UGC NET CS 2014 June-paper-3
Question 1 |
Beam-penetration and shadow-mask are the two basic techniques for producing color displays with a CRT. Which of the following is not true ?
I. The beam-penetration is used with random scan monitors.
II. Shadow-mask is used in raster scan systems.
III. Beam-penetration method is better than shadow-mask method.
IV. Shadow-mask method is better than beam-penetration method.
I and II | |
II and III | |
III only | |
IV only |
Question 1 Explanation:
Beam Penetration Method for displaying color pictures has been used with random-scan monitors. Two layers of phosphor, usually red and green, are coated on to the inside of the CRT screen, and the displayed color depends on how far the electron beam penetrates into the phosphor layers.
Shadow-mask Methods are commonly used in raster-scan systems (including color TV) because they produce a much wider range of color than the beam penetration method. A shadow-mask CRT has three phosphor color dots at each pixel position. One phosphor dot emits a red light, another emits a green light, and the third emits a blue light.
Shadow-mask Methods are commonly used in raster-scan systems (including color TV) because they produce a much wider range of color than the beam penetration method. A shadow-mask CRT has three phosphor color dots at each pixel position. One phosphor dot emits a red light, another emits a green light, and the third emits a blue light.
Question 2 |
Line caps are used for adjusting the shape of the line ends to give them a better appearance. Various kinds of line caps used are
Butt cap and sharp cap | |
Butt cap and round cap | |
Butt cap, sharp cap and round cap | |
Butt cap, round cap and projecting square cap |
Question 2 Explanation:
Line caps helps in improving the appearance of the line by adjusting the shape of line ends There are three types of line caps:
1. But Cap 2. Round Cap 3. Projection Square Cap
1. But Cap 2. Round Cap 3. Projection Square Cap
Question 3 |
Given below are certain output primitives and their associated attributes. Match each primitive with its corresponding attributes :
List – I List – II
a. Line i. Type, Size, Color
b. Fill Area ii. Color, Size, Font
c. Text iii. Style, Color, Pattern
d. Marker iv. Type, Width, Color
a-i, b-ii, c-iii, d-iv | |
a-ii, b-i, c-iii, d-iv | |
a-iv, b-iii, c-ii, d-i | |
a-iii, b-i, c-iv, d-ii |
Question 3 Explanation:
Line Attributes: Basic attributes of a straight line segment are its type, its width, and its color. In some graphics packages, lines can also be displayed using selected pen or brush options.
AREA-FILL ATTRIBUTES: Basic attributes of an area-fill are
Fill Styles: Areas are displayed with three basic fill styles: hollow with a color border, filled with a solid color, or Wed with a specified pattern or design.
Pattern Fill
Soft Fill: the linear soft-fill algorithm repaints an area that was originally painted by merging a foreground color F with a single background color 8, where F + B.The current RGB color P of each pixel within the area to be refilled is some linear combination of F and B:
P = tF + (1- t)B
where the "transparency" factor t has a value between 0 and 1 for each pixel. RGB component of the colors
P = (PR, PC, PR), F = (FR, Fc, FR), B = (BR, Bc, BB)
Text Attributes: Following are the text attributes:
Font : is the choice of font (or typeface), which is a set of characters with a particular design style such as New York, Courier, Helvetica, London, 'Times Roman, and various special symbol groups.
Font size
Font colour
Marker Attributes: A marker symbol is a single character that can be displayed in different colors and in different sizes. We select a particular character to be the marker symbol with
setMarkerType (int)
Hence Marker attributes are type, size and color.
AREA-FILL ATTRIBUTES: Basic attributes of an area-fill are
Fill Styles: Areas are displayed with three basic fill styles: hollow with a color border, filled with a solid color, or Wed with a specified pattern or design.
Pattern Fill
Soft Fill: the linear soft-fill algorithm repaints an area that was originally painted by merging a foreground color F with a single background color 8, where F + B.The current RGB color P of each pixel within the area to be refilled is some linear combination of F and B:
P = tF + (1- t)B
where the "transparency" factor t has a value between 0 and 1 for each pixel. RGB component of the colors
P = (PR, PC, PR), F = (FR, Fc, FR), B = (BR, Bc, BB)
Text Attributes: Following are the text attributes:
Font : is the choice of font (or typeface), which is a set of characters with a particular design style such as New York, Courier, Helvetica, London, 'Times Roman, and various special symbol groups.
Font size
Font colour
Marker Attributes: A marker symbol is a single character that can be displayed in different colors and in different sizes. We select a particular character to be the marker symbol with
setMarkerType (int)
Hence Marker attributes are type, size and color.
Question 4 |
Consider a window bounded by the lines : x = 0; y= 0; x = 5 and y = 3. The line segment joining (–1, 0) and (4, 5), if clipped against this window will connect the points
(0, 1) and (2, 3) | |
(0, 1) and (3, 3) | |
(0, 1) and (4, 3) | |
(0, 1) and (3, 2) |
Question 4 Explanation:


