NIC-NIELIT Scientist-B 2020
Question 1 |
Directions for question number 1 and 2:
Study the information below and answer questions based on it.
Five of India’s leading models are posing for a photograph promoting “World Peace and Understanding”. But then, Sachin Malhotra the photographer is having a tough time getting them to stand in a straight line, because Natasha refuses to stand next to Jessica since Jessica had said something about her in a leading gossip magazine. Rachel and Anna want to stand together because they are good friends. Ria on the other hand cannot get along well with Rachel, because there is some talk about Rachel scheming to get a contract already awarded to Ria. Anna believes her friendly astrologer who has asked her to stand at the extreme right for all group photographs. Finally, Sachin managed to pacify the girls and got a beautiful picture of five beautiful girls smiling beautifully in a straight line, promoting world peace.
Q1: If Natasha stands at the extreme left, who is standing second from left?
Cannot say | |
Jessica | |
Rachel | |
Ria |
Question 2 |
Directions for question number 1 and 2:
Study the information below and answer questions based on it.
Five of India’s leading models are posing for a photograph promoting “World Peace and Understanding”. But then, Sachin Malhotra the photographer is having a tough time getting them to stand in a straight line, because Natasha refuses to stand next to Jessica since Jessica had said something about her in a leading gossip magazine. Rachel and Anna want to stand together because they are good friends. Ria on the other hand cannot get along well with Rachel, because there is some talk about Rachel scheming to get a contract already awarded to Ria. Anna believes her friendly astrologer who has asked her to stand at the extreme right for all group photographs. Finally, Sachin managed to pacify the girls and got a beautiful picture of five beautiful girls smiling beautifully in a straight line, promoting world peace.
Q2: If Anna’s astrologer tells her to stand second from left and Natasha decides to stand second from right, then who is the girl standing at the extreme right?
Rachel | |
Jessica | |
Ria | |
None of the options |
Question 2 Explanation:
Option C will be most appropriate among the given options.
Question 3 |
Directions for question number 3 to 7:
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)
Total population of the given States = 3276000

Q3. If in the year 2018, population of F is increased by 10% and population of B is increased by 12% as compared to the previous year, then ______ is the ratio of population of F and B in 2017.
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)
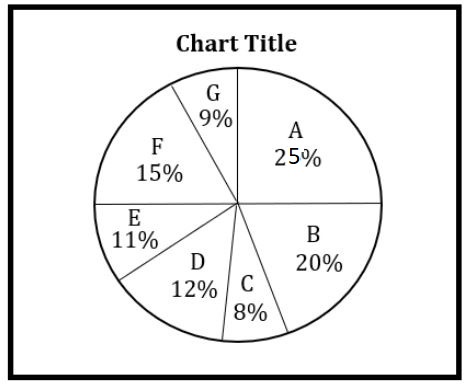
Total population of the given States = 3276000
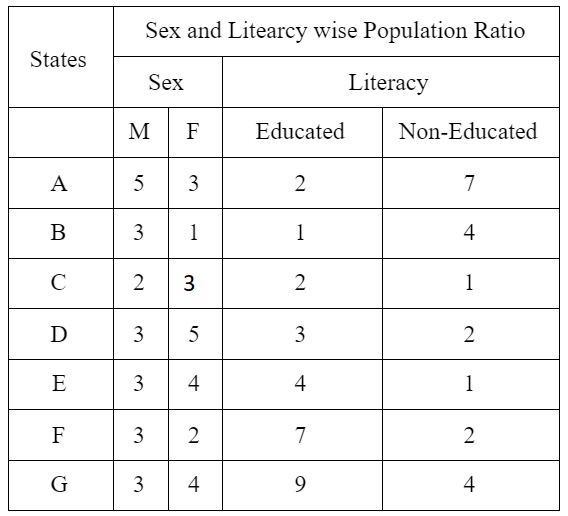
Q3. If in the year 2018, population of F is increased by 10% and population of B is increased by 12% as compared to the previous year, then ______ is the ratio of population of F and B in 2017.
42 : 55 | |
62 : 55 | |
42 : 11 | |
44 : 5 |
Question 3 Explanation:
F 2018 = (15/100)*3276000
B 2018 = (20/100)*3276000
F increased by 10% in 2018.
B increases by 12% in 2018.
So, F 2017→ 1.1 times= 15*32760
B 2017→ 1.12 times = 20*32760
F 2017 : B2017 = [(15*3276)*10]/11 : [(20*32760)*100]/112
= 42:55
B 2018 = (20/100)*3276000
F increased by 10% in 2018.
