |
(i) and (iii) are false, but (ii) is title | |
(i) and (ii) are false, but (iii) is true | |
(i), (ii) and (iii) are false |
The timeout value cannot be fixed for entire duration as it will turn timer to static timer, we need dynamic timer for timeout.
Statement-II: It is True.
Basic algorithm, Jacobson's algorithm, Karl's modification; these three algorithms are to be appropriate to RTT estimation algorithm used to set timeout value dynamically.
Statement-III: It is False.
Because timeout value is set to twice the propagation delay in data link layer where hop to hop distance is known, not in TCP layer.
Question 7 |
Consider a TCP connection in a state where there are no outstanding ACKs. The sender sends two segments back to back. The sequence numbers of the first and second segments are 230 and 290 respectively. The first segment was lost, but the second segment was received correctly by the receiver. Let X be the amount of data carried in the first segment (in bytes), and Y be the ACK number sent by the receiver. The values of X and Y (in that order) are
60 and 290 | |
230 and 291 | |
60 and 231 | |
60 and 230 |
Question 8 |
A firewall is to be configured to allow hosts in a private network to freely open TCP connections and send packets on open connections. However, it will only allow external hosts to send packets on existing open TCP connections or connections that are being opened (by internal hosts) but not allow them to open TCP connections to hosts in the private network. To achieve this the minimum capability of the firewall should be that of
A combinational circuit | |
A finite automaton | |
A pushdown automaton with one stack | |
A pushdown automaton with two stacks |
Turing machine can do everything as the normal computer can do, so firewall can be created by the TM.
Question 9 |
The three way handshake for TCP connection establishment is shown below.
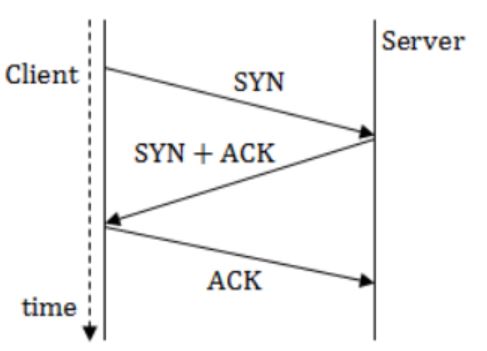
Which of the following statements are TRUE? (S1) Loss of SYN + ACK from the server will not establish a connection (S2) Loss of ACK from the client cannot establish the connection (S3) The server moves LISTEN → SYN_RCVD → SYN_SENT → ESTABLISHED in the state machine on no packet loss (S4) The server moves LISTEN → SYN_RCVD → ESTABLISHED in the state machine on no packet loss.
S2 and S3 only | |
S1 and S4 | |
S1 and S3 | |
S2 and S4 |
S2 → False, because if after ACK client immediately sends data then everything goes on without worry.
S3 → False.
S4 → True.
Question 10 |
(iv), (ii), (iii), (i)
| |
(ii), (iv), (iii), (i)
| |
(ii), (iv), (i), (iii) | |
(iv), (ii), (i), (iii) |
Question 11 |
The sequence number NP is chosen randomly by P
| |
The sequence number NP is always 0 for a new connection | |
The acknowledgement number NQ is equal to NP | |
The acknowledgement number NQ is equal to NP + 1 |
Question 12 |
30 bits | |
32 bits | |
34 bits | |
36 bits |
Question 13 |
Assume that the bandwidth for a TCP connection is 1048560 bits/sec. Let α be the value of RTT in milliseconds (rounded off to the nearest integer) after which the TCP window scale option is needed. Let β be the maximum possible window size the window scale option. Then the values of α and β are
63 milliseconds, 65535×214 | |
63 milliseconds, 65535×216 | |
500 milliseconds, 65535×214 | |
500 milliseconds, 65535×216 |
The wrap around time for given link = 1048560 * α. The TCP window scale option is an option to increase the receive window size. TCP allows scaling of windows when wrap around time > 65,535.
