GATE 2015 [Set-3]
Question 1 |
Extreme focus on syllabus and studying for tests has become such a dominant concern of Indian students that they close their minds to anything _____ to the requirements of the exam
related | |
extraneous | |
outside | |
useful |
Question 2 |
A function f(x) is linear and has a value of 29 at x = -2 and 39 at x = 3. Find its value at x = 5.
59 | |
45 | |
43 | |
35 |
Question 3 |
The Tamil version of ________ John Abraham-starrer Madras café ________ cleared by the Censor Board with no cuts last week but the film’s distributors _________ no takers among the exhibitors for a release in Tamil Nadu _________ this Friday.
Mr., was, found, on | |
a, was, found, at | |
the, was, found, on | |
a, being, find at |
Question 4 |
If ROAD is written as URDG, then SWAN should be written as:
VXDQ | |
VZDQ | |
VZDP | |
UXDQ |
S+3 = V, W+3 = Z, A+3 = D, N+3 = Q.
Question 5 |
Select the pair that best expresses a relationship similar to that expressed in the pair: Children: Pediatrician
Adult: Orthopedist | |
Females: Gynecologist | |
Kidney: Nephrologist | |
Skin: Dermatologist |
Question 6 |
The exports and imports (in crores of Rs.) of a country from the year 2000 to 2007 are given in the following bar chart. In which year is the combined percentage increase in imports and exports the highest?
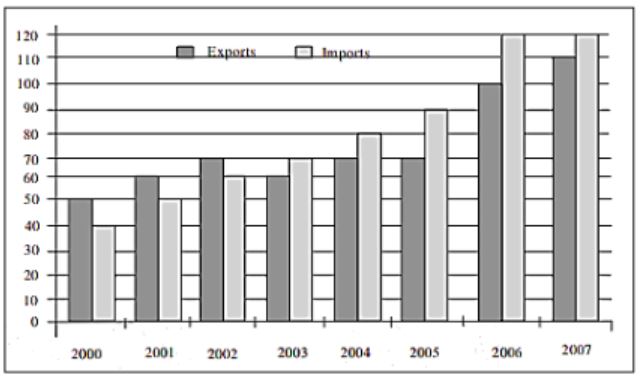
2006 | |
2007 | |
2008 | |
2009 |
Increase in imports in 2006 = 120 - 90/90 = 33.3% which is more than any other year.
Question 7 |
The head of a newly formed government desires to appoint five of the six selected members P, Q, R, S, T and U to portfolios of Home, Power, Defense, Telecom, and Finance. U does not want any portfolio if S gets one of the five. R wants either Home or Finance or no portfolio. Q says that if S gets either Power of telecom, then she must get the other one. T insists on a portfolio if P gets one Which is the valid distribution of portfolios?
P-Home, Q-Power, R-Defense, S-Telecom, T-Finance | |
R-Home, S-Power, P-Defense, Q-Telecom, T-Finance | |
P-Home, Q-Power, T-Defense, S-Telecom, U-Finance | |
Q-Home, U-Power, T-Defense, R-Telecom, P-Finance |
Question 8 |
Choose the most appropriate equation for the function drawn as a thick line, in the plot below
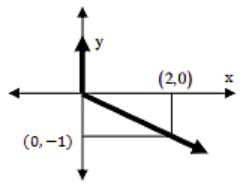
x = y - |y| | |
x = -(y - |y|) | |
x = y + |y| | |
x = -(y + |y|) |
Then the Answer is x = - (y - |y|)
Question 9 |
Most experts feel that in spite of possessing all the technical skills required to be a batsman of the highest order, he is unlikely to be so due to lack of requisite temperament. He was guilty of throwing away his wicket several times after working hard to lay a strong foundation. His critics pointed out that until he addressed this problem, success at the highest level will continue to elude him. Which of the statements(s) below is/are logically valid and can be inferred from the above passage?
- (i) He was already a successful batsman at the highest level.
(ii) He has to improve his temperament in order to become a great batsman.
(iii) He failed to make many of his good starts count.
(iv) Improving his technical skills will guarantee success.
