HCU PHD CS MAY 2016
Question 1 |
 | |
 | |
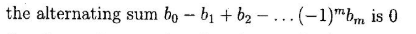 | |
 |
Question 2 |
Which of the following protocols has all of the properties:
(i) imposing restrictions on the order of items being accessed
(ii) ensuring serializability without the requirement of two phase locking, and
(iii) additionally ensuring deadlock freedom.
Three phase locking | |
Timestamp ordering | |
Graph based locking | |
Strict two phase locking |
Question 2 Explanation:
Graph based protocol ensures serializability and deadlock freedom and has restrictions on items being accessed,because before acquiring access to elements we have to acquire lock on parents.
Question 3 |
The property which ensures "once a transaction completes successfully, the changes
it has made to databases persist, even if there are subsequent failures" is called
Atomicity | |
Consistency | |
Isolation | |
Durability |
Question 3 Explanation:
ACID properties in DBMS
Atomicity-This property states that a transaction must be treated as an atomic unit, that is, either all of its operations are executed or none.
Consistency-The database must remain in a consistent state after any transaction. No transaction should have any adverse effect on the data residing in the database. If the database was in a consistent state before the execution of a transaction, it must remain consistent after the execution of the transaction as well.
Isolation- In a database system where more than one transaction are being executed simultaneously and in parallel, the property of isolation states that all the transactions will be carried out and executed as if it is the only transaction in the system. No transaction will affect the existence of any other transaction.
Durability-The database should be durable enough to hold all its latest updates even if the system fails or restarts. If a transaction updates a chunk of data in a database and commits, then the database will hold the modified data. If a transaction commits but the system fails before the data could be written on to the disk, then that data will be updated once the system springs back into action.
Atomicity-This property states that a transaction must be treated as an atomic unit, that is, either all of its operations are executed or none.
Consistency-The database must remain in a consistent state after any transaction. No transaction should have any adverse effect on the data residing in the database. If the database was in a consistent state before the execution of a transaction, it must remain consistent after the execution of the transaction as well.
Isolation- In a database system where more than one transaction are being executed simultaneously and in parallel, the property of isolation states that all the transactions will be carried out and executed as if it is the only transaction in the system. No transaction will affect the existence of any other transaction.
Durability-The database should be durable enough to hold all its latest updates even if the system fails or restarts. If a transaction updates a chunk of data in a database and commits, then the database will hold the modified data. If a transaction commits but the system fails before the data could be written on to the disk, then that data will be updated once the system springs back into action.
Question 4 |
Which of the following is an index mechanism, where an index record appears for
only some of the search key values?
Dense index | |
Sparse index | |
Multi-level index | |
None of these |
Question 4 Explanation:
In Dense Index, an index entry appears for every search-key whereas for Sparse index, an index entry appears for only some of the search-key values.
Question 5 |
In the context of databases SET concept is used in
Relational Model | |
Network Model | |
Hierarchical Model | |
Physical Model |
Question 5 Explanation:
There are two fundamental concepts of a network model :
->Records contain fields which need hierarchical organization.
->Sets are used to define one-to-many relationships between records that contain one owner, many members.
->Records contain fields which need hierarchical organization.
->Sets are used to define one-to-many relationships between records that contain one owner, many members.
Question 6 |
Databases that store information about the state of real world along with timeline are
Temporal databases | |
Mobile databases | |
Multimedia databases | |
Spatial databases |
Question 6 Explanation:
A temporal database stores data relating to time instances. It offers temporal data types and stores information relating to past, present and future time. Temporal databases could be uni-temporal, bi-temporal or tri-temporal. Valid time is the time period during which a fact is true in the real world.
Question 7 |
The condition- “there are no non-trivial functional dependencies of attributes on
anything other than a superset of a candidate key", is both necessary and sufficient
for a database to be in
2nd Normal form | |
3rd Normal form | |
PJNF | |
BCNF |
Question 7 Explanation:
The condition for the relation to be in BCNF is that the left side of functional dependencies must be super key.
Question 8 |
A sequence of length 10 bits is randomly generated. The probability that at least one of these bits is zero is equal to
1023/1024 | |
½ | |
1 | |
9/1024 |
Question 8 Explanation:
Total no. of possible sequences possible
= Each bit can be either 0 ‘or’ 1
= 2 × 2 × 2 … 10times
= 210
= 1024
Now let’s find the probability that none of the bits is 0 = 1/1024
Because out of 1024 only one sequence will contain all bits 1.
So the required probability
= 1 - 1/1024
= 1023/1024
= Each bit can be either 0 ‘or’ 1
= 2 × 2 × 2 … 10times
= 210
= 1024
Now let’s find the probability that none of the bits is 0 = 1/1024
Because out of 1024 only one sequence will contain all bits 1.
