APPSC-2016-DL-CA
Question 1 |
What are you predicting by the logic:
∨x:€y:loyalto(x,y)
Everyone is loyal to someone | |
Everyone is loyal to all | |
Everyone is not loyal to someone
| |
Everyone is loyal |
Question 2 |
The field that investigates the mechanics of human intelligence is _______.
Artificial science
| |
Cognitive science | |
Psychology
| |
Sociology |
Question 3 |
A1 computing focus on ______ and conventional computing focus on ______ and ______.
data, information, knowledge | |
information, data, knowledge
| |
knowledge, data, information | |
None of the given options |
Question 4 |
An inference rule that says, if you know x and you know that if x is true, then y is true, then you can conclude y is
Minmax rule | |
Modus Pones rule
| |
Chain rule | |
None of the given options |
Question 5 |
Which one of the following is blind search?
Breadth first search
| |
Depth first search
| |
Breadth first search and Depth first search | |
None of the given options |
Examples of blind search algorithms are:
1. Depth First Search
2. Breadth First Search
3. Uniform Cost Search
Question 6 |
The intelligent agents senses through _______ and take actions through _______.
sensors, actuators | |
remove, signals | |
sensors, actuators and remote, signals
| |
None of the given options
|
Question 7 |
Local maximum Plateau, Ridge are the difficulties in which searching algorithms?
Hill climbing search | |
Best first search | |
Breadth first search | |
None of the given options |
Question 8 |
A* algorithm uses ___________ heuristic function to search any goal node.
admissible function | |
fitness number
| |
evaluation function | |
None of the given options |
Question 9 |
An algorithm, if it is guaranteed to return an optimal solution if it exists, is known as
admissible | |
heuristic | |
optimistic
| |
cognitive |
Question 10 |
AO* algorithm is also known as
Admissible optimal algorithm
| |
Accurate optimistic algorithm | |
And – or algorithm | |
None of the given options |
Question 11 |
Raster systems display a picture from a definition in a _________
Display file program
| |
Frame buffer | |
Display controller | |
None of the given options |
Question 12 |
A bilinear transformation can be simulated by the transformations
Translation, rotation and stretching | |
Translation and rotation
| |
Rotation, stretching and inversion | |
Rotation, stretching, inversion and translation |
Question 13 |
Hue of a colour is related to its ___________
Luminance | |
Saturation | |
Incandescence
| |
Wavelength |
Question 14 |
If the eccentricity is less than one, then conic is a __________
Circle | |
Parabola | |
Ellipse | |
Hyperbola |
Question 15 |
The refresh rate below which a picture flickers is ___________
25 | |
30 | |
35 | |
40 |
Question 16 |
The physical layer of a network _________
Defines the electrical characteristics of signals passed between the computer and communication devices | |
Controls error detection and corrector | |
Constructs packets of data and sends them across the network
| |
All the given options
|
Question 17 |
End-to End connectivity is provided from host-to-host in _________
Session Layer | |
Network Layer | |
Data link Layer
| |
Transport Layer |
Network layer provides host to host connectivity.
Data link layer provides hop to hop connectivity.
Question 18 |
Which layer is not present in TCP/IP Model?
Internet Layer | |
Application Layer | |
Session Layer | |
Transport Layer |
Application layer
Transport layer
Network layer
Data link layer
Physical layer
Question 19 |
Nyquist Theorem to calculate maximum data rate is _______
2H log2 bits/ses | |
H log2 V bits/ses | |
H log2 (1+S/N) | |
2H log2 (1+S/N)
|
Question 20 |
LANs can be connected by devices called _________ which operate in the data link layer?
Hub
| |
Bridges | |
HDCL | |
Tunnel
|
Question 21 |
Two different networks can be connected by using
Satellite | |
Gateway | |
Bridges | |
None of the given options |
Question 22 |
Which of the following is not a Routing Algorithm?
Broadcast | |
Link state | |
Traffic shaping | |
Distance vector
|
Question 23 |
_________ is a device that receives a radio signal, strengthens it, and sends it on.
Repeater | |
WiFi
| |
Hub | |
Microwave |
Question 24 |
What is the main reason for developing ISO/OSI model for networks?
Manufactures disliked the TCP/IP protocol suite | |
The rate of data transfer was increasing exponentially
| |
Standards were needed to allow any two systems to communicate
| |
None of the given options
|
Question 25 |
Which layer functions as a liaison between user support layers and network support layers?
Network layer | |
Physical layer | |
Transport layer | |
Session layer |
Question 26 |
In the IPv-4 addressing format, the number of networks allowed under Class C addresses is
214 | |
221 | |
27 | |
224 |
Question 27 |
Which of the following flip-flops is free from race around problem?
D flip-flop | |
T flip-flop
| |
S-R flip-flop
| |
Master-slave J-K flip-flop |
During high clock when ever applied input changes the output also changes. But in JK flip flop when j=k=1 , without any change in the input the output changes , this condition is called a race around condition. The circuit accepts input data when the clock signal is “HIGH”, and passes the data to the output on the falling-edge of the clock signal. In other words, the Master-Slave JK Flip flop is a “Synchronous” device as it only passes data with the timing of the clock signal.
Question 28 |
The number of full and half adders required to add 16-bit numbers are
8 half adders, 8 full adders | |
1 half adder, 15 full adders | |
16 half adders, 0 full adders | |
half adders, 12 full adders
|
Question 29 |
An example of a tautology is
x ∨ y | |
x ∨ (¬ y) | |
x ∨ (¬ x) | |
(x →y) ^ (x ← y)
|
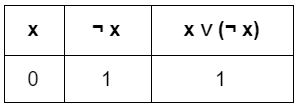
Question 30 |
The idempotent law in the Boolean algebra says that
¬ (¬ x) = x | |
x + x = x | |
x + xy = x | |
x(x + y) = x |
Question 31 |
The proposition (p→q) ^ (¬ q ∨ (p ∨ p) is equivalent to
q → p | |
p → q
| |
(q → p) ∨ (p → q) | |
(p → q) ∧ (q → p) |
= (p->q) ^ (q ->p) (since ¬ q v p = q->p)
Question 32 |
How many flip-flops are required mod – 16 counters?
5 | |
6 | |
3 | |
4 |
So log2 16=4.
Question 33 |
The number of control lines for a 8 to 1 multiplexer is
2 | |
3 | |
4 | |
5 |
Question 34 |
The gray code for decimal number 6 is equivalent
1100 | |
1001 | |
0101 | |
0110 |
The binary value b3, b2, b1, b0 and find the gray code g3, g2, g1, g0 based on the below concept, g3 = b3 = 0
g2 = b3 XOR b2 = 0 xor 1 = 1
g1 = b2 XOR b1 = 1 xor 1 = 0
g0 = b1 XOR b0 = 1 xor 0 = 1
Question 35 |
The gates required to build a half adder are
Ex-OR gate and NOR gate | |
Ex-OR gate and OR gate | |
Ex-OR gate and AND gate | |
Four NAND gates |
Question 36 |
In order to implement an n-variable switching function, a MUX must have
2n inputs | |
2n + inputs | |
2n-1 inputs
| |
2n – 1 inputs |
Question 37 |
The worst case time complexity of Quick Sort is __________
O(n2) | |
O(log n) | |
O(n) | |
O(n logn)
|
The worst case quicksort happens only 2 times
1. Elements are already in sorted order.
2. All elements having the same weight.
