Nielit STA 17-12-2017
Question 1 |
Correct expression for UDP user datagram length is
length of UDP=length of IP - length of IP header | |
length of UDP=length of UDP - length of UDP header | |
length of UDP=length of IP + length of IP header | |
length of UDP=length of UDP + length of UDP header |
Question 1 Explanation:
→ Total length of the datagram in bytes.
→ The size of the data by computing "total length - header length"
→ A user datagram is encapsulated in an IP datagram. There is a field in the IP datagram the defines the total length. There is another field in the IP datagram that defines the length of the header. So if we subtract the length of a UDP datagram that is encapsulated in an IP datagram, we get the length of UDP user datagram.
→ The size of the data by computing "total length - header length"
→ A user datagram is encapsulated in an IP datagram. There is a field in the IP datagram the defines the total length. There is another field in the IP datagram that defines the length of the header. So if we subtract the length of a UDP datagram that is encapsulated in an IP datagram, we get the length of UDP user datagram.
Question 2 |
In binary search tree which traversal is used for getting ascending order values?
Inorder | |
Preorder | |
Postorder | |
None of the above |
Question 2 Explanation:
To traverse a binary search tree in inorder following operations are carried-out
(i) Traverse the left most subtree starting at the left external node,
(ii) Visit the root, and
(iii) Traverse the right subtree starting at the left external node.
The Inorder traversal of the above tree will outputs: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10
(i) Traverse the left most subtree starting at the left external node,
(ii) Visit the root, and
(iii) Traverse the right subtree starting at the left external node.
The Inorder traversal of the above tree will outputs: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 10
Question 3 |
The automaton which allows transformation to a new state without consuming any input symbols:
NFA
| |
DFA | |
NFA-ɛ / NFA-l
| |
All of the above |
Question 3 Explanation:
→ NFA-l or e-NFA is an extension of Non deterministic Finite Automata which are usually called NFA with epsilon moves or lambda transitions.
We extend the class of NFAs by allowing instantaneous (ε) transitions:
1. The automaton may be allowed to change its state without reading the input symbol.
2. In diagrams, such transitions are depicted by labeling the appropriate arcs with ε.
3. Note that this does not mean that ε has become an input symbol. On the contrary, we assume that the symbol ε does not belong to any alphabet.
We extend the class of NFAs by allowing instantaneous (ε) transitions:
1. The automaton may be allowed to change its state without reading the input symbol.
2. In diagrams, such transitions are depicted by labeling the appropriate arcs with ε.
3. Note that this does not mean that ε has become an input symbol. On the contrary, we assume that the symbol ε does not belong to any alphabet.
Question 4 |
Complement of a DFA can be obtained by:
making starting state as final state | |
make final as a starting state | |
make final states non-final and non final as final | |
None of the options |
Question 4 Explanation:
→ If (Q, ∑, δ, q0, F) be a DFA that accepts a language L, then the complement of the DFA can be obtained by swapping its accepting states with its non-accepting states and vice versa.
Note: If we want to complement an NFA, we have to first convert it to DFA and then have to swap states as in the previous method.
Question 5 |
Concatenation operation refers to which of the following set operations:
Union | |
Dot | |
Kleene | |
none of the options |
Question 5 Explanation:
→ It does not matter in which order we group the expression with the operators as they are associative.
→ If one gets a chance to group the expression, one should group them from left for convenience. For instance, 012 is grouped as (01)2.
→ If one gets a chance to group the expression, one should group them from left for convenience. For instance, 012 is grouped as (01)2.
Question 6 |
Which of the following statement is true?
mealy and moore machine are language acceptors | |
Finite state automata is language translator | |
NPDA is more powerful than DPDA | |
mealy machine is more powerful than moore machine |
Question 6 Explanation:
→ NPDA is more powerful than DPDA because
1.DPDA accept only a proper subset of CFL's ie. LL grammars.
2.NPDA can accept any CFL, which makes them more powerful over DPDA
1.DPDA accept only a proper subset of CFL's ie. LL grammars.
2.NPDA can accept any CFL, which makes them more powerful over DPDA
Question 7 |
If file size is large and if it is to be accessed randomly then which of the following allocation strategy should be best to use in a system?
Linked allocation
| |
Indexed allocation
| |
Contiguous allocation | |
None of the options |
Question 7 Explanation:
Contiguous:All blocks of a file are stored contiguously.
Advantages:
Faster access as all blocks are nearby.
Suitable for small sequentially accessed file
Disadvantages:
Poor performance if file grows or shrinks.
