CIL Part - B
Question 1 |
Which of the following statements is TRUE?
The cardinality ratio for a binary relationship specifies the maximum number of relationship instances that an entity can participate in. | |
The cardinality ratio for a binary relationship specifies the minimum number of relationship instances that an entity can participate in. | |
The partial participation constraint is also called existence dependency. | |
The cardinality ratio for a relationship specifies the average number of relationship instances that an entity can participate in. |
Question 1 Explanation:
Cardinality: cardinality ratio for a binary relationship specifies the maximum number of relationship instances that an entity can participate in.
Participation: Participation for a binary relationship specifies the minimum number of relationship instances that an entity can participate in.
Participation: Participation for a binary relationship specifies the minimum number of relationship instances that an entity can participate in.
Question 2 |
Which of the following represents the function of a Multiplexer?
Y= A+ B | |
Y = A | B | |
Y = A & B | |
Y = S ? A : B |
Question 2 Explanation:
Multiplexer : It also known as a data selector, is a device that selects between several input signals and forwards it to a single output line. A multiplexer of 2n inputs has n select lines, which are used to select which input line to send to the output. Here in fourth option “S” is used as select line to select either “A” or “B”.
A multiplexer can be used to implement if-else statements.
A multiplexer can be used to implement if-else statements.
Question 3 |
The prefix equivalent of the following infix expression is:
a / b - c + d * e - a * c
- + - / a b c * d e * a c | |
+ - - / a b c * d e * a c | |
- + / a b c - * d e * a c | |
- - + / a b c * d e * a c |
Question 3 Explanation:
a / b - c + d * e - a * c
* Start scanning the expression from RHS. * Push the operators on the top of the stack by ensuring that only high priority operator can be pushed over a low priority operator.
* If a low priority operator is encountered in expression while scanning it, and if top of stack have high priority operator then pop it and after that push low priority operator on top of stack.
* Print each operand just after scanning it.





* Start scanning the expression from RHS. * Push the operators on the top of the stack by ensuring that only high priority operator can be pushed over a low priority operator.
* If a low priority operator is encountered in expression while scanning it, and if top of stack have high priority operator then pop it and after that push low priority operator on top of stack.
* Print each operand just after scanning it.


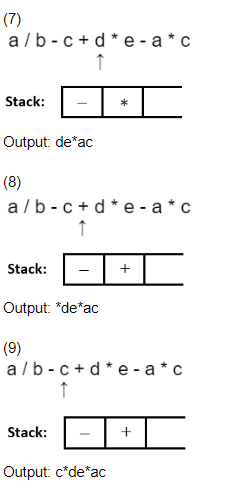
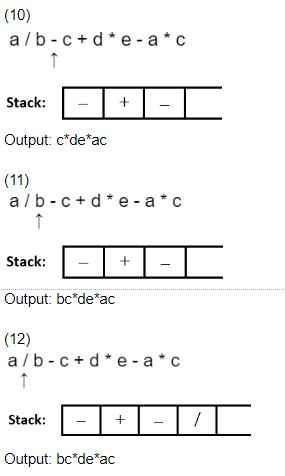

Question 4 |
Which of the following file type arguments is used in fopen() llibrary function to open a new file for both reading and writing and destroys the file if a file with the specified file-name already exists in the current directory ?
“w” | |
“w+” | |
“a+” | |
“r+” |
Question 4 Explanation:
W+ : Create a text file for both reading and writing. If the given file exists, its contents are cleared unless it is a logical file.
A+ : Open a text file in append mode for reading or updating at the end of the file. The fopen() function creates the file if it does not exist.
W : Create a text file for writing. If the given file exists, its contents are destroyed unless it is a logical file.
A : Open a text file in append mode for writing at the end of the file. The fopen() function creates the file if it does not exist and is not a logical file.
R+ : Open a text file for both reading and writing. The file must exist.
A+ : Open a text file in append mode for reading or updating at the end of the file. The fopen() function creates the file if it does not exist.
W : Create a text file for writing. If the given file exists, its contents are destroyed unless it is a logical file.
A : Open a text file in append mode for writing at the end of the file. The fopen() function creates the file if it does not exist and is not a logical file.
R+ : Open a text file for both reading and writing. The file must exist.
Question 5 |
Which of the following statements about IPv6 is FALSE?