Question 5 |
Which of the following color models are defined with three primary colors ?
RGB and HSV color models | |
CMY and HSV color models | |
HSV and HLS color models | |
RGB and CMY color models |
Question 5 Explanation:
Common color models defined with three primary colors are the RGB and CMY models.
RGB: color scheme is an additive model. Intensities of the primary colors are added to produce other colors. Each color point within the bounds of the cube can be represented as a triple (R, G, B), where values for R, G, and B are assigned in the range from 0 to 1. Thus, a color C, is expressed in RGB components as
C = RR + GG + BB
CMY: A color model defined with the primary colors cyan, magenta, and yellow (CMY) is useful for describing color output to hard-copy devices. We can express the conversion from an RGB representation to a CMY representation with the matrix transformation:

RGB: color scheme is an additive model. Intensities of the primary colors are added to produce other colors. Each color point within the bounds of the cube can be represented as a triple (R, G, B), where values for R, G, and B are assigned in the range from 0 to 1. Thus, a color C, is expressed in RGB components as
C = RR + GG + BB
CMY: A color model defined with the primary colors cyan, magenta, and yellow (CMY) is useful for describing color output to hard-copy devices. We can express the conversion from an RGB representation to a CMY representation with the matrix transformation:

Question 6 |
In a digital transmission, the receiver clock is 0.1 percent faster than the sender clock. How many extra bits per second does the receiver receive if the data rate is 1 Mbps?
10 bps | |
100 bps | |
1000 bps | |
10000 bps |
Question 6 Explanation:

Question 7 |
Given U={1,2,3,4,5,6,7}
A={(3,0.7),(5,1),(6,0.8)}
then ~A will be: (where ~ → complement)
{(4,0.7), (2,1), (1,0.8)} | |
{(4,0.3), (5,0), (6,0.2)} | |
{(1,1), (2,1), (3, 0.3), (4, 1), (6, 0.2), (7, 1)} | |
{(3, 0.3), (6.0.2)} |
Question 7 Explanation:

Question 8 |
Consider a fuzzy set old as defined below Old = {(20, 0.1), (30, 0.2), (40, 0.4), (50, 0.6), (60, 0.8), (70, 1), (80, 1)} Then the alpha-cut for alpha = 0.4 for the set old will be
{(40, 0.4)} | |
{50, 60, 70, 80} | |
{(20, 0.1), (30, 0.2)} | |
{(20, 0), (30, 0), (40, 1), (50, 1), (60, 1), (70, 1), (80, 1)} |
Question 8 Explanation:
If the membership of an element is greater than or equal to alpha-cut value then its membership will become one in the resultant set otherwise it’s membership will be zero(i.e. Will not be a member of the resulting set).
Here alpha = 0.4
So new set = {(20, 0), (30, 0), (40, 1), (50, 1), (60, 1), (70, 1), (80, 1)}
OR
{(40, 1), (50,1), (60.1), (70,1), (80,1)}
Here alpha = 0.4
So new set = {(20, 0), (30, 0), (40, 1), (50, 1), (60, 1), (70, 1), (80, 1)}
OR
{(40, 1), (50,1), (60.1), (70,1), (80,1)}
Question 9 |
Perceptron learning, Delta learning and LMS learning are learning methods which falls under the category of
Error correction learning – learning with a teacher | |
Reinforcement learning – learning with a critic | |
Hebbian learning | |
Competitive learning – learning without a teacher |
Question 10 |
Match the following with respect to the jump statements :
List – I List – II
a. return i. The conditional test and increment portions
b. goto ii. A value associated with it
c. break iii. Requires a label for operation
d. continue iv. An exit from only the innermost loop
a-ii, b-iii, c-iv, d-i | |
a-iii, b-iv, c-i, d-ii | |
a-iv, b-iii, c-ii, d-i | |
a-iv, b-iii, c-i, d-ii |
Question 10 Explanation:
The return statement terminates the execution of a function and returns control to the calling function. Execution resumes in the calling function at the point immediately following the call. A return statement can also return a value to the calling function.
Goto statement: The goto statement transfers the program control directly to a labeled statement.A common use of goto is to transfer control to a specific switch-case label or the default label in a switch statement. The goto statement is also useful to get out of deeply nested loops.
Break statement: The break statement terminates the execution of the nearest enclosing do, for, switch, or while statement in which it appears. Control passes to the statement that follows the terminated statement.
Continue statement: The continue statement passes control to the next iteration of the nearest enclosing do, for, or while statement in which it appears, bypassing any remaining statements in the do, for, or while statement body.
Goto statement: The goto statement transfers the program control directly to a labeled statement.A common use of goto is to transfer control to a specific switch-case label or the default label in a switch statement. The goto statement is also useful to get out of deeply nested loops.
Break statement: The break statement terminates the execution of the nearest enclosing do, for, switch, or while statement in which it appears. Control passes to the statement that follows the terminated statement.
Continue statement: The continue statement passes control to the next iteration of the nearest enclosing do, for, or while statement in which it appears, bypassing any remaining statements in the do, for, or while statement body.
Question 11 |
The control string in C++ consists of three important classifications of characters
Escape sequence characters, Format specifiers and Whitespace characters | |
Special characters, White-space characters and Non-white space characters | |
Format specifiers, White-space characters and Non-white space characters | |
Special characters, White-space characters and Format specifiers |
Question 12 |
Code blocks allow many algorithms to be implemented with the following parameters :
clarity, elegance, performance | |
clarity, elegance, efficiency | |
elegance, performance, execution | |
execution, clarity, performance |
Question 12 Explanation:
Algorithm to be implemented should be:
Clear: Clear means it should convey the exact work you are trying to accomplish.
Clear: Clear means it should convey the exact work you are trying to accomplish.
Question 13 |
Match the following with respect to I/O classes in object oriented programming :
List – I List – II
a. fopen() i. returns end of file
b. fclose() ii. return for any problem report
c. ferror() iii. returns 0
d. feof() iv. returns a file pointer
a-iv, b-i, c-ii, d-iii | |
a-iii, b-i, c-iv, d-ii | |
a-ii, b-iii, c-iv, d-i | |
a-iv, b-iii, c-i, d-ii |
Question 13 Explanation:
fopen() → returns a file pointer
fclose() → returns end of file
ferror() → return for any problem report
feof() → returns 0
fclose() → returns end of file
ferror() → return for any problem report
feof() → returns 0
Question 14 |
Which one of the following describes the syntax of prolog program ?
I. Rules and facts are terminated by full stop (.)
II. Rules and facts are terminated by semicolon (;)
III. Variables names must start with upper case alphabets.
IV. Variables names must start with lower case alphabets.
I, II | |
III, IV | |
I, III | |
II, IV |
Question 14 Explanation:
Rules:


