TNPSC-2017-Polytechnic-CS
Question 1 |
If there are ‘n’ number of states in NFA, then its equivalent DFA may contain atmost ________ number of states.
2n | |
n | |
n2 | |
2n+1 |
Question 1 Explanation:
If there are ‘n’ number of states in NFA ,then its equivalent DFA may contain atmost 2n number of states.
Question 2 |
To get the PDA, the CFG should be in the form of :
CFG | |
GNF | |
RE | |
CNF |
Question 2 Explanation:
To get the PDA, the CFG should be in the form of GNF.
Question 3 |
One of the uses of CNF is to turn parse tree into :
AVL trees | |
Binary search trees | |
Binary trees | |
None of the above |
Question 3 Explanation:
One of the uses of CNF is to turn parse trees into binary trees. – These trees have some convenient properties, one of which we exploit here.
Theorem 7.17: Suppose we have a parse tree according to a Chomsky- Normal-Form grammar G = (V, T, P, S), and suppose that the yield of the tree is a terminal string w.
Theorem 7.17: Suppose we have a parse tree according to a Chomsky- Normal-Form grammar G = (V, T, P, S), and suppose that the yield of the tree is a terminal string w.
Question 4 |
The grammar A→AA|(A)|∈ is not suitable for predictive parsing because the grammar is:
Ambiguous | |
Left - Recursive | |
Right Recursive | |
An operator grammar |
Question 4 Explanation:
Let’s draw parse tree for string ‘( )’
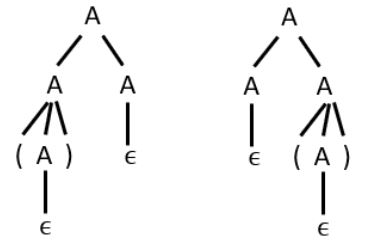
Since for the given string two parse trees are possible. So the given grammar is ambiguous.

Since for the given string two parse trees are possible. So the given grammar is ambiguous.
Question 5 |
The overall logical structure of a database can be expressed graphically by:
Entity relationship model | |
Relation model | |
Object based model | |
Semi structured model |
Question 5 Explanation:
The overall logical data structure of a database can be expressed graphically by an E-R diagram. Which consists of rectangle (entity), ellipse (attribute), diamond (relationship), and lines.
Question 6 |
The relation schema describes:
Set of tuples (Records) | |
Set of fields (Column heads/Attributes) | |
Set of associated values | |
Domain of each field |
Question 6 Explanation:
The relation schema describes set of fields (Column heads/Attributes).
Question 7 |
“X is not a proper subset of any Key” is a 3NF violation called as:
Partial dependency | |
Total dependency | |
Transitive dependency | |
None of the above |
Question 7 Explanation:
If X is not a proper subset of any key means there is no partial dependency. And if there is a violation then the only possibility left is transitive dependency, means if there is transitive dependencies then there is 3NF violation.
Question 8 |
ALL or NONE refers:
Consistency | |
Isolation | |
Durability | |
Atomicity |
Question 8 Explanation:
There are four properties of transactions that must be followed,
A-Atomicity
C-Consistency
I-Isolation
D-Durability
And the question is asking all or none refers to which of the property.
All or None refers to Atomicity.
A-Atomicity
C-Consistency
I-Isolation
D-Durability
And the question is asking all or none refers to which of the property.
All or None refers to Atomicity.
Question 9 |
Inheritance achieved by the key word in SQL is:
of | |
sub | |
under | |
from |
Question 9 Explanation:
Inheritance achieved by the keyword in SQL is ‘under’.
Question 10 |
Which of the following is not specified in Abstract data type?
Type | |
Set of operations on that type | |
How the type is implemented | |
(A) and (B) |
Question 10 Explanation:
An ADT does not specify how the data type is implemented.
Question 11 |
Backtracking uses __________ node generation _____________ bounding functions :
Breadth first, with | |
Breadth first, without | |
Depth-first, with | |
Depth-first, without |
Question 11 Explanation:
Backtracking is a depth-first search with any bounding function.
Question 12 |
Which of the following are not valid IPV4 addresses?
192.10.14.3 | |
200.172.287.33 | |
65.92.11.00 | |
10.34.110.77 |
Question 12 Explanation:
Each octet of IP address has the maximum value of 255. Since in option B, third octet exceeds the value 255,hence invalid.
Question 13 |
In which kind of communication, the destination address in each packet is the same for all duplicate?
Unicasting | |
Multicasting | |
Multiple unicasting | |
Broad casting |
Question 13 Explanation:
In broadcasting communication ,the destination address of all the packets are same since that packet has to be distributed among all the hosts of the network.
Question 14 |
In IPV4, using the classful addressing scheme, the whole address space is divided into how many classes:
8 | |
16 | |
24 | |
5 |
Question 14 Explanation:
There are 5 classful addressing scheme, Class A, Class B, Class C, Class D, Class D, Class E.
Question 15 |
A functional dependency is a relationship between:
Tables | |
Attributes | |
Rows | |
Relations |
Question 15 Explanation:
A functional dependency is a relationship between attributes.
Question 16 |
___________ operator is used to retain the unmatched rows of relations when they joined.
Outer join | |
Inner join | |
Natural join | |
Self join |
Question 16 Explanation:
Outer join operator is used to retain the unmatched rows of relations when they joined.
Question 17 |
The physical location of a record is determined by a mathematical formula that transforms a file key into a record location is:
B – Tree File | |
Hashed File | |
Indexed File | |
Sequential File |
Question 17 Explanation:
The physical location of a record is determined by a mathematical formula, which transforms a file key into a record location in hashed file. Hashing is the transformation of a string of characters into a usually shorter fixed-length value or key that represents the original string.
Question 18 |
Which one of the following statements is FALSE?
A relation with two attributes is in BCNF | |
Lossless dependency preserving decomposition into BCNF is always possible | |
BCNF is stricter than 3NF | |
Lossless, dependency preserving decomposition into 3NF is always possible
|
Question 18 Explanation:
Option B is false because Lossless decomposition into BCNF is always possible but dependency preserving decomposition into BCNF is not always possible.
Question 19 |
The primary objective of formal technical reviews is to:
fix errors | |
find errors | |
clear errors | |
modify errors |
Question 19 Explanation:
Primary objective of formal technical reviews:
Find errors during the process so that they do not become defects after release of the software. Benefit - the early discovery of errors so they do not propagate to the next step in the software process
Find errors during the process so that they do not become defects after release of the software. Benefit - the early discovery of errors so they do not propagate to the next step in the software process
Question 20 |
___________ is a class which implement lower level business abstractions required to manage the business domain class :
User interface class | |
System class | |
Business domain class | |
Process class |
Question 20 Explanation:
Process class is a class which implement lower level business abstractions required to manage the business domain class.
Question 21 |
If there is a Turing machine that enumerates L in canonical order, L is:
ambiguous | |
right – recursive | |
left – recursive | |
recursive |
Question 21 Explanation:
A language L is recursive iff there exists a TM that enumerates L in canonical order.
Question 22 |
Which of the following level of storage is not managed by operating system?
Main memory | |
Solid state disk | |
Cache | |
Magnetic disk |
Question 22 Explanation:
Main memory, cache, magnetic disk are managed by operating system but solid state disk is not managed by operating system.
There are 22 questions to complete.
