UGC NET CS 2012 June-Paper2
Question 1 |
The postfix expression AB + CD – * can be evaluated using a
stack | |
tree | |
queue | |
linked list |
Question 1 Explanation:

Question 2 |
The post order traversal of a binary tree is DEBFCA. Find out the preorder traversal.
ABFCDE | |
ADBFEC | |
ABDECF | |
None of the above |
Question 2 Explanation:
Post order traversal tree is look like

Postorder: DEBFCA
Inorder: DBEAFC
Preorder: ABDECF

Postorder: DEBFCA
Inorder: DBEAFC
Preorder: ABDECF
Question 3 |
The branch logic that provides making capabilities in the control unit is known as
Controlled transfer | |
Conditional transfer | |
Unconditional transfer | |
None of the above |
Question 3 Explanation:
The branch logic that provides making capabilities in the control unit is known as controlled transfer.
Question 4 |
The number of colours required to properly colour the vertices of every planar graph is
2 | |
3 | |
4 | |
5 |
Question 4 Explanation:
→ The 4-colour theorem of the planar graph describes that any planar can at most be colored with 4 colors.
→ The sufficient number of colors in worst case is 4 colors for any planar graph.
→ The sufficient number of colors in worst case is 4 colors for any planar graph.
Question 5 |
Networks that use different technologies can be connected by using
Packets | |
Switches | |
Bridges | |
Routers |
Question 5 Explanation:
→ Switch is a multiport network bridge that uses hardware addresses to process and forward data at the data link layer (layer 2) of the OSI model. Some switches can also process data at the network layer (layer 3) by additionally incorporating routing functionality. Such switches are commonly known as layer-3 switches or multilayer switches.
→ Hub is basically a multiport repeater. A hub works at the physical layer (layer 1) of the OSI model. A repeater hub also participates in collision detection, forwarding a jam signal to all ports if it detects a collision.
→ Bridge operates at data link layer. A bridge is a repeater, with add on functionality of filtering content by reading the MAC addresses of source and destination. It is also used for interconnecting two LANs working on the same protocol. It has a single input and single output port, thus making it a 2 port device.
→ Router is a device like a switch that routes data packets based on their IP addresses. Router is mainly a Network Layer device. Routers normally connect LANs and WANs together and have a dynamically updating routing table based on which they make decisions on routing the data packets. Router divide broadcast domains of hosts connected through it.
→ Hub is basically a multiport repeater. A hub works at the physical layer (layer 1) of the OSI model. A repeater hub also participates in collision detection, forwarding a jam signal to all ports if it detects a collision.
→ Bridge operates at data link layer. A bridge is a repeater, with add on functionality of filtering content by reading the MAC addresses of source and destination. It is also used for interconnecting two LANs working on the same protocol. It has a single input and single output port, thus making it a 2 port device.
→ Router is a device like a switch that routes data packets based on their IP addresses. Router is mainly a Network Layer device. Routers normally connect LANs and WANs together and have a dynamically updating routing table based on which they make decisions on routing the data packets. Router divide broadcast domains of hosts connected through it.
Question 6 |
Both hosts and routers are TCP/IP protocol software. However, routers do not use protocol from all layers. The layer for which protocol software is not needed by a router is
Layer – 5 (Application) | |
Layer – 1 (Physical) | |
Layer – 3 (Internet) | |
Layer – 2 (Network Interface) |
Question 6 Explanation:
Router works on three layers which are physical layer, data link layer and network layer. It do not works on application layer. So the answer is option(A).
Router can connect two different networks like ethernet and token ring because it have two physical layer, two data link layer and one network layer to change the frame format according to the respective network
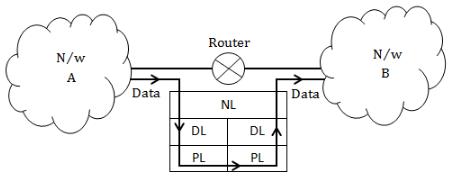
Router can't connect two networks which are using different protocols like one is using TCP/IP and other one is using ATM. For connecting such networks GATEWAYS are used because the works on application layer.
Router can connect two different networks like ethernet and token ring because it have two physical layer, two data link layer and one network layer to change the frame format according to the respective network