IPSec support is an integral part of IPv6. | |
IPv6 has no way to distinguish delay-sensitive packets from bulk data transfers. | |
In comparison to IPA. IPv6 has improved header structure with less processing overhead. | |
IPv6 routers no longer have to fragment packets. |
Question 5 Explanation:
TRUE: IPSec support is an integral part of IPv6.
TRUE: IPv6 has no way to distinguish delay-sensitive packets from bulk data transfers.
FALSE: In comparison to IPA. IPv6 has improved header structure with less processing overhead.
An independent physician association (IPA) is a business entity organized and owned by a network of independent physician practices for the purpose of reducing overhead or pursuing business ventures such as contracts with employers, accountable care organizations (ACO) and/or managed care organizations (MCOs). There are substantial opportunities for innovation in delivery system modeling and benefit design in the creation of physician networks. Specifically, creation of practice networks involving patient-centered medical home (PCMH) practices may accelerate important and necessary changes in health care delivery.
TRUE: IPv6 routers no longer have to fragment packets.
TRUE: IPv6 has no way to distinguish delay-sensitive packets from bulk data transfers.
FALSE: In comparison to IPA. IPv6 has improved header structure with less processing overhead.
An independent physician association (IPA) is a business entity organized and owned by a network of independent physician practices for the purpose of reducing overhead or pursuing business ventures such as contracts with employers, accountable care organizations (ACO) and/or managed care organizations (MCOs). There are substantial opportunities for innovation in delivery system modeling and benefit design in the creation of physician networks. Specifically, creation of practice networks involving patient-centered medical home (PCMH) practices may accelerate important and necessary changes in health care delivery.
TRUE: IPv6 routers no longer have to fragment packets.
Question 6 |
Which of the following does not represent the total number of multiplications for multiplying four matrices of orders
20*2,2*30, 30*12 and 12*8?
1232 | |
3680 | |
10320 | |
8850 |
Question 6 Explanation:
Optimal Parenthesization is : (A((BC)D))
Optimal Cost is : 1232
Optimal Cost is : 1232
Question 7 |
To schedules are said to be______. If the order of any two conflicting operations is same in both the schedules.
conflict equivalent | |
schema equivalent | |
result equivalent | |
view equivalent |
Question 7 Explanation:
View-serializability of a schedule is defined by equivalence to a serial schedule (no overlapping transactions) with the same transactions, such that respective transactions in the two schedules read and write the same data values ("view" the same data values).
Conflict-serializability is defined by equivalence to a serial schedule (no overlapping transactions) with the same transactions, such that both schedules have the same sets of respective chronologically ordered pairs of conflicting operations (same precedence relations of respective conflicting operations).
Conflict-serializability is defined by equivalence to a serial schedule (no overlapping transactions) with the same transactions, such that both schedules have the same sets of respective chronologically ordered pairs of conflicting operations (same precedence relations of respective conflicting operations).
Question 8 |
Which of the following data structures allows both addition and deletion of items from either end?
Double Ended Queue | |
Queue | |
Priority Queue | |
Stack |
Question 8 Explanation:
Double Ended Queue: It is abbreviated to deque and it is an abstract data type that generalizes a queue, for which elements can be added to or removed from either the front (head) or back (tail). It is also often called a head-tail linked list
Stack: Stack is an abstract data type that serves as a collection of elements, with two principal operations:
->push, which adds an element to the collection, and
->pop, which removes the most recently added element that was not yet removed.
Both PUSH and POP operations are done from a single end.The order in which elements come off a stack gives rise to its alternative name, LIFO (last in, first out).
Queue: a queue is a collection of entities that are maintained in a sequence and can be modified by the addition of entities at one end of the sequence and removal from the other end of the sequence. It allows addition and deletion of items from fixed different ends.
Stack: Stack is an abstract data type that serves as a collection of elements, with two principal operations:
->push, which adds an element to the collection, and
->pop, which removes the most recently added element that was not yet removed.
Both PUSH and POP operations are done from a single end.The order in which elements come off a stack gives rise to its alternative name, LIFO (last in, first out).
Queue: a queue is a collection of entities that are maintained in a sequence and can be modified by the addition of entities at one end of the sequence and removal from the other end of the sequence. It allows addition and deletion of items from fixed different ends.
Question 9 |
Considering the relation schemas R (A, B, C, D) and S (C. D. E. F), what will be the degree of the resultant relation of the following Relational Algebra expression. Where “*” represents the”natural join" operation?
3 | |
4 | |
6 | |
5 |
Question 10 |
Which of the following will be the encoding of string “aabaabaca" using Huffman's coding?
