UGC NET CS 2010 Dec-Paper-2
Question 1 |
The number of integers between 1 and 250 that are divisible by 2, 5 and 7 is
2 | |
3 | |
5 | |
8 |
Question 1 Explanation:
Here, we have to find all possible integers between 250 which was divisible by 2,5 and 7.
Solving this problem by 2 methods:
1. Venn diagram
2. Mathematical substitution.
In this problem, we are using Mathematical substitution method.
Step-1: According to condition, we can perform least common multiple(LCM) of 2,5 and 7=70
Step-2: Total number of integers= ⌊250/70⌋
= 3
Note: Divisible numbers are 70,140 and 210.
Solving this problem by 2 methods:
1. Venn diagram
2. Mathematical substitution.
In this problem, we are using Mathematical substitution method.
Step-1: According to condition, we can perform least common multiple(LCM) of 2,5 and 7=70
Step-2: Total number of integers= ⌊250/70⌋
= 3
Note: Divisible numbers are 70,140 and 210.
Question 2 |
An undirected graph possesses an eulerian circuit if and only if it is connected and its vertices are
all of even degree | |
all of odd degree | |
of any degree | |
even in number |
Question 2 Explanation:
→ An undirected graph possesses an eulerian circuit if and only if it is connected and its vertices all of even degree.
→ Eulerian circuit (or) Euler tour in an undirected graph is a cycle that uses each edge exactly once.
→ Eulerian circuit (or) Euler tour in an undirected graph is a cycle that uses each edge exactly once.
Question 3 |
A partially ordered set is said to be a lattice if every two elements in the set have
a unique least upper bound | |
a unique greatest lower bound | |
both (A) and (B) | |
none of the above |
Question 3 Explanation:
A partially ordered set is said to be a lattice if every two elements in the set have
1. Unique least upper bound
2. Unique greatest lower bound
1. Unique least upper bound
2. Unique greatest lower bound
Question 4 |
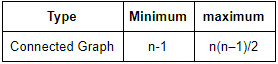
The minimum number of edges in a connected graph with ‘n’ vertices is equal to
n(n – 1) | |
n(n–1)/2 | |
n2 | |
n – 1 |
Question 4 Explanation:
Question 5 |
Consider the problem of connecting 19 lamps to a single electric outlet by using extension cords each of which has four outlets. The number of extension cords required is
4 | |
5 | |
6 | |
7 |
Question 6 |
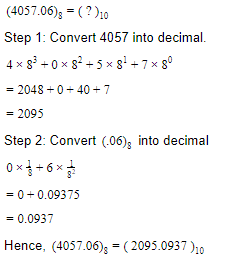
The decimal number equivalent of (4057.06)8 is
2095.75 | |
2095.075 | |
2095.937 | |
2095.0937 |
Question 6 Explanation:
Question 7 |
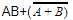 is equivalent to
is equivalent to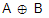 | |
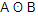 | |
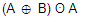 | |
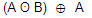 |
Question 7 Explanation:
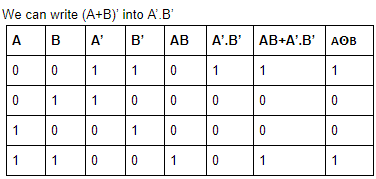
Question 8 |
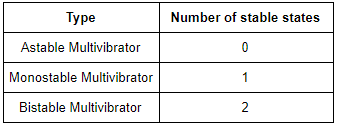
An astable multivibrator has
one stable state | |
two stable states | |
no stable states | |
none of these |
Question 8 Explanation:
Question 9 |
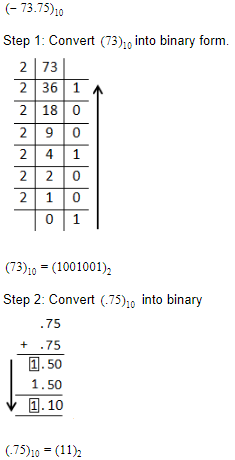
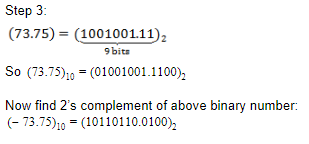
12-bit 2’s complement of –73.75 is
01001001.1100 | |
11001001.1100 | |
10110110.0100 | |
10110110.1100 |
Question 9 Explanation:
Question 10 |
Encoding of data bits 0011 into 7-bit even Parity Hamming Code is
0011110 | |
0101110 | |
0010110 | |
0011100 |
Question 10 Explanation:
(m) Data = 0011
No. of parity bits needed is decided using
2p≥ m+p+1
p=3
Bit pattern:
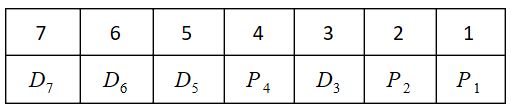
P1(check even parity at 1, 3, 5, 7 bit) = 0
P2(check even parity at 2, 3, 6, 7 bit) = 1
P4(check even parity at 4, 5, 6, 7 bit) = 1
So encoded data = 0011110
No. of parity bits needed is decided using
2p≥ m+p+1
p=3
Bit pattern:

P1(check even parity at 1, 3, 5, 7 bit) = 0
P2(check even parity at 2, 3, 6, 7 bit) = 1
P4(check even parity at 4, 5, 6, 7 bit) = 1
So encoded data = 0011110
Question 11 |
How many of the following declarations are correct ?
int z = 7.0;
double void = 0.000;
short array [2] = {0, 1, 2};
char c = “\n”;
int z = 7.0;
double void = 0.000;
short array [2] = {0, 1, 2};
char c = “\n”;
None | |
One is correct | |
Two are correct | |
All four are correct |
Question 11 Explanation:
int z = 7.0; → Incorrect. Given data type is integer but given floating point number.
It is wrong declaration.
double void = 0.000; → Incorrect. void is a keyword but can’t use with variable declaration.
It always return null value.
short array [2] = {0, 1, 2}; → Correct. It is right format. We can declare static values here itself.
char c = “\n”; → Incorrect. It is character data type but given in double quotes. It should be single quote instead of double quote.
double void = 0.000; → Incorrect. void is a keyword but can’t use with variable declaration.
It always return null value.
short array [2] = {0, 1, 2}; → Correct. It is right format. We can declare static values here itself.
char c = “\n”; → Incorrect. It is character data type but given in double quotes. It should be single quote instead of double quote.
Question 12 |
The value of the following expression (13 / 4 * 3) % 5 + 1 is
5.75 | |
2.95 | |
1.4875 | |
5 |
Question 12 Explanation:
(13 / 4 * 3) % 5 + 1
Step-1: (13 / 4 * 3) % 5 + 1
Step-2: (3.25*3)%5+1
Step-3: 9.75%5+1
Step-4: 4.75+1
Step-5: 5.75
Note: ( ) having highest precedence then *,/ and % have same precedence order.
Step-1: (13 / 4 * 3) % 5 + 1
Step-2: (3.25*3)%5+1
Step-3: 9.75%5+1
Step-4: 4.75+1
Step-5: 5.75
Note: ( ) having highest precedence then *,/ and % have same precedence order.
There are 12 questions to complete.
