Security
Question 1 |
Anarkali digitally signs a message and sends it to Salim. Verification of the signature by Salim requires
Anarkali's public key. | |
Salim's public key. | |
Salim's private key. | |
Anarkali's private key. |
Question 2 |
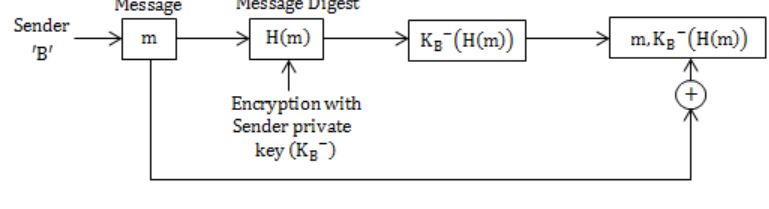
Consider that B wants to send a message m that is digitally signed to A. Let the pair of private and public keys for A and B be denoted by Kx- and Kx+ for x = A,B, respectively. Let Kx(m) represent the operation of encrypting m with a key Kx and H(m) represent the message digest. Which one of the following indicates the CORRECT way of sending the message m along with the digital signature to A?
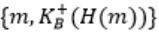 | |
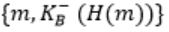 | |
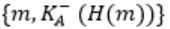 | |
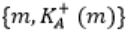 |
Question 2 Explanation:
Digital signatures are electronic signatures which ensure the integrity, non-repudiation and authenticity of message.
Message digest is a hash value generated by applying a function on it.
Message digest is encrypted using private key of sender, so it can only be decrypted by public key of sender.
This ensures that the message was sent by the known sender.
Message digest is sent with the original message to the receiving end, where hash function is used on the original message and the value generated by that is matched with the message digest.
This ensures the integrity and thus, that the message was not altered.
Digital signature uses private key of the sender to sign message digest.
Message digest is a hash value generated by applying a function on it.
Message digest is encrypted using private key of sender, so it can only be decrypted by public key of sender.
This ensures that the message was sent by the known sender.
Message digest is sent with the original message to the receiving end, where hash function is used on the original message and the value generated by that is matched with the message digest.
This ensures the integrity and thus, that the message was not altered.
Digital signature uses private key of the sender to sign message digest.

Question 3 |
A sender S sends a message m to receiver R, which is digitally signed by S with its private key. In this scenario, one or more of the following security violations can take place.
(I) S can launch a birthday attack to replace m with a fraudulent message.
(II) A third party attacker can launch a birthday attack to replace m with a fraudulent message.
(III) R can launch a birthday attack to replace m with a fraudulent message.
Which of the following are possible security violations?
(I) S can launch a birthday attack to replace m with a fraudulent message.
(II) A third party attacker can launch a birthday attack to replace m with a fraudulent message.
(III) R can launch a birthday attack to replace m with a fraudulent message.
Which of the following are possible security violations?
(I) and (II) only | |
(I) only | |
(II) only | |
(II) and (III) only |
Question 3 Explanation:
Birthday attack Problem is when sender replaces original message with fraud message having same message digest as the original message, along with the digital signature of the original message.
(I) Can the sender replace the message with a fraudulent message?
Yes, definitely because the sender will encrypt the message with its private key.
It can encrypt another message also with its private key.
(II) Can the third party send a fraudulent message?
No, because the third party doesn't know about the private key of the sender.
(III) Can receiver send the fraudulent message?
No, the receiver also doesn't know about the Private key of the sender.
So receiver also cannot send the fraudulent message.
(I) Can the sender replace the message with a fraudulent message?
Yes, definitely because the sender will encrypt the message with its private key.
It can encrypt another message also with its private key.
(II) Can the third party send a fraudulent message?
No, because the third party doesn't know about the private key of the sender.
(III) Can receiver send the fraudulent message?
No, the receiver also doesn't know about the Private key of the sender.
So receiver also cannot send the fraudulent message.
Question 4 |
Which of the following are used to generate a message digest by the network security protocols?
- (P) RSA
(Q) SHA-1
(R) DES
(S) MD5
P and R only | |
Q and R only | |
Q and S only | |
R and S only |
Question 4 Explanation:
RSA and DES are for Encryption where MD5 and SHA – 1 are used to generate Message Digest.
There are 4 questions to complete.