110111011001 | |
110111011111 | |
110111111001 | |
110011011011 |
Question 10 Explanation:
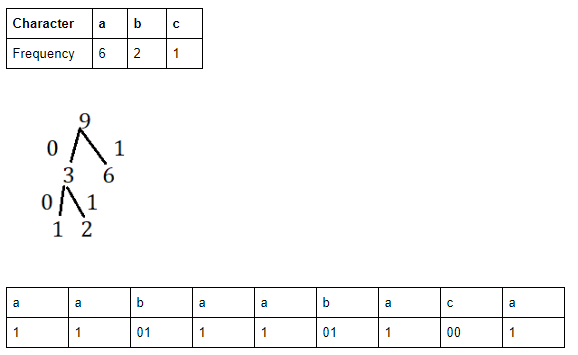
Question 11 |
Which of the following is the time complexity of dynamic programming algorithm to compute the Binomial coefficient nCk?
Θ(nk) | |
Θ(kn) | |
Θ(nk) | |
Θ(n+k) |
Question 11 Explanation:
Optimal Substructure: The value of C(n, k) can be recursively calculated using following standard formula for Binomial Coefficients.
C(n, k) = C(n-1, k-1) + C(n-1, k)
C(n, 0) = C(n, n) = 1
Time Complexity: O(nk)
Space complexity: O(nk)
C(n, k) = C(n-1, k-1) + C(n-1, k)
C(n, 0) = C(n, n) = 1
Time Complexity: O(nk)
Space complexity: O(nk)
Question 12 |
Which of the following constraints enforces that the value of the primary key cannot be Null?
Key Constraint | |
Foreign key constraint | |
Entity integrity constraint | |
Domain constraint |
Question 12 Explanation:
The entity integrity constraint states that primary key value can't be null. This is because the primary key value is used to identify individual rows in relation and if the primary key has a null value, then we can't identify those rows.
Question 13 |
Two concurrent processes P and Q execute the following code.
Process P;
while(True){
W:_____
print(’0’);print(’0’);
X:______
}
Process Q;
while(True){
Y:_____
print(’1’);print(’1’);
Z:______
}
Given S and T are binary semaphore variables, and P() and V() as standard “wait“ and “signal” functions respectively.
What should be the semaphore operations W,X,Y and Z for the output string: 11001100…?
W=P(T),X=V(S),Y=P(S),Z=V(T),S=1,T=0 | |
W=P(T),X=V(S),Y=P(S),Z=V(T),S=T=1 | |
W=P(T),X=V(T),Y=P(S),Z=V(S),S=T=1 | |
W=P(T),X=V(T),Y=P(S),Z=V(S),S=1, T=0 |
Question 13 Explanation:
Process P will be executed first and then Process Q can be executed next.
At the process P: W=P(T)
X=V(S)
At the process Q: Y=P(S)
Z=V(T)
Here, S=0, T=1 then the process P executes first and then Q, and both can run on process alternate way start with P.
At the process P: W=P(T)
X=V(S)
At the process Q: Y=P(S)
Z=V(T)
Here, S=0, T=1 then the process P executes first and then Q, and both can run on process alternate way start with P.
Question 14 |
The output of the following 'C' language code is:
void main(){
int x=1, i , y=2;
for(i=0;i<10;i++)
{
x<<1;
y=x+i;
}
printf("%d.%d”,x.y);
}
10,11 | |
1,1 | |
10,1
| |
1,10 |
Question 14 Explanation:
Question 15 |
Which of the following protocols is built on client-server architecture and uses separate control and data connections between the client and the server?
FTP | |
SMTP | |
POP | |
TELNET |
Question 15 Explanation:
FTP protocols is built on client-server architecture and uses separate control and data connections between the client and the server
Question 16 |
An organization has a Class B network and wishes to form subnets for 60 departments. The subnet mask would be:
255.255.64.0 | |
255.255.0.0 | |
255.255.252.0 | |
255.255.255.0 |
Question 16 Explanation:
Organization have 60 departments, and to assign 60 subnet we need 6 bits for subnet. In Class B network first two octet are reserved for NID, so we take first 6 bit of third octet for subnets and subnet mask would be 255.255.11111100.00000000 = 255.255.252.0
Question 17 |
Which of the following is an NP -complete problem?
Turing's Halting problem | |
CNF-Satisfiability problem | |
Presburger Arithmetic problem | |
Number of Hamiltonian circuits in a complete graph of ‘n’ vertices with n>2 |
Question 17 Explanation:
CNF-Satisfiability problem belongs to NP-Complete.