(iii) and (iv) | |
(ii) and (iii) | |
(i), (ii) and (iii) | |
(ii) only |
→ He is unlikely due to lack of requisite temperament ------- (ii) is True
→ He was guilty of throwing away his wicket several times ------- (iii) is True
Question 10 |
Alexander turned his attention towards India, since he had conquered Persia. Which one of the statements below is logically valid and can inferred from the above sentence?
Alexander would not have turned his attention towards India had he not conquered Persia | |
Alexander was not ready to rest on his laurels, and wanted to march to India | |
Alexander was completely in control of his army and could command it to move towards India | |
Since Alexander’s kingdom extended to Indian borders after the conquest of Persia, he was keen to move further |
Y be " he had conquered Persia"
Like that
∼X be "Alexander would not have turned his attention towards India"
then
∼Y be "he had not conquered Persis"
Answer is option A.
Question 11 |
In a room there are only two types of people, namely Type 1 and Type 2. Type 1 people always tell the truth and Type 2 people always lie. You give a fair coin to a person in that room, without knowing which type he is from and tell him to toss it and hide the result from you till you ask for it. Upon asking, the person replies the following:
“The result of the toss is head if and only if I am telling the truth.”
Which of the following options is correct?
The result is head | |
The result is tail
| |
If the person is of Type 2, then the result is tail | |
If the person is of Type 1, then the result is tail |
Case 1:
The person who speaks truth. This definitely implies that result of toss is Head.
Case 2:
The person who lies. In this the reality will be the negation of the statement.
The negation of (x⇔y) is exactly one of x or y holds. "The result of the toss is head if and only if I am telling the truth". So here two possibilities are there,
→ It is head and lie spoken.
→ It is not head and truth spoken.
Clearly, the second one cannot speaks the truth. So finally it is head.
Hence, option (A).
Question 12 |
Consider the relation X(P, Q, R, S, T, U) with the following set of functional dependencies
F = {
{P, R} → {S,T},
{P, S, U} → {Q, R}
} Which of the following is the trivial functional dependency in F+ is closure of F?
{P,R}→{S,T} | |
{P,R}→{R,T} | |
{P,S}→{S} | |
{P,S,U}→{Q} |
Question 13 |
Given a hash table T with 25 slots that stores 2000 elements, the load factor α for T is ___________.
80 | |
70 | |
60 | |
50 |
Question 14 |
Consider a software project with the following information domain characteristic for calculation of function point metric.
-
Number of external inputs (I) = 30
Number of external output (O) = 60
Number of external inquiries (E) = 23
Number of files (F) = 08
Number of external interfaces (N) = 02
It is given that the complexity weighting factors for I, O, E, F and N are 4, 5, 4, 10 and 7, respectively. It is also given that, out of fourteen value adjustment factors that influence the development effort, four factors are not applicable, each of he other four factors have value 3, and each of the remaining factors have value 4. The computed value of function point metric is __________.
612.06 | |
612.07 | |
612.08 | |
612.09 |
Question 15 |
Consider the following statements.
-
I. TCP connections are full duplex.
II. TCP has no option for selective acknowledgment.
III. TCP connections are message streams.
Only I is correct | |
Only I and III are correct | |
Only II and III are correct | |
All of I, II and III are correct |
Question 16 |
Suppose U is the power set of the set S = {1, 2, 3, 4, 5, 6}. For any T ∈ U, let |T| denote the number of element in T and T' denote the complement of T. For any T, R ∈ U, let TR be the set of all elements in T which are not in R. Which one of the following is true?
∀X ∈ U (|X| = |X'|) | |
∃X ∈ U ∃Y ∈ U (|X| = 5, |Y| = 5 and X ∩ Y = ∅) | |
∀X ∈ U ∀Y ∈ U (|X| = 2, |Y| = 3 and X \ Y = ∅) | |
∀X ∈ U ∀Y ∈ U (X \ Y = Y' \ X') |
(A) False. Consider X = {1,2}. Therefore, X' = {3,4,5,6}, |X| = 2 and |X'| = 4.
(B) False. Because for any two possible subsets of S with 5 elements should have atleast 4 elements in common. Hence X∩Y cannot be null.
(C) False. Consider X = {1,4}, Y= {1,2,3} then X\Y = {4} which is not null.
(D) True. Take any possible cases.
![GATE 2015 [Set-3]](https://solutionsadda.in/wp-content/uploads/2019/05/green-new-logo.png)