B increases by 12% in 2018.
So, F 2017→ 1.1 times= 15*32760
B 2017→ 1.12 times = 20*32760
F 2017 : B2017 = [(15*3276)*10]/11 : [(20*32760)*100]/112
= 42:55
Question 4 |
Directions for question number 3 to 7:
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)
Total population of the given States = 3276000

Q4. _______ is the percentage of total number of males in F, B and D together to the total population of all the given states.
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q4. _______ is the percentage of total number of males in F, B and D together to the total population of all the given states.
24% | |
17.5% | |
28.5% | |
29.5% |
Question 4 Explanation:
Let population=X
Males of F in 2018 = (⅗)*15*(X/100) = 9X/100
Males of B in 2018 = (¾)*20*(X/100) = 15X/100
Males of D in 2018 = (⅜)*12*(X/100)=4.5X/100
Total=(28.5*X)/100
X=28.5%
Males of F in 2018 = (⅗)*15*(X/100) = 9X/100
Males of B in 2018 = (¾)*20*(X/100) = 15X/100
Males of D in 2018 = (⅜)*12*(X/100)=4.5X/100
Total=(28.5*X)/100
X=28.5%
Question 5 |
Directions for question number 3 to 7:
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q5. The number of males in F in the year 2018 is ______.
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q5. The number of males in F in the year 2018 is ______.
294650 | |
294840 | |
301470 | |
301200 |
Question 5 Explanation:
Males of F in 2018 = (9X/100) = (9/100)*3276000
=10’s digit is 4
So, Option-B is correct.
=10’s digit is 4
So, Option-B is correct.
Question 6 |
Directions for question number 3 to 7:
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q6. _____ is the ratio of the number of females in G to the number of females in C.
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q6. _____ is the ratio of the number of females in G to the number of females in C.
16 : 5 | |
16 : 7 | |
15 : 11 | |
15 : 14 |
Question 6 Explanation:
=327600*9*(4/7) : 327600*8*(3/5)
=(9*4)/7 * 5/(8*3)
= 15:14
=(9*4)/7 * 5/(8*3)
= 15:14
Question 7 |
Directions for question number 3 to 7:
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q7. _____ is the total number of non-educated people in A and B in 2018.
Study the following and the table and answer the questions given below. (Data of different states regarding population of states in the year 2018)

Total population of the given States = 3276000

Q7. _____ is the total number of non-educated people in A and B in 2018.
1276040 | |
1032170 | |
1081550 | |
1161160 |
Question 7 Explanation:
Non educated people= A 2018 + B 2018
= (7/9) * (25X/100) + ⅘ * (20X / 100) * 9/9
= 1161160
= (7/9) * (25X/100) + ⅘ * (20X / 100) * 9/9
= 1161160
Question 8 |
The admission ticket for an Art Gallery bears a password which is changed after every clock hour based on set of words chosen for each day. The following is an illustration of the code and steps of rearrangement for subsequent clock hours.
The Time is 9 a.m. to 3 p.m. Day’s first password:
First Batch - 9 a.m. to 10 a.m.
is not ready cloth simple harmony burning
Second Batch - 10 a.m. to 11 a.m.
ready not is cloth burning harmony simple
Third Batch - 11 a.m. to 12 noon
cloth is not ready simple harmony burning
Fourth Batch - 12 noon to 1 p.m.
not is cloth ready burning harmony simple
Fifth Batch - 1 p.m. to 2 p.m.
ready cloth is not simple harmony burning and so on.
If the password for 11 a.m. to 12 noon was - “soap shy miss pen yet the she”, what was the password for the First Batch?
The Time is 9 a.m. to 3 p.m. Day’s first password:
First Batch - 9 a.m. to 10 a.m.
is not ready cloth simple harmony burning
Second Batch - 10 a.m. to 11 a.m.
ready not is cloth burning harmony simple
Third Batch - 11 a.m. to 12 noon
cloth is not ready simple harmony burning
Fourth Batch - 12 noon to 1 p.m.
not is cloth ready burning harmony simple
Fifth Batch - 1 p.m. to 2 p.m.
ready cloth is not simple harmony burning and so on.