Router can't connect two networks which are using different protocols like one is using TCP/IP and other one is using ATM. For connecting such networks GATEWAYS are used because the works on application layer.
Question 7 |
In multiuser database if two users wish to update the same record at the same time, they are prevented from doing so by
Jamming | |
Password | |
Documentation | |
Record lock |
Question 7 Explanation:
→ In multiuser database if two users wish to update the same record at the same time, they are prevented from doing so by record lock.
→ Record locking is the technique of preventing simultaneous access to data in a database, to prevent inconsistent results.
→ A simple way to prevent this is to lock the file whenever a record is being modified by any user, so that no other user can save data. This prevents records from being overwritten incorrectly, but allows only one record to be processed at a time, locking out other users who need to edit records at the same time.
→ Record locking is the technique of preventing simultaneous access to data in a database, to prevent inconsistent results.
→ A simple way to prevent this is to lock the file whenever a record is being modified by any user, so that no other user can save data. This prevents records from being overwritten incorrectly, but allows only one record to be processed at a time, locking out other users who need to edit records at the same time.
Question 8 |
A binary search tree is a binary tree :
All items in the left subtree are less than root | |
All items in the right subtree are greater than or equal to the root | |
Each subtree is itself a binary search tree | |
All of the above |
Question 8 Explanation:
Binary search tree properties:
1. All items in the left subtree are less than root
2. All items in the right subtree are greater than or equal to the root
3. Each subtree is itself a binary search tree
2. All items in the right subtree are greater than or equal to the root
3. Each subtree is itself a binary search tree
Question 9 |
What deletes the entire file except the file structure ?
ERASE | |
DELETE | |
ZAP | |
PACK |
Question 9 Explanation:
→ PACK statement removes all records marked for deletion permanently.
→ DELETE statement is used to delete existing records in a table.
→ ZAP deletes the entire file except the file structure.
→ DELETE statement is used to delete existing records in a table.
→ ZAP deletes the entire file except the file structure.
Question 10 |
Which command is the fastest among the following ?
COPY TO | |
COPY STRUCTURE TO | |
COPY FILE | |
COPY TO MFILE-DAT DELIMITED |
Question 10 Explanation:
COPY STRUCTURE TO → It copying the structure rather than file. So, it is fastest among all.
Question 11 |
B+ tree are preferred to binary tree in Database because
Disk capacity are greater than memory capacities | |
Disk access is much slower than memory access | |
Disk data transfer rates are much less than memory data transfer rate | |
Disks are more reliable than memory |
Question 11 Explanation:
In B+ tree, each node can store multiple keys because of which number of disk access is less. While in binary tree each node can store only one key value so the number of disk access is greater than B+ tree. Since the disc access time is greater so it is better to have less number of disc accesses. So in that case B+ tree is preferred over binary tree.
Question 12 |
A Transaction Manager is which of the following ?
Maintains a log of transactions | |
Maintains before and after database images | |
Maintains appropriate concurrency control | |
All of the above |
Question 12 Explanation:
A transaction manager is one who is responsible for the ACID properties of a transaction.
→ He maintains the log of all transactions and ensures that only each transaction should be either performed completely or not performed at all.
→ Transaction manager ensure consistency preservation by maintaining the before and after database images of a transaction.
→ Multiple transactions can be executed simultaneously but it is the responsibility of transaction manager that the execution of a transaction should not be interfered with by any other transactions executing concurrently. So for that it maintains a appropriate concurrency control.
→ Transaction manager is also responsible for the durability of a transaction that is the changes applied to the database by a committed transaction must persist in the database. These changes must not be lost because of any failure.
→ He maintains the log of all transactions and ensures that only each transaction should be either performed completely or not performed at all.
→ Transaction manager ensure consistency preservation by maintaining the before and after database images of a transaction.
→ Multiple transactions can be executed simultaneously but it is the responsibility of transaction manager that the execution of a transaction should not be interfered with by any other transactions executing concurrently. So for that it maintains a appropriate concurrency control.
→ Transaction manager is also responsible for the durability of a transaction that is the changes applied to the database by a committed transaction must persist in the database. These changes must not be lost because of any failure.
There are 12 questions to complete.