Linked Allocation:Each block stores pointer to next block
Advantages:
No fragmentation.
Suitable for large sequentially accessed file
Disadvantages:
Random access is not possible, If one link is lost, cannot access subsequent blocks
Note: In File Allocation Table (FAT) all links are cached in a table for faster access.
Indexed Allocation:A single bock stores indexes of all blocks of a file.
Advantage:
Suitable for large randomly accessed file
Eg: UNIX inode stores the first 12 or so data block pointers and then singly, doubly, and triply indirect pointers.
Advantages:
Faster access as all blocks are nearby.
Suitable for small sequentially accessed file
Disadvantages:
Poor performance if file grows or shrinks.
Linked Allocation:Each block stores pointer to next block
Advantages:
No fragmentation.
Suitable for large sequentially accessed file
Disadvantages:
Random access is not possible, If one link is lost, cannot access subsequent blocks
Note: In File Allocation Table (FAT) all links are cached in a table for faster access.
Indexed Allocation:A single bock stores indexes of all blocks of a file.
Advantage:
Suitable for large randomly accessed file
Eg: UNIX inode stores the first 12 or so data block pointers and then singly, doubly, and triply indirect pointers.
Question 8 |
Microprocessors are used in which generation of computers?
Ist generation | |
IInd generation
| |
IIIrd generation | |
IV generation |
Question 8 Explanation:
In the history of computing hardware, computers using
1. Vacuum tubes were called the first generation;
2. Transistors and diodes, the second;
3. Integrated circuits, the third;
4. Microprocessors, the fourth.
5. Whereas previous computer generations had focused on increasing the number of logic elements in a single CPU, the fifth generation, it was widely believed at the time, would instead turn to massive numbers of CPUs for added performance.
1. Vacuum tubes were called the first generation;
2. Transistors and diodes, the second;
3. Integrated circuits, the third;
4. Microprocessors, the fourth.
5. Whereas previous computer generations had focused on increasing the number of logic elements in a single CPU, the fifth generation, it was widely believed at the time, would instead turn to massive numbers of CPUs for added performance.
Question 9 |
Operating system maintains the page table for:
each process | |
each thread | |
each instruction | |
each address |
Question 9 Explanation:
Role of the page table
→ In operating systems that use virtual memory, every process is given the impression that it is working with large, contiguous sections of memory.
→ Physically, the memory of each process may be dispersed across different areas of physical memory, or may have been moved (paged out) to another storage, typically to a hard disk drive.
→ When a process requests access to data in its memory, it is the responsibility of the operating system to map the virtual address provided by the process to the physical address of the actual memory where that data is stored.
→ The page table is where the operating system stores its mappings of virtual addresses to physical addresses, with each mapping also known as a page table entry (PTE).
→ Physically, the memory of each process may be dispersed across different areas of physical memory, or may have been moved (paged out) to another storage, typically to a hard disk drive.
→ When a process requests access to data in its memory, it is the responsibility of the operating system to map the virtual address provided by the process to the physical address of the actual memory where that data is stored.
→ The page table is where the operating system stores its mappings of virtual addresses to physical addresses, with each mapping also known as a page table entry (PTE).
Question 10 |
Close-loop control mechanism try to:
Remove congestion after it occurs | |
Remove congestion after sometime | |
Prevent congestion before it occurs | |
Prevent congestion before sending packets |
Question 10 Explanation:
We can divide congestion control mechanisms into two broad categories:
open-loop congestion control (prevention)
closed-loop congestion control (removal).
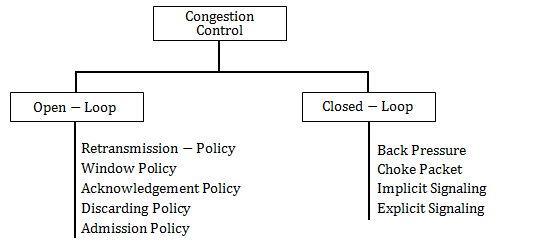
open-loop congestion control (prevention)
closed-loop congestion control (removal).

Question 11 |
Which multiple access technique is used by IEEE 802.11 standard for wireless LAN?
CDMA | |
CSMA/CA
| |
ALOHA | |
None of the Options |
Question 11 Explanation:
A wireless LAN system allows a station using infrared, visible light, or radio wave to communicate with similarly configured stations in the vicinity, or to communicate with remote stations via a nearby base station that is connected to a wired network. The most prevalent wireless LANs used today are those based IEEE 802.11. These standards use similar medium access control protocol and frame format as the Ethernet, and therefore IEEE 802.11 - based wireless LANs have been referred to as wireless Ethernets.
