HCU PHD CS MAY 2012
Question 1 |
In DBMS the projection operation creates a new table that has
more tuples than the original table
| |
more attributes than the original table | |
both of A and B above | |
none of the above |
Question 1 Explanation:
In DBMS the projection operation creates a new table that has less than or equal no. of tuples and less no. of attributes than the original table.
Question 2 |
A locked file can be
accessed by a user having correct password | |
accessed by one user | |
used to hide data
| |
none of the above
|
Question 2 Explanation:
File locking is a mechanism that restricts access to a computer file, or to a region of a file, by allowing only one user or process to modify or delete it in a specific time and to prevent reading of the file while it's being modified or deleted.
Question 3 |
The length of a Hamiltonian path (if exists) in a simple connected graph of n vertices is
n+1 | |
n-1 | |
n | |
None of the above |
Question 3 Explanation:
Hamiltonian path is a path in a graph that visits each vertex exactly once.
So if each vertex is visited exactly once then to cover those vertices exactly n-1 edges are required,because if vertices are not repeated then edge will also be not repeated.
So if each vertex is visited exactly once then to cover those vertices exactly n-1 edges are required,because if vertices are not repeated then edge will also be not repeated.
Question 4 |
A network schema is different from a hierarchical schema, for, it allows
one parent - one child | |
one parent - many children | |
many parents - many children | |
both of A and B above only |
Question 4 Explanation:
While the hierarchical database model structures data as a tree of records, with each record having one parent record and many children, the network model allows each record to have multiple parent and child records, forming a generalized graph structure.
Question 5 |
A binary search tree (BST) is built by inserting the following values in the given order: 4,25,15,12,20,70,40. The Post Order. Traversal will be
12, 15, 20, 40,70,25, 4 | |
12, 20,15, 40, 70, 25, 4 | |
4, 25,70, 40, 15, 12,20 | |
4, 12, 15, 20, 25, 40,70 |
Question 5 Explanation:
The given sequence is,
4, 25, 15, 12, 20, 70, 40
Now let’s draw binary search tree for above sequence,

The post order traversal for above BST is,
12, 20, 15, 40, 70, 25, 4.
4, 25, 15, 12, 20, 70, 40
Now let’s draw binary search tree for above sequence,

The post order traversal for above BST is,
12, 20, 15, 40, 70, 25, 4.
Question 6 |
If N is an n-bit number, how many bits long is N!, approximately?
nlogn | |
n! | |
2n | |
n2 | |
None of the given option is correct.The correct answer is n*2^n. |
Question 6 Explanation:

Question 7 |
Which one of these sorting algorithms involves minimum record swaps during execution on an average?
bubble sort | |
insertion sort | |
selection sort | |
quicksort |
Question 7 Explanation:
Selection sort algorithm involves minimum no. of records swap on an average and also in worst case. In selection sort the average or worst case no. of swaps is O(n).
Whereas in Bubble sort tha average no. of swaps is O(n^2) , in insertion sort it is O(n^2), and in quick sort it is O(nlogn).
Whereas in Bubble sort tha average no. of swaps is O(n^2) , in insertion sort it is O(n^2), and in quick sort it is O(nlogn).
Question 8 |
The solution of the recurrence relation T(n)=3T(n/2)+Θ(n), for n ≥ 2, T(1)=0, is
Θ(nlog_2^3) | |
Θ(n log n) | |
Θ(n) | |
Θ(n2) |
Question 8 Explanation:

Question 9 |
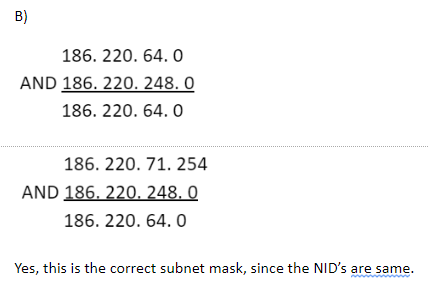
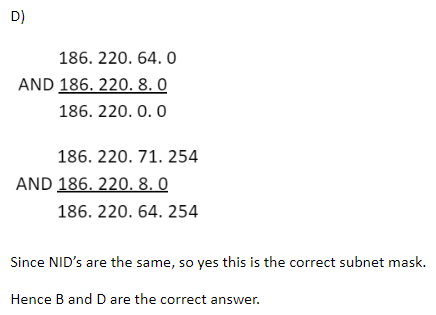
All IP addresses in the range 186.220 .64.0 to 186.220.71.254 arc kept in a VLAN. The correct netmask so that messages are broadcast only within this VLAN is
186.220.255.255 | |
186.220.248.0 | |
186.220.248.255 | |
186.220.8.0 |
Question 9 Explanation:
Let check option wise,






Question 10 |
On a Linux system, a person found that it is possible to display the contents of a file named /usr/foo/public/award.html but could not list the files in the directory using is /usr/foo/public.
The permissions on the directory may have been
rwxr-x--x | |
rwxr-xr-- | |
rwrxr-xr-x | |
None of the Above |
Question 11 |
The first four bytes of a binary file are CA , FE, BA, BE (in Hexadecimal, of course!). What type of a file is it?
MSWindows .exe file | |
IUSWindows .com file | |
Java Class file | |
BNIP Image file |
Question 12 |
For which of the following problems can a Turing Machine not be designed?
Find if there exists a sequence of 7 consecutive 7's in the decimal expansion of 22/7 | |
Find if there exists a sequence of 7 consecutive 7’s in the decimal expansion of π | |
Find if there exists a sequence of 7 consecutive 7’s in the quotient obtained by dividing all positive integers less than 1064 by the number 125 | |
None of the Above |
There are 12 questions to complete.
