CIL 2020
Question 1 |
A____is a pictorial depiction of the schema of a database that shows the relations in the databases, their attributes, and primary keys and foreign keys.
Relational query languages | |
Relational algebra
| |
Flow diagram | |
Schema Diagram |
A database schema can be represented in a visual diagram, which shows the database objects and their relationship with each other.
Question 2 |
Consider the following table of arrival time and burst time for three processes P0,P1,P2
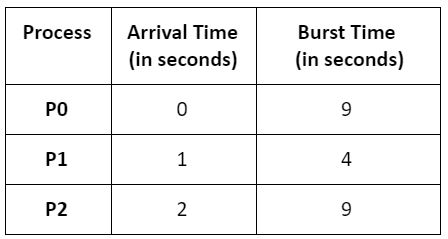
The preemptive shortest job first scheduling algorithm is used scheduling is carried out only at arrival or completion of process. The average waiting time for three process is____.
7 Seconds | |
4 seconds
| |
6 seconds
| |
5 seconds |

∴ Avg. WT = 4+0+11/3 = 5
Question 3 |
According to boolean law: (A')' = ?
0 | |
A | |
(A')'
| |
1 |
Since in the question complement of variable is done 2 times which is even, so will give the same variable.
Question 4 |
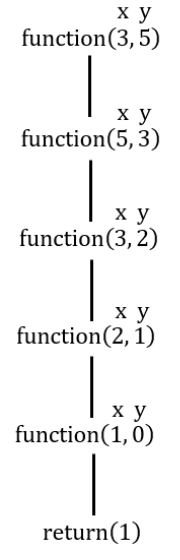
int function (int x, int y)
{
if(y<=0) return x;
return function (y, x%y);
}
The above recursive function computes ______
GCD of X and Y
| |
xy | |
yx | |
HCF of x and y | |
Both A and D |
Question 5 |
The working set model is used in memory management to implement the concept of:
Principle of locality
| |
Thrashing
| |
Paging
| |
Segmentation
|
Or
The working set is the memory that's being accessed "frequently" by an application or set of applications.
Principle of Locality does the same thing as explained above.
In computer science, locality of reference, also known as the principle of locality, is the tendency of a processor to access the same set of memory locations repetitively over a short period of time.There are two basic types of reference locality – temporal and spatial locality. Temporal locality refers to the reuse of specific data, and/or resources, within a relatively small time duration. Spatial locality (also termed data locality) refers to the use of data elements within relatively close storage locations.
Question 6 |
Depth first search graph search algorithm uses ____ data structure for its implementation.
Stack
| |
Tree | |
Dequeue
| |
Queue |
Whereas Breadth first search algorithm uses queue data structure for its implementation.
Question 7 |
In RSA
1. P and Q are chosen as very large prime number
2. Compute n = p*q and Φ(n) = (n-1)*(q-1)
Letter e encryption key chosen. How is this encryption key selected?
e is chosen as a relative prime to q
| |
e is chosen as a relative prime to p | |
e is chosen as a relative prime to Φ(n)
| |
e is chosen as a relative prime to n
|
e*d = 1 mod Φ(n), where e is encryption key and d is decryption key.
Question 8 |
Consider the following problem X
"Given a Turing Machine M over the input alphabet Σ any state q of M and word Σ*, does the computation of M on w visit the state q"
X is undecidable but partially decidable
| |
X is not a decision problem
| |
X is decidable
| |
X is undecidable but not even partially decidable
|
Question 9 |
The expression for commutative law is given by:
A+AB=A
| |
A+AB=B
| |
A+B=B+A | |
AB+AA'=A
|
A op B = B op A
Where op is any operator.
Hence A+B = B+A
Question 10 |
Consider the following grammar
S → m | mn | mnoChoose correct statement from the following:
The grammar is LL(4)
| |
The grammar is LL(3) | |
The grammar is LL(2) | |
The grammar is LL(1)
|
Intersection of second() of second and third production of S is ‘n’ which is not equal to {empty}, so not LL(2).
Intersection of third() of any two production of S is equal to {empty}, so yes LL(3).
Question 11 |
Consider the classful addressing, the IP address 128.252.144.84 denotes:
0.0.0.0 as network ID and 128.252.252.84 as node ID | |
128.0.0.0 as network ID and 128.252.127.84 as node ID | |
128.252.144.0 as network ID and 128.252.144.84 as node ID
| |
128.252.0.0 as network ID and 128.252.144.84 as node ID
|
So the Network ID of given IP address will be 128.252.0.0. And the node ID will be the same as the given IP address which is 128.252.144.84.
Question 12 |
Consider the following statement.
I. Packet filter firewall analyzes network traffic at transport layer.
II. Circuit level firewall operate transport and session layer of OSI model.
From the above statement which statement/s is/are TRUE?