A wireless LAN can be characterized by the following attributes
Architecture
Physical layer
Medium access control layer
Architecture
Based on IEEE 802.11 standards, wireless LANs can be classified as follows: infrastructure and ad hoc. With the ad hoc architecture, wireless stations communicate directly with each other on an ad hoc basis.
Physical Layer
The physical layer is characterized by the following three elements: the frequency band, the multiple access method (which are similar to "multiplexing" in the wired environment, and the data rate.
Medium Access Control (MAC) Layer
This layer provide the same function as the MAC layer in the wired LAN environment. IEEE 802.11, instead of using Ethernet's CSMA/CD, specifies a scheme called CSMA/CA.
CA stands for Collision Avoidance. (In the wireless environment, since a station may not be able to hear all other stations, CD, Collision Detection is not feasible)
A wireless LAN can be characterized by the following attributes
Architecture
Physical layer
Medium access control layer
Architecture
Based on IEEE 802.11 standards, wireless LANs can be classified as follows: infrastructure and ad hoc. With the ad hoc architecture, wireless stations communicate directly with each other on an ad hoc basis.
Physical Layer
The physical layer is characterized by the following three elements: the frequency band, the multiple access method (which are similar to "multiplexing" in the wired environment, and the data rate.
Medium Access Control (MAC) Layer
This layer provide the same function as the MAC layer in the wired LAN environment. IEEE 802.11, instead of using Ethernet's CSMA/CD, specifies a scheme called CSMA/CA.
CA stands for Collision Avoidance. (In the wireless environment, since a station may not be able to hear all other stations, CD, Collision Detection is not feasible)
Question 12 |
PGP encrypts data using a block cipher called:
International data encryption algorithm | |
private data encryption algorithm | |
Internet data encryption algorithm | |
none of the options |
Question 12 Explanation:
→ International data encryption algorithm(IDEA) was used in Pretty Good Privacy (PGP) v2.0 and was incorporated after the original cipher used in v1.0, BassOmatic, was found to be insecure.
→ IDEA is an optional algorithm in the OpenPGP standard. PGP encrypts data by using a block cipher called international data encryption algorithm.
→ IDEA operates on 64-bit blocks using a 128-bit key and consists of a series of 8 identical transformations (a round, see the illustration) and an output transformation (the half-round).
→ The processes for encryption and decryption are similar.
→ IDEA is an optional algorithm in the OpenPGP standard. PGP encrypts data by using a block cipher called international data encryption algorithm.
→ IDEA operates on 64-bit blocks using a 128-bit key and consists of a series of 8 identical transformations (a round, see the illustration) and an output transformation (the half-round).
→ The processes for encryption and decryption are similar.
Question 13 |
If L1 and L2 are regular sets then intersection of these two will be:
Regular | |
Non regular | |
Recursive | |
Non Recursive |
Question 13 Explanation:
If L1 and If L2 are two regular languages, their intersection L1 ∩ L2 will also be regular.
Example
L1= {am bn | n ≥ 0 and m ≥ 0} and L2= {am bn ∪ bn am | n ≥ 0 and m ≥ 0}
L3 = L1 ∩ L2 = {am bn | n ≥ 0 and m ≥ 0} is also regular.
Example
L1= {am bn | n ≥ 0 and m ≥ 0} and L2= {am bn ∪ bn am | n ≥ 0 and m ≥ 0}
L3 = L1 ∩ L2 = {am bn | n ≥ 0 and m ≥ 0} is also regular.
Question 14 |
The smallest integer that can be represented by an 8-bit number in 2's complement form is:
-256
| |
-128 | |
-127 | |
0 |
Question 14 Explanation:
→ For n bit 2’s complement numbers, range of number is -(2(n-1)) to +(2(n-1)-1)
→ The smallest integer that can be represented by an 8-bit number in 2’s complement form is =-(2(n-1))
= -128
→ The smallest integer that can be represented by an 8-bit number in 2’s complement form is =-(2(n-1))
= -128
Question 15 |
Non contiguous memory allocation splits program into blocks of memory called ___ that can be loaded in non adjacent holes in main memory
Pages | |
Frames | |
Partition | |
Segments |
Question 15 Explanation:
Noncontiguous memory allocation splits programs into blocks of memory called Segments that can be loaded into non adjacent “holes” in main memory.
There are 15 questions to complete.