So the required probability
= 1 - 1/1024
= 1023/1024
Question 9 |
In a University, 1232 students have taken a course in Spanish, 879 have taken a course in French and 114 have taken a course in Russian. Further, 103 have taken course in both Spanish and Flench, 23 have taken in course both Spanish and Russian, and 14 have taken course in both Flench and Russian, If 2092 students have taken at ]east one of Spanish, French and Russian, how many students have taken a course in all three languages
7 | |
14 | |
23 | |
103 |
Question 9 Explanation:
Let
A = No. of students taken course in French
B = No. of students taken course in Russian
C = No. of students taken course in Spanish
Now, We have to find,
A∩B∩C
Now, the formula we know is
AUBUC = A + B + C - A∩B - B∩C - C∩A + A∩B∩C
= 1232 + 879 + 114 - 103 - 23 - 14 + A∩B∩C
2092 = 2085 + A∩B∩C
A∩B∩C = 7
A = No. of students taken course in French
B = No. of students taken course in Russian
C = No. of students taken course in Spanish
Now, We have to find,
A∩B∩C
Now, the formula we know is
AUBUC = A + B + C - A∩B - B∩C - C∩A + A∩B∩C
= 1232 + 879 + 114 - 103 - 23 - 14 + A∩B∩C
2092 = 2085 + A∩B∩C
A∩B∩C = 7
Question 10 |
The number of different reflexive relations on a set with n elements is
2n(n-1) | |
2n2 | |
n2 | |
2n |
Question 10 Explanation:
No. of total elements in n×n relation = n2
For reflexive relation all the diagonal elements must be there. In total there are n diagonal elements out of n2 and for remaining n2-n elements we have two choices either we can select it or don’t take it. Therefore total no. of reflexive relations possible is,
2 × 2 × 2 × …(n2-n)times
= 2n2-n
For reflexive relation all the diagonal elements must be there. In total there are n diagonal elements out of n2 and for remaining n2-n elements we have two choices either we can select it or don’t take it. Therefore total no. of reflexive relations possible is,
2 × 2 × 2 × …(n2-n)times
= 2n2-n
Question 11 |
p → q is logically equivalent to
~p V Q | |
p V ~q | |
p V q | |
~p V ~q |
Question 11 Explanation:
p → q is logically equivalent to ~p V Q
Question 12 |
What is the output of the following program ?
#include
void main()
{
char ch=1026;
switch(ch) {
Case 1: printf ("Response 1") ; break;
Case 2: printf ("Response 2"); break;
Case 3: printf ("Response 3") ; break;
default: printf ("Default Response" ) ;
}
}
Response 1
| |
Response 2 | |
Response 3 | |
Default Response |
Question 12 Explanation:
The binary value of 1026 is
10000000010
But since char is of 1 byte so, it will consider 8 bits from the right side. Hence the value of char will be
00000010 = 2
So when the switch is executed it will go to case 8 and “Response 2” will get printed.
10000000010
But since char is of 1 byte so, it will consider 8 bits from the right side. Hence the value of char will be
00000010 = 2
So when the switch is executed it will go to case 8 and “Response 2” will get printed.
Question 13 |
What is the output of the following program ?
#include
int main()
{
if(printf ("ABC")) printf ("True") ;
else printf("False");
return 0;
}
Compilation error | |
ABC | |
ABCTrue | |
ABCFalse |
Question 13 Explanation:
Inside the condition of if printf(“ABC”) will return 3 and we know that in if condition anything other than 0 is considered true so it will enter the if loop and will print Tue.Also before that ABC will get printed due to printf(“ABC”). So in total ABCTrue will get printed
Question 14 |
Which of the following declarations are legal ?
I. int a=0, b=1 , c=2; int array[3]={a,b,c};
II. int size = 3; int array[size];
III. int size = 3; int array[size]= {1,2,3};
IV. AII of the above
II and III
| |
I only | |
IV | |
I and II |
Question 14 Explanation:
III is not legal because variable sized object cannot be initialized.
Question 15 |
In the following program which segment is the variable 'p' to be stored
#include
int main()
{
char ch = 'a'; p = & a;
printf ("%c", *p) ;
return 0;
)
Context segment | |
Data segment | |
Stack segment | |
BSS segment |
Question 15 Explanation:
Since p is a local variable for main() function ,so it will be stored in stack section.
Question 16 |
Which of the following is a bottom-up approach to design a database by examining relationships among attributes ?
Functional dependency | |
Database modelling | |
Normalization | |
Decomposition |
Question 16 Explanation:
A well- known approach to database design that can be used as a bottom-up approach is normalization
Question 17 |
Empdt1(emp code,name,street,city,state,pincode)is a schema. For any pincode, there
is only one city and state. AIso for a given street, city and state, there is just one
pincode. In normalization terms, empdtl is a relation in
1NF oniy | |
2NF and hence in lNF | |
3NF and hence also in 2NF and 1NF | |
BCNF and hence also in 3NF and 2NF and 1NF |
Question 17 Explanation:
Given,
Pincode → city, state
Street, city, state → pincode
The candidate keys are
(empcode, name, pincode)
and
(empcode, name, street, city, state)
Since in both the functional dependencies right side is prime attributes but left side is not super keys. So the given relation is in 3NF but not in BCNF.
Pincode → city, state
Street, city, state → pincode
The candidate keys are
(empcode, name, pincode)
and
(empcode, name, street, city, state)
Since in both the functional dependencies right side is prime attributes but left side is not super keys. So the given relation is in 3NF but not in BCNF.
Question 18 |
Which of the following is not associated with transaction processing
Confirming an action or triggering a response | |
Producing detail summary or exception report | |
Recording a business activity | |
Maintaining a data |
There are 18 questions to complete.