Only I | |
Only II | |
None | |
I and II
|
A circuit-level gateway is a type of firewall. Circuit-level gateways work at the session layer of the OSI model, or as a "shim-layer" between the application layer and the transport layer of the TCP/IP stack. They monitor TCP handshaking between packets to determine whether a requested session is legitimate.
Question 13 |
___ is not a public key cryptosystem
EI Gemal
| |
Rabin | |
AES | |
RSA
|
Like all asymmetric cryptosystems, the Rabin system uses a key pair: a public key for encryption and a private key for decryption. The public key is published for anyone to use, while the private key remains known only to the recipient of the message.
AES is a symmetric key cryptosystem or private key encryption.
RSA is one of the first public-key cryptosystems and is widely used for secure data transmission. In such a cryptosystem, the encryption key is public and distinct from the decryption key which is kept secret.
Question 14 |
Consider the FA shown in fig below which language is accepted by the FA:
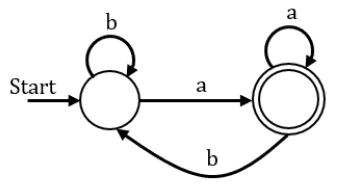
(a+b)*a | |
b+(a+b)*b | |
b+a*b* | |
b+a*b
|
Option C - ‘b’ is generated which is not accepted by the given FA.
Option D- ‘b’ is generated which is not accepted by the given FA.
Option A- All the strings generated by regular expression are accepted by the given FA.
Moreover we can clearly see that given automata accepts all the strings which ends with ‘a’. And regular expression in option A generates all such strings.
Question 15 |
Generation of intermediate code based on an abstract machine model is useful in compilers because:
It makes implementation of lexical and syntax analysis easier | |
It is difficult to generate executable code from high level language program
| |
Syntax translations are easier for intermediate code generation
| |
It enhances the portability of the compiler system program |
Question 16 |
The maximum height of a binary tree with 'n' nodes is ____
(n+n) | |
(n+1)
| |
n | |
(n-1)
|
Question 17 |
In hashing, collision resolution is carried out by close addressing. Which of the following is close addressing technique-
I. Bucket (for contiguous storage)
II. Chains (for linked storage)
Only I | |
Only II
| |
I and II
| |
None |
Hence Chains use close addressing whereas bucket uses open addressing.
Question 18 |
The main memory of a computer has 2cm blocks while the cache has 2c blocks. If cache uses set associative mapping scheme with two blocks per set, then the block k of the main memory maps to set:
(k mod m) of the cache
| |
(k mod c) of the cache | |
(k mod 2c) of the cache
| |
(k mod 2cm) of the cache
|
Therefore the kth block of main memory maps to k mod c of the cache.
Question 19 |
Consider the following two statements.
1. A binary tree T is full if each node is either a leaf or possesses exactly two child nodes.
2. A binary tree with n levels is complete if all levels except possibly the last are completely full, and the last level has all its nodes to the left side.
Which statement is/are TRUE?
Only 2 | |
Only 1 | |
1 and 2
| |
Neither 1 nor 2
|
S2 is true. The given definition of complete binary tree is correct.
Question 20 |
Consider the Unix i-node which uses 12 direct DBAs, 1 single indirect, 1 double indirect, 1 triple indirect. The disk block address requires 32 bits and disk block size is 1 KB. What is the maximum file size?
32 GB | |
64 GB | |
16 GB
| |
8 GB
|
No. of addresses that can fit in one block = size of block/size of address = 210B/22B = 28
∴ The maximum file size,
= (Direct address + 1 single indirect + 1 double indirect + 1 triple indirect) × Block size
= (12 + 28 + 28 × 28 + 28 × 28 × 28) × 210
≌ 234 = 16GB
Question 21 |
A trigger has three parts.
The ____ describes the change that activates the trigger.
The _____ is a query that is run whenever the trigger is activated.
The ___ is the procedure that is executable if the trigger is activated and the condition is true.
event, condition, actor
| |
entity, condition, action | |
event, question, action | |
event, condition, action |
The condition is a query that is run whenever the trigger is activated.
The action is the procedure that is executable if the trigger is activated and the condition is true.
Question 22 |
Which layer is associated with log in and log out from the network?
Presentation | |
Transport | |
Data link | |
Session
|
Question 23 |
Digital certificates are described using ____ format.
X.509
| |
X.510 | |
X.508 | |
X.409 |
Question 24 |
___ command is used to enable, disable, modify or drop a constraint in SQL
MODIFY Table
| |
DEFINE Table
| |
ADD Column | |
ALTER Table
|
Question 25 |
Which is equivalent CFG without useless symbols for the given grammar:
S → PQ | p, P → p
S → PQ | |
S → p | |
S → P, P → p | |
S → P | p, P → p |
Since Q does not derive any string, hence the productions related to it will be removed. Now the productions remaining,
S → p
P → p
Now we can see that P is not reachable from the starting symbol S hence the productions related to P will be removed. So finally the answer will become,
S → p
