ISRO CS 2009
Question 1 |
If G is a graph with e edges and n vertices, the sum of the degrees of all vertices in G is
e | |
e/2 | |
e2 | |
2 e |
Question 1 Explanation:
Handshaking theorem states that the sum of degrees of the vertices of a graph is twice the number of edges.
If G=(V,E) be a graph with E edges,then-
Σ degG(V) = 2E
This theorem applies even if multiple edges and loops are present.
Since the given graph is undirected, every edge contributes as twice in sum of degrees. So the sum of degrees is 2e.
Question 2 |
In networking, UTP stands for
Unshielded T-connector port | |
Unshielded twisted pair | |
Unshielded terminating pair | |
Unshielded transmission process |
Question 2 Explanation:
Unshielded twisted pair (UTP) is a ubiquitous type of copper cabling used in telephone wiring and local area networks (LANs).
There are five types of UTP cables -- identified with the prefix CAT, as in category -- each supporting a different amount of bandwidth.g a different amount of bandwidth.
There are five types of UTP cables -- identified with the prefix CAT, as in category -- each supporting a different amount of bandwidth.g a different amount of bandwidth.
Question 3 |
The address resolution protocol (ARP) is used for
Finding the IP address from the DNS | |
Finding the IP address of the default gateway | |
Finding the IP address that corresponds to a MAC address | |
Finding the MAC address that corresponds to an IP address |
Question 3 Explanation:
The Address Resolution Protocol (ARP) is a communication protocol used for discovering the link layer address, such as a MAC address, associated with a given internet layer address, typically an IPv4 address.
Question 4 |
Which of the following is a MAC address?
192.166.200.50 | |
00056A:01A01A5CCA7FF60 | |
568, Airport Road | |
01:A5:BB:A7:FF:60 |
Question 4 Explanation:
A media access control address (MAC address) of a device is a unique identifier assigned to a network interface controller (NIC).
MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or no separator.
Option (A) is example for IP address
Option (B) and (C ) are not examples for any address representation in computer
01:A5:BB:A7:FF:60 is the MAC address which consists of six groups of two hexadecimal digits, separated by hyphens, colons, or no separator.
MAC addresses are recognizable as six groups of two hexadecimal digits, separated by hyphens, colons, or no separator.
Option (A) is example for IP address
Option (B) and (C ) are not examples for any address representation in computer
01:A5:BB:A7:FF:60 is the MAC address which consists of six groups of two hexadecimal digits, separated by hyphens, colons, or no separator.
Question 5 |
What is the primary purpose of a VLAN?
Demonstrating the proper layout for a network | |
Simulating a network | |
To create a virtual private network | |
Segmenting a network inside a switch or device |
Question 5 Explanation:
1. A virtual local area network (VLAN) is a logical group of workstations, servers and network devices that appear to be on the same LAN despite their geographical distribution. A VLAN allows a network of computers and users to communicate in a simulated environment as if they exist in a single LAN and are sharing a single broadcast and multicast domain.
2. Higher-end switches allow the functionality and implementation of VLANs.
3. VLANs address issues such as scalability, security, and network management. Network architects set up VLANs to provide network segmentation
2. Higher-end switches allow the functionality and implementation of VLANs.
3. VLANs address issues such as scalability, security, and network management. Network architects set up VLANs to provide network segmentation
Question 6 |
SHA-1 is a
encryption algorithm | |
decryption algorithm | |
key exchange algorithm | |
message digest function |
Question 6 Explanation:
SHA-1 produces a 160-bit hash value or message digests from the inputted data (data that requires encryption), which resembles the hash value of the MD5 algorithm.
Question 7 |
Advanced Encryption Standard (AES) is based on
Asymmetric key algorithm | |
Symmetric key algorithm | |
Public key algorithm | |
Key exchange |
Question 7 Explanation:
The Advanced Encryption Standard, or AES, is a symmetric block cipher chosen by the U.S. government to protect classified information.
AES is Symmetric key algorithm
AES is Symmetric key algorithm
Question 8 |
The primary purpose of an operating system is
To make most efficient use of the computer hardware | |
To allow people to use the computer | |
To keep systems programmers employed | |
To make computers easier to use |
Question 8 Explanation:
Explanation: An operating system has three main functions:
(1) manage the computer’s resources, such as the central processing unit, memory, and other input – output sources
(2) establish a user interface, and
(3) execute and provide services for applications software.
OS provides an interface between the user and the hardware and thus making the computer easy to use for the user but the primary function of OS is to manage the hardware in the most efficient way.
(1) manage the computer’s resources, such as the central processing unit, memory, and other input – output sources
(2) establish a user interface, and
(3) execute and provide services for applications software.
OS provides an interface between the user and the hardware and thus making the computer easy to use for the user but the primary function of OS is to manage the hardware in the most efficient way.
Question 9 |
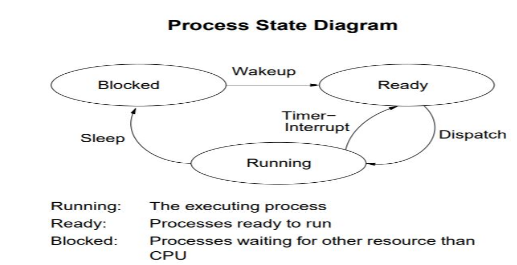
Which is the correct definition of a valid process transition in an operating system?
Wake up: ready → running | |
Dispatch: ready → running | |
Block: ready → running | |
Timer runout: ready → running |
Question 9 Explanation:
From the below process state diagram, we can easily that the option (B) is correct.