==> 1048560 * α > 65,535*8 bits
==> α = 0.5 sec = 500 mss
Scaling is done by specifying a one byte shift count in the header options field. The true receiver window size is left shifted by the value in shift count. A maximum value of 14 may be used for the shift count value. Therefore maximum window size with scaling option is 65535 × 214.
Question 14 |
Suppose two hosts use a TCP connection to transfer a large file. Which of the following statements is/are False with respect to the TCP connection?
- 1. If the sequence number of a segment is m, then the sequence
number of the subsequent segment is always m+1.
2. If the estimated round trip time at any given point of time is t sec, the value of the retransmission timeout is always set to greater than or equal to t sec.
3. The size of the advertised window never changes during the course of the TCP connection.
4. The number of unacknowledged bytes at the sender is always less than or equal to the advertised window.
III only | |
I and III only | |
I and IV only | |
II and IV only |
If the sequence no. of the segment is m, then the sequence number of the subsequent segment depends on the current segment size.
II. True.
If the estimated RTT at any given point of time is t second, then the value of the re-transmission timeout is always set to greater than or equal to t sec.
III. False.
The size of the advertised window may change during the course of the TCP connection depending on the processing capability at the receiver's side and the network traffic.
IV. True.
The number of unacknowledged bytes at the sender is always less than or equal to the advertised window, because the sender never sends no. of bytes greater than advertised window.
Question 15 |
Identify the correct sequence in which the following packets are transmitted on the network by a host when a browser requests a webpage from a remote server, assuming that the host has just been restarted.
HTTP GET request, DNS query, TCP SYN | |
DNS query, HTTP GET request, TCP SYN | |
DNS query, TCP SYN, HTTP GET request | |
TCP SYN, DNS query, HTTP GET request |
Question 16 |
Consider the following statements.
-
I. TCP connections are full duplex.
II. TCP has no option for selective acknowledgment.
III. TCP connections are message streams.
Only I is correct | |
Only I and III are correct | |
Only II and III are correct | |
All of I, II and III are correct |
Question 17 |
While opening a TCP connection, the initial sequence number is to be derived using a time-of-day (ToD) clock that keeps running even when the host is down. The low order 32 bits of the counter of the ToD clock is to be used for the initial sequence numbers. The clock counter increments once per millisecond. The maximum packet lifetime is given to be
Which one of the choices given below is closest to the minimum permissible rate at which sequence numbers used for packets of a connection can increase?
0.015/s | |
0.064/s | |
0.135/s | |
0.327/s |
The maximum packet lifetime is given is given 64s.
Maximum data rate possible(bandwidth) to avoid the wraparound = 232/64 = 226 Byte/sec.
The clock counter increments once per milliseconds = That means when then counter increments next possible sequence number is generated. The packet lifetime is 64 seconds and after this 64 seconds next sequence number is come. So that means in this 64 seconds only 1 sequence number is generated.
Hence the minimum rate is = 1/64 = 0.015/sec.
Question 18 |
1. The web browser requests a webpage using HTTP.
2. The web browser establishes a TCP connection with the web server.
3. The web server sends the requested webpage using HTTP.
4. The web browser resolves the domain name using DNS.
4,2,1,3 | |
1,2,3,4 | |
4,1,2,3 | |
2,4,1,3 |
Question 19 |
Let the size of congestion window of a TCP connection be 32 KB when a timeout occurs. The round trip time of the connection is 100 msec and the maximum segment size used is 2 KB. The time taken (in msec) by the TCP connection to get back to 32 KB congestion window is _________.
1100 to 1300 | |
1101 to 1301 | |
1102 to 1302 | |
1103 to 1303 |
When Time Out occurs, for the next round of Slow Start, Threshold = (size of Cwnd) / 2
It means Threshold = 16KB
Slow Start
2KB
1RTT
4KB
2RTT
8KB
3RTT
16KB ----------- Threshold reaches. So Additive Increase Starts
4RTT
18KB
5RTT
20KB
6RTT
22KB
7RTT
24KB
8RTT
26KB
9RTT
28KB
10RTT
30KB
11RTT
32KB
So, Total no. of RTTs = 11 → 11 * 100 = 1100