If the password for 11 a.m. to 12 noon was - “soap shy miss pen yet the she”, what was the password for the First Batch?
pen miss shy soap she the yet | |
shy miss pen soap yet the she | |
soap pen miss shy she the yet | |
miss shy soap pen she the yet |
Question 8 Explanation:
cloth is not ready simple harmony burning
Soap shy miss pen yet the she
is not ready cloth simple harmony burning
shy miss pen soap yet the she
Soap shy miss pen yet the she
is not ready cloth simple harmony burning
shy miss pen soap yet the she
Question 9 |
There are 6 boxes numbered 1, 2, …...., 6. Each box is to be filled up either with a red or a green ball in such a way that at least 1 box contains a green ball and the boxes containing green balls are consecutively numbered. The total number of ways in which this can be done is:
18 | |
19 | |
20 | |
21 |
Question 9 Explanation:
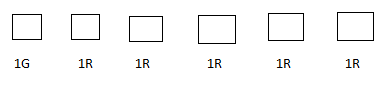
1G 5R → 6 ways
2G 4R → 5 ways
3G 3R → 4 ways
4G 2R → 3 ways
5G 1R → 2 ways
6G 0R → 1 way
Total = 21 ways
Question 10 |
If a cube with length, height and width equal to 10 cm, is reduced to a smaller cube of height, length and width of 9 cm then reduction in volume is:
172 cm2 | |
729 cm2 | |
271 cm2 | |
None of the options |
Question 10 Explanation:
= 103 - 93
= 271 cm3
= 271 cm3
Question 11 |
If 09/12/2001 (DD/MM/YYYY) happens to be Sunday, then 09/12/1971 would have been a:
Wednesday | |
Tuesday | |
Saturday | |
Thursday |
Question 11 Explanation:
In 30 years there are 22 non leap years and 8 leap years are there.
for every non leap year 1 odd day. and for leap year 2 odd days.
total no.of odd days = (22*1) + ( 8 * 2) = 38.
odd days = 38/7 = 3.
sunday - 3 = Thursday.
Note: Might be you did sunday + 3 = wednesday. ( here we need to calculate 30 day previous day )
for every non leap year 1 odd day. and for leap year 2 odd days.
total no.of odd days = (22*1) + ( 8 * 2) = 38.
odd days = 38/7 = 3.
sunday - 3 = Thursday.
Note: Might be you did sunday + 3 = wednesday. ( here we need to calculate 30 day previous day )
Question 12 |
Select a suitable figure from the four alternatives that would complete the figure matrix.


 | |
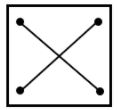 | |
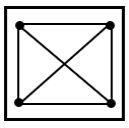 | |
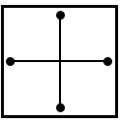 |
Question 13 |
What is the value of k for which the following system of equations has no solution:
2x - 8y = 3 and kx + 4y = 10
2x - 8y = 3 and kx + 4y = 10
-2 | |
1 | |
-1 | |
2 |
Question 13 Explanation:
2X - 8Y = 3
KX + 4Y = 10
(a1 / a2) = (b1 / b2) ≠ (c1/c2)
2/K = (-8/4)
K= -1
KX + 4Y = 10
(a1 / a2) = (b1 / b2) ≠ (c1/c2)
2/K = (-8/4)
K= -1
Question 14 |
A player rolls a die and receives the same number of rupees as the number of dots on the face that turns up. What should the player pay for each roll if he wants to make a profit of one rupee per throw of the die in the long run?
₹ 2.50
| |
₹ 2 | |
₹ 3.50 | |
₹ 4 |
Question 15 |
Gopal went to a fruit market with certain amount of money. With this money he can buy either 50 oranges or 40 mangoes. He retains 10% of the money for taxi fare. If he buys 20 mangoes, then the number of oranges he can buy with balance amount is:
25 | |
20 | |
18 | |
6 |
Question 15 Explanation:
50 0range = 40 Mangoes = X
Orange = X/50
Mangoes = X/40
→ X - 0.1 X - 20 M
→ X - 0.1 X - (20*(X/40))
→ 0.4 X
→ 0.4 * 50 Oranges
= 20 Oranges
Orange = X/50
Mangoes = X/40
→ X - 0.1 X - 20 M
→ X - 0.1 X - (20*(X/40))
→ 0.4 X
→ 0.4 * 50 Oranges
= 20 Oranges
Question 16 |
Number of letters repeated in the given word ‘MEASUREMENTS’ are indicated in front of each alternative. Identify the correct alternative.
