UGC NET CS 2009-June-Paper-2
Question 1 |
If x and y are independent Gaussian random variables with average value 0 and with same variance, their joint probability density function is given by :
p(x, y)=p(x).p(y) | |
p(x, y)=p(x)+p(y) | |
p(x, y)=p(x+y) | |
p(x, y)=p(x).p(y)+p(x) |
Question 1 Explanation:
As they are independent, answer could be Option-A, though it need to be checked with zero average too.
Note: Original key given option-C is correct answer
Note: Original key given option-C is correct answer
Question 2 |
In order that a code is ‘t’ error correcting, the minimum Hamming distance should be :
t | |
2t-1 | |
2t | |
2t+1 |
Question 2 Explanation:
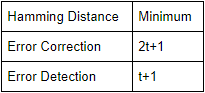
Question 3 |
The boolean expression x'y'z+yz+xz is equivalent to:
x | |
y | |
z | |
x+y+z |
Question 3 Explanation:
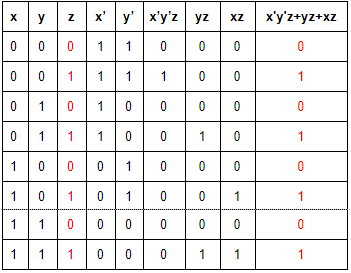
Question 4 |
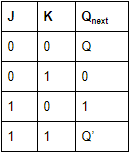
The characteristic equation of a JK flip flop is :
Qn+1 = J.Qn +K.Qn | |
Qn+1 = J.Q'n +K'Qn | |
Qn+1= QnJ.K | |
Qn+1= (J+K)Qn |
Question 4 Explanation:
The characteristic equation of a JK flip flop is Qn+1 = J.Q'n +K'Qn Characteristic Table:

Question 5 |
In order to implement a n variable switching function, a MUX must have :
2n inputs | |
2n+1 inputs | |
2n-1 inputs | |
2n-1 inputs |
Question 5 Explanation:
In order to implement a n variable switching function, a MUX must have 2n inputs.
Question 6 |
The throughput of pure ALOHA is given by :
S=G | |
S=e2G | |
S=Ge2G | |
S=Ge-2G |
Question 6 Explanation:
→ The throughput of pure ALOHA is given by S=Ge-2G
→ The throughput of pure ALOHA is given by S=Ge-G
→ The throughput of pure ALOHA is given by S=Ge-G
Question 7 |
The Fiber Distributed Data Interface(FDDI) uses :
single mode fibers and LEDs | |
multimode fibers and LEDs | |
single mode fibers and ILDs | |
multimode fibers and ILDs |
Question 7 Explanation:
→ FDDI uses a multimode fiber because the cost of single mode fiber is not justified for networks running at only 100 Mbps.
→ It also uses LEDs instead of Lasers not only because of the lower cost but also because FDDI may sometimes be used to connect directly to user workstations, and safety against exposure to LASER radiation is difficult to maintain in that case.
→ It also uses LEDs instead of Lasers not only because of the lower cost but also because FDDI may sometimes be used to connect directly to user workstations, and safety against exposure to LASER radiation is difficult to maintain in that case.
Question 8 |
To employ multi-access in GSM, users are given different :
time slots | |
bandpass filters | |
handsets | |
frequency bands |
Question 8 Explanation:
To employ multi-access in GSM, users are given different frequency bands.
Question 9 |
With a four programs in memory and with 80% average I/O wait, the CPU utilization is ?
60% | |
70% | |
90% | |
100% |
Question 9 Explanation:
Given data
-- Average I/O wait=80%
-- Total programs in memory=4
-- CPU Utilization=?
Step-1: To find CPU utilization, we have standard formula is 1-pn
Where,
-- ‘n’ is number of process
-- ‘P’ is waiting time for I/O.
Step-2: CPU Utilization=1-0.84
= 1-0.4096
= 0.5904 (approximation is 60%)
-- Average I/O wait=80%
-- Total programs in memory=4
-- CPU Utilization=?
Step-1: To find CPU utilization, we have standard formula is 1-pn
Where,
-- ‘n’ is number of process
-- ‘P’ is waiting time for I/O.
Step-2: CPU Utilization=1-0.84
= 1-0.4096
= 0.5904 (approximation is 60%)
Question 10 |
Assume N segments in memory and a page size of P bytes. The wastage on account of internal fragmentation is :
NP/2 bytes | |
P/2 Bytes | |
N/2 Bytes | |
NP Bytes |
Question 10 Explanation:
→ The wastage on account of internal fragmentation is NP/2 bytes.
where,
Segments in memory=N
Page size= P bytes.
where,
Segments in memory=N
Page size= P bytes.
Question 11 |
Assertion (A) : Bit maps are not often used in memory management.
Reason (R) :Searching a bitmap for a run of given length is a slow operation.
Reason (R) :Searching a bitmap for a run of given length is a slow operation.
Both (A) and (R) are true and (R) is correct explanation for (A) | |
Both (A) and (R) are true but (R) is not correct explanation for (A) | |
(A) is true (R) is false | |
(A) is false (R) is true |
Question 11 Explanation:
→ Bit maps are not often used in memory management because searching a bitmap for a run of given length is a slow operation.
Question 12 |
The complete graph with four vertices has k edges where k is :
3 | |
4 | |
5 | |
6 |
Question 12 Explanation:
To find number of edges in complete graph using standard formula is n(n-1)/2

n=4
= 4(4-3)/2
= (4*3)/2
= 12/2
= 6
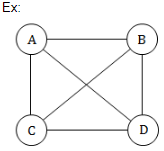
n=4
= 4(4-3)/2
= (4*3)/2
= 12/2
= 6
There are 12 questions to complete.