Question 15 |
Let L be any language. Define even (W) as the strings obtained by extracting from W the letters in the even-numbered positions and even(L) = {even (W) | W ∈ L}. We define another language Chop (L) by removing the two leftmost symbols of every string in L given by Chop(L) = {W | ν W ∈ L, with | ν | = 2}. If L is regular language then
even(L) is regular and Chop(L) is not regular. | |
Both even(L) and Chop(L) are regular. | |
even(L) is not regular and Chop(L) is regular. | |
Both even(L) and Chop(L) are not regular. |
Question 16 |
Software testing is
the process of establishing that errors are not present. | |
the process of establishing confidence that a program does what it is supposed to do. | |
the process of executing a program to show that it is working as per specifications. | |
the process of executing a program with the intent of finding errors. |
Question 16 Explanation:
Software testing is the process of executing a program with the intent of finding errors.
Question 17 |
Assume that a program will experience 200 failures in infinite time. It has now experienced 100 failures. The initial failure intensity was 20 failures/CPU hr. Then the current failure intensity will be
5 failures/CPU hr | |
10 failures/CPU hr. | |
20 failures/CPU hr. | |
40 failures/CPU hr. |
Question 17 Explanation:

Question 18 |
Consider a project with the following functional units :
Number of user inputs = 50
Number of user outputs = 40
Number of user enquiries = 35
Number of user files = 06
Number of external interfaces = 04
Assuming all complexity adjustment factors and weighing factors as average, the function points for the project will be
135 | |
722 | |
675 | |
672 |
Question 18 Explanation:
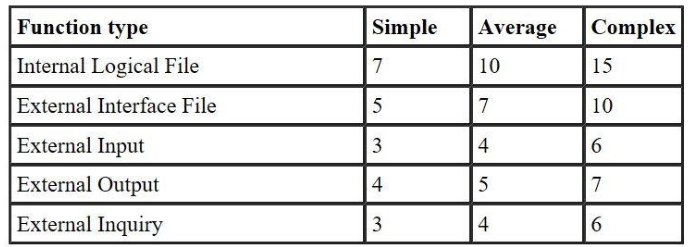 UFP= (50*4)+ ( 40*5)+(35*4)+(6*10)+(4*7)
UFP= (50*4)+ ( 40*5)+(35*4)+(6*10)+(4*7)UFP= 628
CAF = 0.65 + ( 0.01 * F )
F = 14 * scale
Since weighing factor is given as average. So scale value= 3
F= 42.
CAF = 1.07
FP= UFP* CAF
FP= 628*1.07
FP= 671.96
FP= 672(approximately)
There are 18 questions to complete.