M2E2A2S2U1R1N1T1 | |
M2E3A1S1U2R1N2T1 | |
M2E2A1S2U1R1N1T1 | |
M2E3A1S2U1R1N1T1 |
Question 16 Explanation:
Verify the options by counting the number of characters and matching with the subscript of the every character.
M2E3A1S2U1R1N1T1
M2E3A1S2U1R1N1T1
Question 17 |
If X says that his mother is the only daughter of Y’s mother, then how is Y related to X?
Brother | |
Son | |
Uncle | |
Father |
Question 18 |
A solid cube of each side 8 cm, has been painted red, blue and black on pairs of opposite faces. It is then cut into cubical blocks of each side 2 cm. How many cubes have no face painted?
0 | |
4 | |
8 | |
12 |
Question 18 Explanation:
8 → 3 face painted
24 → 2 face painted
24 → 1 face painted
8 → No face painted
24 → 2 face painted
24 → 1 face painted
8 → No face painted
Question 19 |
Find out the alternative figure which contains the given figure as its part.

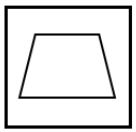
 | |
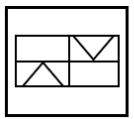 | |
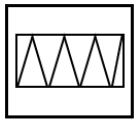 | |
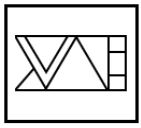 |
Question 20 |
Identify the figure that completes the pattern.


 | |
 | |
 | |
 |
Question 21 |
A university library budget committee must reduce exactly five of eight areas of expenditure - I, J, K, K, M, N, O and P - in accordance with the following conditions:
If both I and O are reduced, P is also reduced.
If L is reduced, neither N nor O is reduced.
If M is reduced, J is not reduced.
Of the three areas J, K and N exactly two are reduced.
If both K and N are reduced, which one of the following is a pair of areas neither of which could be reduced?
If both I and O are reduced, P is also reduced.
If L is reduced, neither N nor O is reduced.
If M is reduced, J is not reduced.
Of the three areas J, K and N exactly two are reduced.
If both K and N are reduced, which one of the following is a pair of areas neither of which could be reduced?
I, L | |
J, L | |
J, M | |
I, J |
Question 21 Explanation:
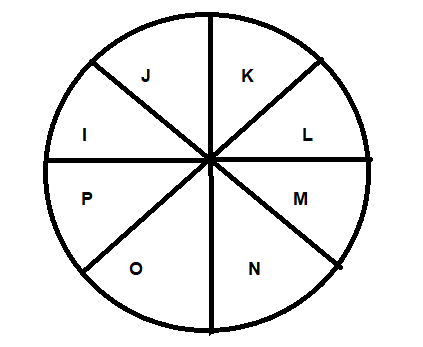
L i X reduced, Neither N or O are reduced.
K, N are reduced → J can’t be red.
So, the correct answer is J and L
Question 22 |
Which of these statements reflects a contrast between two flowers?
This tulip is as colourful as a rose. | |
This tulip does not smell as bad as a daffodil. | |
This tulip turns towards light just like sunflower. | |
This tulip is grown in bunches, like a lotus. |
Question 23 |
Choose the missing terms out of the given alternatives.
EJO, TYD, INS, XCH, …….?
EJO, TYD, INS, XCH, …….?
NRW | |
MRW | |
MSX | |
NSX |
Question 23 Explanation:
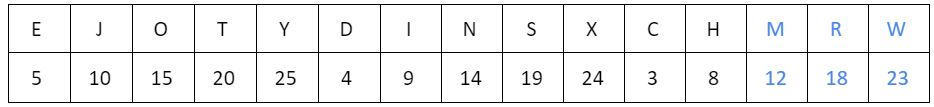
Question 24 |
Choose which of the following will be sufficient to find: What time did the bus leave today?
Statements:
The bus normally leaves on time.
The scheduled departure is at 12:30.
Statements:
The bus normally leaves on time.
The scheduled departure is at 12:30.
I alone is sufficient while II alone is not sufficient | |
II alone is sufficient while I alone is not sufficient | |
Either I or II is sufficient | |
Neither I nor II is sufficient |
Question 25 |
In the following question below are given three statements followed by three conclusions numbered I, II and III. You have to take the two statements to be true even if they seem to be at variance from the commonly known facts. Read all the conclusions and then decide which of the given conclusions logically follow from the two given statements, disregarding commonly known facts.
Statements:
Some pigeons are eagles.
All eagles are sparrows.
