KVS 30-12-2018 Part B
Question 1 |
An address in the memory is called
physical address | |
logical address | |
memory address | |
word address |
Question 1 Explanation:
A physical address (also real address, or binary address), is a memory address that is represented in the form of a binary number on the address bus circuitry in order to enable the data bus to access a particular storage cell of main memory, or a register of memory mapped I/O device.
Question 2 |
EEPROM is
Efficiently erasable programmable read only memory | |
Electrically erasable programmable read only memory | |
Electronically erasable programmable read only memory | |
Electrically and Electronically programmable read only memory |
Question 2 Explanation:
Electrically Erasable Programmable Read-Only Memory is a type of non-volatile memory used in computers, integrated in microcontrollers for smart cards and remote keyless systems, and other electronic devices to store relatively small amounts of data but allowing individual bytes to be erased and reprogrammed.
Question 3 |
Convert the following octal number into its decimal equivalent: 2 3 7 4 in octal
(10208)10 | |
(1276)10 | |
(2374)10 | |
(1272)10 |
Question 3 Explanation:
(2374)8=2x83+3x82+7x81+4x80=1024+192+56+4=1276
Question 4 |
Which of the following statement/s is/are correct?
- With on-chip decoding, 8 address lines can access 64 memory locations
- With on-chip decoding, 4 address lines can access 64 memory locations
- With on-chip decoding, 8 address lines can access 256 memory locations
- With on-chip decoding, 4 address lines can access 128 memory locations
Only a | |
A and b | |
Only c | |
C and d |
Question 4 Explanation:
->The n address lines consists of 2n memory locations
->8 address lines can access 28 =256 memory locations
->8 address lines can access 28 =256 memory locations
Question 5 |
Represent the decimal number 3.248*104 into a single precision floating point binary number(using standard format).
0|10001101|11111011100000000000000 | |
0|11001101|11111011100000000000000 | |
1|11001101|11111011100000000000000 | |
0|10001110|11111011100000000000000 |
Question 5 Explanation:
Given number is in base 10. Convert it to base-10.
3.248x104 =32480= 1111110111
= 1.111110111 x 214
Mantissa = 11111011100...00
Biased exponent = 14 +127= 141 = 10001101
3.248x104 =32480= 1111110111
= 1.111110111 x 214
Mantissa = 11111011100...00
Biased exponent = 14 +127= 141 = 10001101
Question 6 |
When used with IC, what does he term QUAD indicate?
2 circuits | |
4 circuits | |
6 circuits | |
8 circuits |
Question 6 Explanation:
→A quad gate is an IC (integrated circuit or chip) containing four logic gates. The gates can be of any type: AND, OR, XOR, NOT, NAND, NOR, and XNOR. Within any given quad gate, all four of the individual gates are normally of the same type.
→A logic gate is an elementary building block of a digital circuit.
→A logic gate is an elementary building block of a digital circuit.
Question 7 |
Data can be changed from special code to temporal code by using
Shift Registers | |
Counters | |
Combinational circuits | |
A/D converters |
Question 7 Explanation:
By shift registers , data is can be changed from one code to another code.
Question 8 |
Words having 8 bits are to be stored in computer memory. The number of lines required for writing into the memory are
1 | |
2 | |
4 | |
8 |
Question 8 Explanation:
Each line carries one bit of information.
Question 9 |
A group of bits that tells the computer to perform a specific operation is known as
Instruction code | |
Micro operation | |
Accumulator | |
Register |
Question 9 Explanation:
→An instruction code is a group of bits that instruct the computer to perform a specific operation.
→The operation code of an instruction is a group of bits that define operations such as addition, subtraction, shift, complement, etc.
→An instruction must also include one or more operands, which indicate the registers and/or memory addresses from which data is taken or to which data is deposited.
→The operation code of an instruction is a group of bits that define operations such as addition, subtraction, shift, complement, etc.
→An instruction must also include one or more operands, which indicate the registers and/or memory addresses from which data is taken or to which data is deposited.
Question 10 |
If a value V(x) of the target operand is contained in the field itself, the addressing mode is called
Immediate | |
Direct | |
Indirect | |
Implied |
Question 10 Explanation:
As mentioned in the question “Target operand is contained in the field itself”. It should be immediate addressing mode
Question 11 |
If the address of A[1][1] and A[2][1] are 1000 and 1010 respectively and each element occupies 2 bytes, then the array has been stored in ____ order
Row major order | |
Column major | |
Matrix major | |
Simple |
Question 11 Explanation:
→Row-major order and column-major order are methods for storing multidimensional arrays in linear storage such as random access memory.
→First element address is 1000 and Second element address is 1002 and so on
→A[2][1] means Second row first element whose address is 1010.
→First element address is 1000 and Second element address is 1002 and so on
→A[2][1] means Second row first element whose address is 1010.
Question 12 |
What is the following program segment doing?
main()
{
int d=1;
do
{
printf(“%d”\n”,d++);
}while(d<=9);
}
main()
{
int d=1;
do
{
printf(“%d”\n”,d++);
}while(d<=9);
}
Adding 9 integers | |
Adding integers from 1 to 9 | |
Displaying integers from 1 to 9 | |
No output |
Question 12 Explanation:
The code consists of do-while loop in which action performs first and later condition checking.