Question 10 |
The correct matching of the following pairs is
(A) Disk check (1) Round robin
(B) Batch processing (2) Scan
(C) Time sharing (3) LIFO
(D) Stack operation (4) FIFO
(A) Disk check (1) Round robin
(B) Batch processing (2) Scan
(C) Time sharing (3) LIFO
(D) Stack operation (4) FIFO
A B C D 3 4 2 1 | |
A B C D 4 3 2 1 | |
A B C D 3 4 1 2 | |
A B C D 2 4 1 3 |
Question 10 Explanation:
Scan is disk scheduling algorithm
In the round robin algorithm, each process will execute for particular time quantum,So it is the example for time sharing,
Stack is last in first out(LIFO)
In the batching processing, whatever process arrives first, it execute that process. So it First in First out(FIFO)
In the round robin algorithm, each process will execute for particular time quantum,So it is the example for time sharing,
Stack is last in first out(LIFO)
In the batching processing, whatever process arrives first, it execute that process. So it First in First out(FIFO)
Question 11 |
A page fault
Occurs when a program accesses an available page on memory | |
is an error in a specific page | |
is a reference to a page belonging to another program | |
occurs when a program accesses a page not currently in memory |
Question 11 Explanation:
A page fault is a type of exception raised by computer hardware when a running program accesses a memory page that is not currently mapped by the memory management unit (MMU) into the virtual address space of a process
Question 12 |
The infix expression A+(B–C)*D is correctly represented in prefix notation as
A+B−C∗D | |
+A∗−BCD | |
ABC−D∗+ | |
A+BC−D∗ |
Question 12 Explanation:
Given Expression = A + (B – C)* D
Prefix Notation:
A + (- B C) * D
A + (* - B C D)
+ A * - B C D
Question 13 |
If the pdf of a Poisson distribution is given by f(x) = (e-22x)/x!, then its mean is
2x | |
2 | |
-2 | |
1 |
Question 13 Explanation:
Given the function f(x) = (e-22x)/x!
Poisson Formula. Suppose we conduct a Poisson experiment, in which the average number of successes within a given region is μ.
Then, the Poisson probability is: P(x; μ) = (e-μ) (μx) / x!
where x is the actual number of successes that result from the experiment, and e is approximately equal to 2.71828.
From the given function the “μ” value is 2 which is the mean.
Poisson Formula. Suppose we conduct a Poisson experiment, in which the average number of successes within a given region is μ.
Then, the Poisson probability is: P(x; μ) = (e-μ) (μx) / x!
where x is the actual number of successes that result from the experiment, and e is approximately equal to 2.71828.
From the given function the “μ” value is 2 which is the mean.
Question 14 |
If the mean of a normal frequency distribution of 1000 items is 25 and its standard deviation is 2.5, then its maximum ordinate is
(1000/√2π).e-25 | |
1000/√2π | |
(1000/√2π ).e-2.5 | |
400/√2π |
Question 14 Explanation:

Question 15 |
Consider a system having “n” resources of same type. These resources are shared by 3 processes, A, B, C. These have peak demands of 3, 4, and 6 respectively. For what value of “n” deadlock won’t occur
15 | |
9 | |
10 | |
11 |
Question 15 Explanation:
Number of min resources required = (3-1) + (4-1) + (6-1) + 1 = 11
Question 16 |
Consider a set of 5 processes whose arrival time, CPU time needed and the priority are given below:

(smaller the number, higher the priority)
If the CPU scheduling policy is priority scheduling without preemption, the average waiting time will be
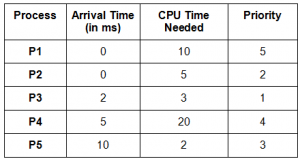
(smaller the number, higher the priority)
If the CPU scheduling policy is priority scheduling without preemption, the average waiting time will be
12.8 ms | |
11.8 ms | |
10.8 ms | |
9.8 ms |
Question 16 Explanation:
Following is the Gantt diagram:

Average Waiting Time = (30 + 3 + 3 + 18)/ 5 = 10.8

Average Waiting Time = (30 + 3 + 3 + 18)/ 5 = 10.8
Question 17 |
The range of integers that can be represented by n bit 2’s complement number system is:
-2n-1 to (2n-1 – 1) | |
-(2n-1 – 1)to (2n-1 – 1) | |
-2n-1 to (2n-1 ) | |
-(2n-1 + 1)to (2n-1 – 1) |
Question 17 Explanation:
The range of integers that can be represented by n bit 2’s complement number system is -2n-1 to (2n-1 – 1).
Question 18 |
Which of the following is/are true of the auto-increment addressing mode?
I. It is useful in creating self-relocating code
II. If it is included in an Instruction Set Architecture, then an additional ALU is required for effective address calculation
III. The amount of increment depends on the size of the data item accessed
I only | |
II only | |
III only | |
None of the above |
Question 18 Explanation:
After determining the effective address, the value in the base register is incremented by the size of the data item that is to be accessed.
For example, (A7)+ would access the content of the address register A7, then increase the address pointer of A7 by 1 (usually 1 word). Within a loop, this addressing mode can be used to step through all the elements of an array or vector.
For example, (A7)+ would access the content of the address register A7, then increase the address pointer of A7 by 1 (usually 1 word). Within a loop, this addressing mode can be used to step through all the elements of an array or vector.
Question 19 |
In which addressing mode, the effective address of the operand is generated by adding a constant value to the content of a register?
Absolute mode
| |
Indirect mode
| |
Immediate mode
| |
Index mode |
Question 19 Explanation:
1. An absolute address is represented by the contents of a register. This addressing mode is absolute in the sense that it is not specified relative to the current instruction address.
2. Indirect addressing is a scheme in which the address specifies which memory word or register contains not the operand but the address of the operand.
Immediate Operand:
The simplest way for an instruction to specify an operand is for the address part of the instruction actually to contain the operand itself rather than an address or other information describing where the operand is. Such an operand is called an immediate operand because it is automatically fetched from memory at the same time the instruction itself is fetched. It is immediately available for use.
Index mode:
The address of the operand is obtained by adding to the contents of the general register (called index register) a constant value. The number of the index register and the constant value are included in the instruction code
2. Indirect addressing is a scheme in which the address specifies which memory word or register contains not the operand but the address of the operand.
Immediate Operand:
The simplest way for an instruction to specify an operand is for the address part of the instruction actually to contain the operand itself rather than an address or other information describing where the operand is. Such an operand is called an immediate operand because it is automatically fetched from memory at the same time the instruction itself is fetched. It is immediately available for use.
Index mode:
The address of the operand is obtained by adding to the contents of the general register (called index register) a constant value. The number of the index register and the constant value are included in the instruction code
There are 19 questions to complete.