Question 18 |
Which of the following is/are FALSE?
I) Operator precedence parser works on ambiguous grammar
II) Top-down parser works on left recursive, unambiguous and deterministic grammar
III) LL(I) is a non-recursive descent parser
IV) CLR(I) is the most powerful parser
Only II | |
I, II, III and IV | |
ll and IV | |
I, III and IV |
Question 18 Explanation:
I) TRUE: Operator precedence parser works on ambiguous grammar
II) FALSE: Top-down parser works on left recursive, unambiguous and deterministic grammar
Ill) TRUE: LL(I) is a non-recursive descent parser
IV) TRUE: CLR(I) is the most powerful parser
II) FALSE: Top-down parser works on left recursive, unambiguous and deterministic grammar
Ill) TRUE: LL(I) is a non-recursive descent parser
IV) TRUE: CLR(I) is the most powerful parser
Question 19 |
The data type of the variable "var1 " declared in the following 'C' language statement is:
unsigned var1:
int | |
double | |
char | |
float |
Question 19 Explanation:
By default unsigned variables will consider integer data type.
Question 20 |
Which of the following problem cannot be solved using greedy approach?
0-1 knapsack | |
Job scheduling | |
Minimum spanning tree | |
Huffman code |
Question 20 Explanation:
Greedy Problems:
1. Job scheduling
2. Minimum spanning tree
3. Huffman code
Dynamic Programming:
1. O/1 knapsack
2. Optimal Binary search tree
3. Matrix chain multiplication
1. Job scheduling
2. Minimum spanning tree
3. Huffman code
Dynamic Programming:
1. O/1 knapsack
2. Optimal Binary search tree
3. Matrix chain multiplication
Question 21 |
The decimal number 395, when converted into binary occupies______binary digits, whereas when it is represented using BCD codes using BCD codes, occupies_____ binary digits.
12; 9 | |
7; 12 | |
9; 12 | |
12; 7 |
Question 21 Explanation:
Decimal Number= (395)10 =(110001011)2 =(613)8 = (18B)16
Total 9 digits of binary number required to convert decimal number
Total 9 digits of binary number required to convert decimal number
Question 22 |
Match the following.
List I List II
I)Attenuation P) Loss of energy
II)Shannon capacity Q) Changes in shape of the signal
Ill)Nyquist bit rate R) Noisy channel
IV)Distortion S) Noiseless channel
I-P, II-Q,III-R,IV-S | |
I-P, II-R,III-S,IV-Q | |
I-S, II-R,III-Q,IV-P | |
I-Q, II-P,III-S,IV-R |
Question 22 Explanation:
Attenuation → Changes in shape of the signal
Shannon capacity → Noisy channel
Nyquist bit rate → Noiseless channel
Distortion → Loss of energy
Shannon capacity → Noisy channel
Nyquist bit rate → Noiseless channel
Distortion → Loss of energy
Question 23 |
Which of the following relation schema is always in BCNF?
R( A,B,C,D) | |
R( A,B,C) | |
R( A,B,C,D,E) | |
R( A,B) |
Question 23 Explanation:
BCNF Properties:
1. BCNF is the advance version of 3NF. It is stricter than 3NF.
2. A table is in BCNF if every functional dependency X → Y, X is the super key of the table.
3. For BCNF, the table should be in 3NF, and for every FD, LHS is super key.
4. Two (or) Binary tuples are always be in BCNF
1. BCNF is the advance version of 3NF. It is stricter than 3NF.
2. A table is in BCNF if every functional dependency X → Y, X is the super key of the table.
3. For BCNF, the table should be in 3NF, and for every FD, LHS is super key.
4. Two (or) Binary tuples are always be in BCNF
Question 24 |
Let k2,2 be a complex bipartite graph given below. Which of the following is the total number of paths of length 3 from vertex 1 to vertex 4?

2 | |
3 | |
4 | |
1 |
Question 25 |
Consider the list of numbers 1, 2, 3, ..., 1000 is stored in a[0..999]. What will be the total number of comparisons to search x = 501 using the following binary_search() function?
int binary_search(int a[ ], int n, int x)
{
int low=0, high=n-1;
while(low <= high)
{
int m = (low + high) /2:
if(x > a[m])
low = m+1;
else if(x < a[m])
high= m-1:
else
return m;
}
return -1;
}
2 | |
15 | |
17 | |
1 |
There are 25 questions to complete.