In the printf() statement, d++ means first it will display d value and increment the d value later condition checking.So the integer values 1 to 9 will be printed.
In the printf() statement, d++ means first it will display d value and increment the d value later condition checking.So the integer values 1 to 9 will be printed.
Question 13 |
In a computer, keywords of a language are recognized during
Parsing of the program | |
Code generation | |
Lexical analysis of the program | |
Data flow diagrams |
Question 13 Explanation:
Lexical analyzer reads the characters from source code and convert it into tokens.
Different tokens or lexemes are:
→Keywords
→Identifiers
→Operators
→Constants
Different tokens or lexemes are:
→Keywords
→Identifiers
→Operators
→Constants
Question 14 |
If an array is declared as Int a[5]={3,0,1,2}, then values assigned to a[0] and a[4] will be
3,2 | |
0,2 | |
3,0 | |
0,4 |
Question 14 Explanation:
→A[0] is first element and a[4] means 5th element. Array is declared for 5 elements are only four elements are initialized and the default value is 0.
→The first value is 3 and a[4] value is 0
→The first value is 3 and a[4] value is 0
Question 15 |
Consider the following code segment in JAVA
switch(x)
{
default;
system.out.println(“Hello”);
}
Which of the following data types are acceptable for x?
switch(x)
{
default;
system.out.println(“Hello”);
}
Which of the following data types are acceptable for x?
Byte and char | |
Long and char | |
Char and float | |
Byte and float |
Question 15 Explanation:
The possible values are either integer constant or character constant.No other data type values are allowed.
Question 16 |
Which of the following are valid calls to math.max in java?
- Math.max(1,4)
- Math.max(2.3,5)
- Math.max(1,3,5,7)
- Math.max(-1.5,-2.8f)
A,b and d | |
B,c and d | |
A,b and c | |
C and d |
Question 16 Explanation:
→The java.lang.Math.max(int a, int b) returns the greater of two int values.
→We can find the greater of any two data types variables.
→Option C consists of four variables , So it is invalid.
→We can find the greater of any two data types variables.
→Option C consists of four variables , So it is invalid.
Question 17 |
Which of the following is NOT true in C++?
Before a variable can be used, it must be declared | |
Variable are allocated values through the use of assignment statements | |
When a variable is declared, C++ allocates storage for the variable and puts an unknown value inside it. | |
We can use a variable even if it is not declared. |
Question 17 Explanation:
In the c++ (or) C programming language , in order to use the variables in the program we must declare the variables before using.
Question 18 |
What shall be the output of the following program in C++(using turbo C++)?
#include<iostream.h>
float answer;
main()
{
answer=⅓;
cout<<”The value of ⅓ is” <<answer,,”\n”;
return(0);
}
#include<iostream.h>
float answer;
main()
{
answer=⅓;
cout<<”The value of ⅓ is” <<answer,,”\n”;
return(0);
}
The value of ⅓ is 0 | |
The value of ⅓ is 0.33 | |
The value of ⅓ is 0.3333 | |
The value of ⅓ is 1/3 |
Question 18 Explanation:
The expression answer=⅓ , which is integer divide by integer operation .
Modulus operation gives the quotient values when one number is divided by another number .
When 1 is divide by 3, the quotient is o
Modulus operation gives the quotient values when one number is divided by another number .
When 1 is divide by 3, the quotient is o
Question 19 |
What shall be the output of the following code segment in C++?
int main()
{
int x=0,i=4;
switch(i)
{
default:x+=5;
cout<<”x=<<x<<”\n”;
Case 4:x+=4;
cout<<”x=<<x<<”\n”;
Case 1:x+=1;
cout<<”x=<<x<<”\n”;
Case 2:x+=2;
cout<<”x=<<x<<”\n”;
Case 3:x+=3;
cout<<”x=<<x<<”\n”;
}
return 0;
}
int main()
{
int x=0,i=4;
switch(i)
{
default:x+=5;
cout<<”x=<<x<<”\n”;
Case 4:x+=4;
cout<<”x=<<x<<”\n”;
Case 1:x+=1;
cout<<”x=<<x<<”\n”;
Case 2:x+=2;
cout<<”x=<<x<<”\n”;
Case 3:x+=3;
cout<<”x=<<x<<”\n”;
}
return 0;
}
x=4,x=10 | |
x=4 | |
x=10 | |
x=9 |
Question 19 Explanation:
The output of the above program is x=4,x=5,x=7 and x=10 as there is no break statement is the switch case.
From the above options the possible values are 4 and 10 only.
Question 20 |
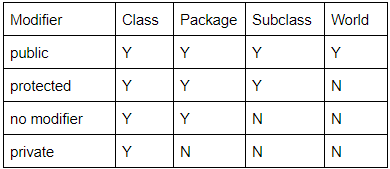
Which of the following is NOT true in case of protected Inheritance in C++?
Each public member in the base class is protected in the derived class | |
Each protected member in the base class is protected in the derived class | |
Each private member in the base class is private in the derived class | |
Each private member in the base class is visible in the derived class |
Question 20 Explanation:
The following table shows the access to members permitted by each modifier.

There are 20 questions to complete.