Some sparrows are not pigeons.
Conclusions:
Some sparrows are pigeons.
All pigeons are sparrows.
All eagles are pigeons.
Statements:
Some pigeons are eagles.
All eagles are sparrows.
Some sparrows are not pigeons.
Conclusions:
Some sparrows are pigeons.
All pigeons are sparrows.
All eagles are pigeons.
Only I follows | |
Only II follows | |
Only III follows | |
Both I and III follows |
Question 25 Explanation:
Question 26 |
Find the odd one out in the given series:
ZA, RS, DE, JK, PR, LM, YZ, NO
ZA, RS, DE, JK, PR, LM, YZ, NO
JK | |
LM | |
ZA | |
PR |
Question 26 Explanation:
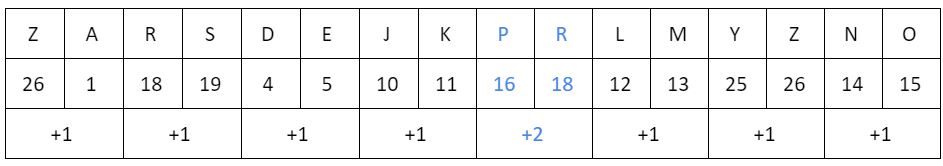
Question 27 |
In an office, 30% of the employees were women and 70% of the employees were above the age of 40 years, out of which 60% are men. Find the percentage of women employees who are above 40 years out of the total number of women employees.
96% | |
93.33% | |
70.44% | |
80.66%
|
Question 27 Explanation:
30% Employee → Women
70% Employee → greater than 40 → 60% Men AND 40% Women
70% → Men
Percentage of women( > 40 out of total women) = [(0.4*0.7Employee)/0.3Employee]*100
= (28/3)*10
= 93.33%
70% Employee → greater than 40 → 60% Men AND 40% Women
70% → Men
Percentage of women( > 40 out of total women) = [(0.4*0.7Employee)/0.3Employee]*100
= (28/3)*10
= 93.33%
Question 28 |
What is the next number
16, 30, 54, 88, 132
16, 30, 54, 88, 132
186 | |
188 | |
190 | |
206 |
Question 28 Explanation:
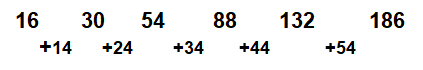
Question 29 |
Three squares are there as shown on the three sides of the triangle; find the area of the triangle from the respective areas of the squares.

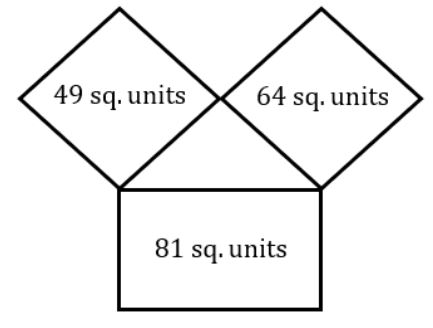
15√5 | |
12√5 | |
2√5 | |
1 |
Question 29 Explanation:
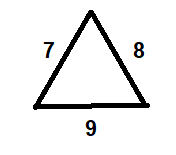
S=(a+b+c)/2
=(7+8+9)/2
=12
√(S(S-a)(S-b)(S-c))
√(12(5)(4)(3)
12√5
Question 30 |
Two tapes A and B can fill a tank in 12 minutes and 15 minutes respectively. The tank can be emptied by a third tap C in 6 minutes. If A and B are kept open for 5 minutes in the beginning and then C is opened along with A and B being kept open, the time taken to empty the tank is:
60 minutes | |
45 minutes | |
30 minutes | |
75 minutes |
Question 30 Explanation:
A → 12 min = 1/12
B → 15 min = 1/15
C → 6 min = -(⅙)
=((1/12)+(1/15))*5
=((15+12)/(12*15))*5
=27/36
=¾
= (1/12) + (1/15) - (⅙)
= (15+12-(15*2))/15*12
= -3 / (15*12)
= -(1/60)
1 Tank → 60 min
¾ Tank → 45 min
B → 15 min = 1/15
C → 6 min = -(⅙)
=((1/12)+(1/15))*5
=((15+12)/(12*15))*5
=27/36
=¾
= (1/12) + (1/15) - (⅙)
= (15+12-(15*2))/15*12
= -3 / (15*12)
= -(1/60)
1 Tank → 60 min
¾ Tank → 45 min
There are 30 questions to complete.
